Search the audit log for events in Microsoft Defender XDR
Applies to:
The audit log can help you investigate specific activities across Microsoft 365 services. In the Microsoft Defender XDR portal, Microsoft Defender XDR and Microsoft Defender for Endpoint activities are audited. Some of the activities audited are:
- Changes to data retention settings
- Changes to advanced features
- Creation of indicators of compromise
- Isolation of devices
- Add\edit\deletion of security roles
- Create\edit custom detection rules
- Assign user to an incidents
For a complete list of Microsoft Defender XDR activities that are audited, see Microsoft Defender XDR activities and Microsoft Defender for Endpoint activities.
Requirements
To access the audit log, you need to have the View-Only Audit Logs or Audit Logs role in Exchange Online. By default, those roles are assigned to the Compliance Management and Organization Management role groups.
Note
Global administrators in Office 365 and Microsoft 365 are automatically added as members of the Organization Management role group in Exchange Online.
Turn on auditing in Microsoft Defender XDR
Microsoft Defender XDR uses the Microsoft Purview auditing solution, before you can look at the audit data in the Microsoft Defender XDR portal:
You should confirm that auditing is turned on in the Microsoft Purview compliance portal. For more information, see Turn auditing on or off.
Follow the steps below to enable the unified audit log in the Microsoft Defender XDR portal:
- Log in to Microsoft Defender XDR using an account with the Security administrator or Global administrator role assigned.
- In the navigation pane, select Settings > Endpoints > Advanced features.
- Scroll own to Unified audit log and toggle the setting to On.
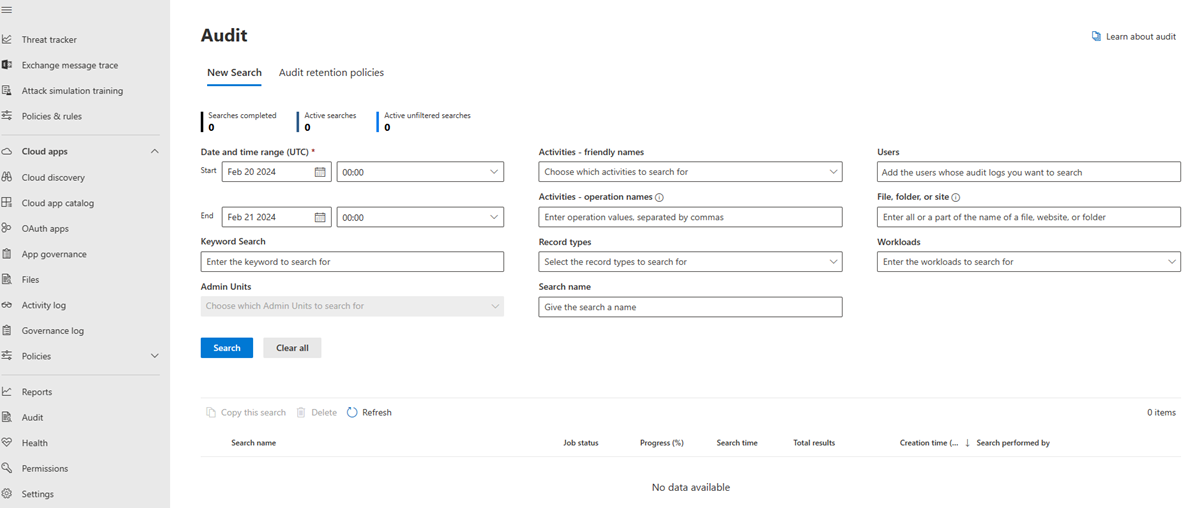
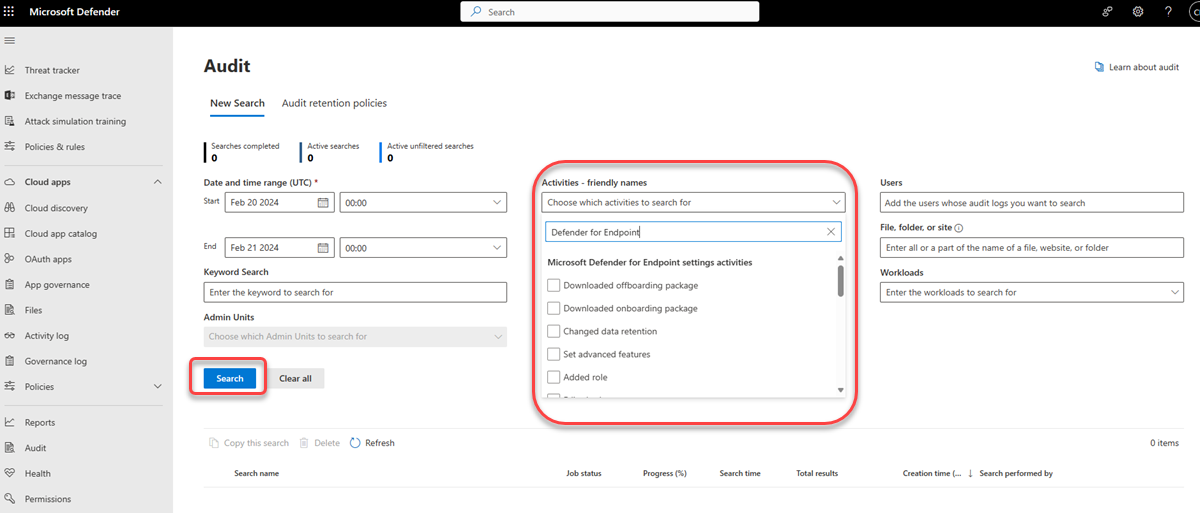
Using the audit search in Microsoft Defender XDR
To retrieve audit logs for Microsoft Defender XDR activities, navigate to the Microsoft Defender XDR Audit page or go to the Purview compliance portal and select Audit.
On the New Search page, filter the activities, dates, and users you want to audit.
Select Search
Export your results to Excel for further analysis.
For step-by-step instructions, see Search the audit log in the compliance portal.
Audit log record retention is based on Microsoft Purview retention policies. For more information, see Manage audit log retention policies.
Microsoft Defender XDR activities
For a list of all events that are logged for user and admin activities in Microsoft Defender XDR in the Microsoft 365 audit log, see:
- Custom detection activities in Microsoft Defender XDR in the audit log
- Incident activities in Microsoft Defender XDR in the audit log
- Suppression rule activities in Microsoft Defender XDR in the audit log
Microsoft Defender for Endpoint activities
For a list of all events that are logged for user and admin activities in Microsoft Defender for Endpoint in the Microsoft 365 audit log, see:
- General settings activities in Defender for Endpoint in the audit log
- Indicator settings activities in Defender for Endpoint in the audit log
- Response action activities in Defender for Endpoint in the audit log
- Roles settings activities in Defender for Endpoint in the audit log
Using a PowerShell script
You can use the following PowerShell code snippet to query the Office 365 Management API to retrieve information about Microsoft Defender XDR events:
$cred = Get-Credential
$s = New-PSSession -ConfigurationName microsoft.exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $cred -Authentication Basic -AllowRedirection
Import-PSSession $s
Search-UnifiedAuditLog -StartDate 2023/03/12 -EndDate 2023/03/20 -RecordType <ID>
Note
See the API column in Audit activities included for the record type values.
Additional resources
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for