Local Administrator Password Solution
The "Local Administrator Password Solution" (LAPS) provides a centralized storage of secrets/passwords in Active Directory (AD) - without additional computers. Each organization’s domain administrators determine which users, such as helpdesk admins, are authorized to read the passwords.
For occasions when login is required without domain credentials, password management can become complex. LAPS simplifies password management while helping customers implement recommended defenses against cyberattacks. In particular, it mitigates the risk of lateral escalation that results when customers have the same administrative local account and password combination on many computers.
Why use LAPS instead of other password managers/vaults?
Other password managers typically require either, additional hardware (IIS/SQL), trusting a third party, or ad hoc practices (Excel spreadsheet of passwords = huge security hole).
LAPS provides a streamlined approach to:
- Periodically randomizing local administrator passwords - ensures password update to AD succeeds before modifying local secrets/passwords
- Centrally store secrets in existing infrastructure - Active Directory (AD)
- Control access via AD ACL permissions
- Transmit encrypted passwords from client to AD (using Kerberos encryption, AES cypher by default)
Components
- Agent - Group Policy Client Side Extension (CSE) - installed via MSI
- Event logging
- Random password generation - written from client computer to AD computer object
- PowerShell module
- Active Directory - centralized control
- Audit trail in security log of domain controller
- Computer object, confidential attribute
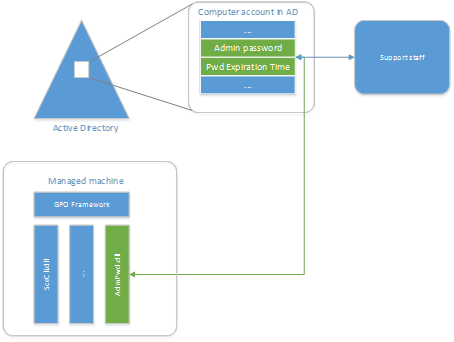
Solution automatically manages the .500 (local administrator) password on domain joined computers, so the password is:
- Unique on each managed computer
- Randomly generated
- Stored in existing AD infrastructure
Solution is built upon AD infrastructure, so there is no need to install and support other technologies.
Solution itself is a Group Policy Client Side Extension that is installed on managed machines and performs all management tasks
Management tools delivered with the solution allow for easy configuration and administration.
Core of the solution is GPO Client side Extension (CSE) that performs the following tasks during GPO update:
- Checks whether the password of local Administrator account has expired or not
- Generates the new password when old password expired or is required to be changed prior to expiration
- Changes the password of Administrator account
- Reports the password to password Active Directory, storing it in confidential attribute with computer account in AD/li>
- Reports the next expiration time to Active Directory, storing it in confidential attribute with computer account in AD
- Password then can be read from AD by users who are allowed to do so
- Password can be forced to be changed by eligible users
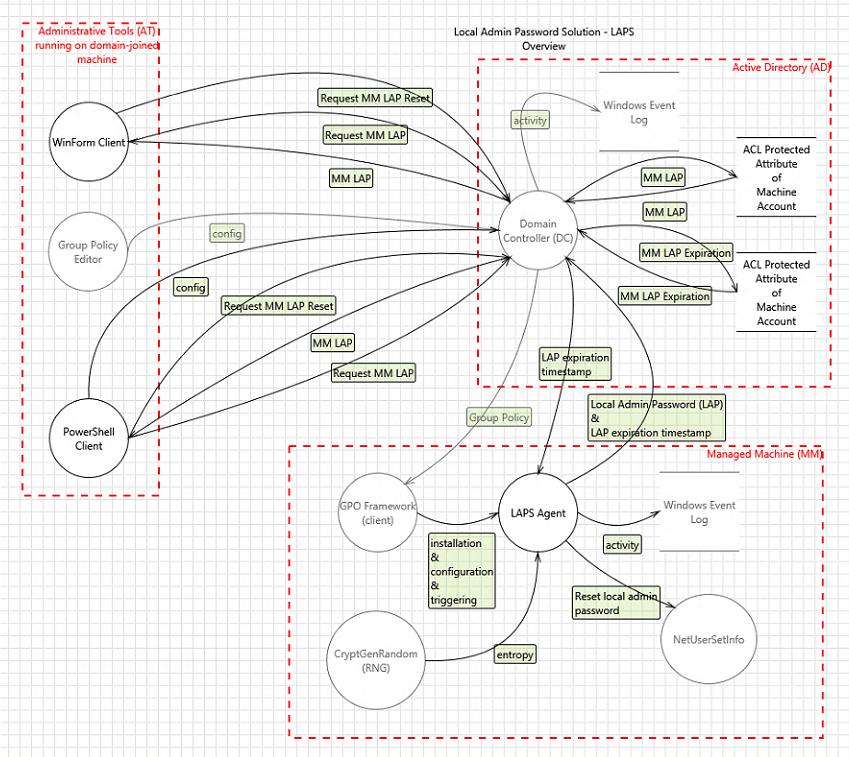
Security
- Random password that automatically regularly changes on managed machines
- Effective mitigation of Pass-the-hash attack
- Password is protected during the transport via Kerberos encryption
- Password is protected in AD by AD ACL, so granular security model can be easily implemented
Manageability
- Configurable password parameters: age, complexity and length
- Ability to force password reset on per-machine basis
- Security model integrated with AD ACLs
- End use UI can be any AD management tools of choice, plus custom tools (PowerShell and Fat client) are provided
- Protection against computer account deletion
- Easy implementation and minimal footprint
Requirements
- Active Directory:
- Windows 2003 SP1 and above
- Managed/Client machines:
- Windows Server 2016
- x86 or x64
- Windows Server 2012 R2 Datacenter
- Windows Server 2012 R2 Standard
- Windows Server 2012 R2 Essentials
- Windows Server 2012 R2 Foundation
- Windows 8.1 Enterprise
- Windows 8.1 Pro
- Windows Server 2012 Datacenter
- Windows Server 2012 Standard
- Windows Server 2012 Essentials
- Windows Server 2012 Foundation
- Windows 8 Enterprise
- Windows 8 Pro
- Windows Server 2008 R2 Service Pack 1
- Windows 7 Service Pack 1
- Windows Server 2008 Service Pack 2
- Windows Vista Service Pack 2
- Microsoft Windows Server 2003 Service Pack 2
- Itanium NOT supported
- Management tools:
- .NET Framework 4.0
- PowerShell 2.0 or above
FAQs
Where can I download LAPS?
You can download the tool from the download center here.
Is LAPS officially supported?
LAPS customer support is available through Microsoft Premier Support Services.
Where can I see further details, architectural diagrams and granular installation instructions?
See the documentation via LAPS download link
Where can I find installation instructions?
See the documentation via LAPS download link
Are there any known compatibility issues?
Yes. Administrator password management via Group Policy Preferences (GPP) collides with LAPS, event after hotfix MS014-025 installed. Management of administrator account password needs to be removed from GPP prior installing LAPS
What is new in 6.1 version?
- PowerShell: Customers want to run Find-AdmPwdExtendedRights before extending AD schema. Added switch that allows it
- Powershell: content bug in help for Powershell
- LAPS UI: Replaced text box for password expiration with datetime picker
- Documentation: Updated docs (printscreens and info about loading LAPS module into PS 2.0)
- Admin tools: Fixed issue when computer account may not be found in forest with multiple domain trees
What is new in 6.2 version?
- Support for localized local Administrators group name on localized OS builds when using setup parameter CUSTOMADMINNAME – you no longer need to create MST files for OS builds where name of Administrators group is localized to be able to create custom admin account during installation
- Fix of bug “Format of path is invalid” in LAPS UI and PowerShell on Windows 10 Anniversary update and Windows Server 2016, when reading and resetting the password
- Fix of bug when some long error messages not shown in status bar of LAPS UI client
- Font for password field in LAPS UI changed to Courier 12 for better readability of passwords.

