Deploy cloud connected HoloLens 2 to external clients
This guide is a supplement to the Cloud Connected Deployment Guide. It's used in situations where your organization wants to ship HoloLens 2 devices to an external client's facility for short or long-term use. The external client will log into the HoloLens 2 device using credentials provided by your organization, and use Remote Assist to contact your experts. This guide provides general HoloLens 2 deployment recommendations that are applicable to most external HoloLens 2 deployment scenarios and common concerns that customers have when deploying Remote Assist for external use.
Prerequisites
The following infrastructure should be in place per the Cloud Connected Deployment Guide to deploy the HoloLens 2 externally.
- Microsoft Entra join with MDM Auto Enrollment—MDM-managed (Intune)
- Users sign in with their own corporate account (Microsoft Entra ID)
- Single or multiple users per device are supported.
Remote Assist licensing and requirements
- Microsoft Entra account (required for purchasing the subscription and assigning licenses)
- Remote Assist subscription (or Remote Assist Trial)
See Learn more about Remote Assist.
Dynamics 365 Remote Assist user
- Remote Assist license
- Network Connectivity
Microsoft Teams user
- Microsoft Teams or Teams Freemium
- Network connectivity
General deployment recommendations
We recommend the following steps for external HoloLens 2 deployment:
Use the latest HoloLens OS release as your baseline build.
Assign user-based or device-based licenses by following the steps below:
- Create a group in Microsoft Entra ID and add members for HoloLens/RA users.
- Assign device-based or user-based licenses to this group.
- (Optional) Target groups for Mobile device management (MDM) policies.
Join Microsoft Entra devices to your tenant, auto enroll, and configure through Autopilot. For more information, see device owner.
- The first user on the device will be the device owner.
- If the device is Microsoft Entra joined, the user that performed the join is made device owner.
Tenant lock the device so that it can only be joined by your tenant.
- See also Tenant lock CSP.
Disable the following (optional) capabilities:
- Ability to put the device into developer mode here.
- Ability to connect the HoloLens to a PC to copy date disable USB.
Note
If you don’t want to disable USB but want the ability to apply a provisioning package to the device using USB, follow the instructions on how to allow provisioning package installation.
Use Windows Defender Application Control (WDAC) to allow or block apps on the HoloLens 2 device.
Update Remote Assist to the latest version as part of the setup. Consider the following two options:
- Go to Windows Microsoft Store --> Remote Assist --> and Update App.
- ApplicationManagement/AllowAppStoreAutoUpdate - which allows automatic app updates - is enabled by default. Keep the device plugged in to receive updates.
Disable all settings pages except the network settings to allow users to connect to guest networks at client sites.
-
- Option to control OS updates or allow to flow freely.
Now your external clients are ready to use their HoloLens 2.
Common external client deployment concerns
- Ensuring clients can't communicate with one another
- Ensuring clients can't access company resources
- Hiding or restricting apps
- Managing passwords for your clients
- Ensuring clients can't access chat history
Ensure that external clients can't communicate with one another
Remote Assist HoloLens to HoloLens calls aren't supported. Clients can search for, but can't communicate with each other. Information barriers in Microsoft 365 can further restrict with whom a client can search and call. Another option is to use Microsoft Teams scoped directory search.
Note
Since single sign on is enabled, it is important to disable the browser using Windows Defender Application Control (WDAC). If an external client opens the browser and uses the web version of Teams, the client will have access to your chat history.
Ensure that clients won't have access to company resources
There are two options to consider.
The first option is a multi-layer approach:
- Only assign licenses that the user requires. If you don't assign OneDrive, Outlook, SharePoint, Yammer, etc., the user will not have access to those resources. The only licenses the users will need is Remote Assist, Intune, and Microsoft Entra ID licenses to begin.
- Block apps (such as email) that you don’t want clients to access (See [Apps are hidden or restricted](#apps are hidden or restricted)).
- Don't share usernames nor password with clients. To log into the HoloLens 2, an email and numerical PIN is required.
The second option is to create a separate tenant that hosts clients (see Image 1.1).
Image 1.1
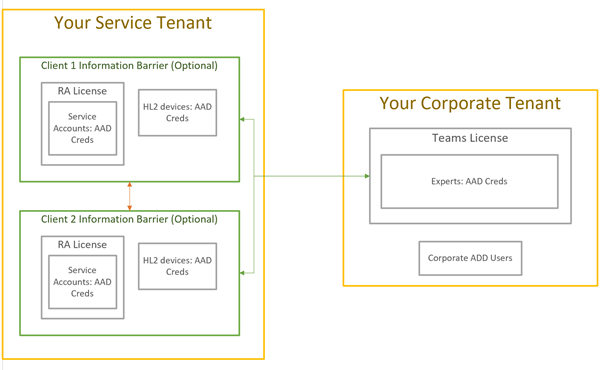
Hidden or restricted apps
Kiosk mode and/or Windows Defender Application Control (WDAC) are options for hiding and/or restricting applications.
Password management for your clients
- Remove password expiration. However, this option may increase the chance that an account will be compromised. NIST password recommendation is change passwords every 30-90 days.
- Extend the password expiration for HoloLens 2 devices to exceed 90 days.
- The devices should be returned to your organization to change the passwords. However, this option can cause issues if the devices are expected to be in the client's plant for 90+ days.
- For devices that are sent to multiple clients, reset passwords before shipping the device to clients.
Ensure that clients won't have access to chat history
Remote Assist clears chat history after each session. However, chat history will be available for Microsoft Teams users.
Note
Since single sign on is enabled, it is important to disable the browser using Windows Defender Application Control (WDAC). If a external client opens the browser and uses the web version of Teams, the client will have access to call/chat history.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for