What is Azure Bastion?
Azure Bastion is a fully managed PaaS service that you provision to securely connect to virtual machines via private IP address. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly over TLS from the Azure portal, or via the native SSH or RDP client already installed on your local computer. When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software.
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network for which it's provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
Key benefits
| Benefit | Description |
|---|---|
| RDP and SSH through the Azure portal | You can get to the RDP and SSH session directly in the Azure portal using a single-click seamless experience. |
| Remote Session over TLS and firewall traversal for RDP/SSH | Azure Bastion uses an HTML5 based web client that is automatically streamed to your local device. Your RDP/SSH session is over TLS on port 443. This enables the traffic to traverse firewalls more securely. Bastion supports TLS 1.2. Older TLS versions aren't supported. |
| No Public IP address required on the Azure VM | Azure Bastion opens the RDP/SSH connection to your Azure VM by using the private IP address on your VM. You don't need a public IP address on your virtual machine. |
| No hassle of managing Network Security Groups (NSGs) | You don't need to apply any NSGs to the Azure Bastion subnet. Because Azure Bastion connects to your virtual machines over private IP, you can configure your NSGs to allow RDP/SSH from Azure Bastion only. This removes the hassle of managing NSGs each time you need to securely connect to your virtual machines. For more information about NSGs, see Network Security Groups. |
| No need to manage a separate bastion host on a VM | Azure Bastion is a fully managed platform PaaS service from Azure that is hardened internally to provide you secure RDP/SSH connectivity. |
| Protection against port scanning | Your VMs are protected against port scanning by rogue and malicious users because you don't need to expose the VMs to the internet. |
| Hardening in one place only | Azure Bastion sits at the perimeter of your virtual network, so you don’t need to worry about hardening each of the VMs in your virtual network. |
| Protection against zero-day exploits | The Azure platform protects against zero-day exploits by keeping the Azure Bastion hardened and always up to date for you. |
SKUs
Azure Bastion offers multiple SKU tiers. The following table shows features and corresponding SKUs.
| Feature | Developer SKU | Basic SKU | Standard SKU |
|---|---|---|---|
| Connect to target VMs in same virtual network | Yes | Yes | Yes |
| Connect to target VMs in peered virtual networks | No | Yes | Yes |
| Support for concurrent connections | No | Yes | Yes |
| Access Linux VM Private Keys in Azure Key Vault (AKV) | No | Yes | Yes |
| Connect to Linux VM using SSH | Yes | Yes | Yes |
| Connect to Windows VM using RDP | Yes | Yes | Yes |
| Connect to Linux VM using RDP | No | No | Yes |
| Connect to Windows VM using SSH | No | No | Yes |
| Specify custom inbound port | No | No | Yes |
| Connect to VMs using Azure CLI | No | No | Yes |
| Host scaling | No | No | Yes |
| Upload or download files | No | No | Yes |
| Kerberos authentication | No | Yes | Yes |
| Shareable link | No | No | Yes |
| Connect to VMs via IP address | No | No | Yes |
| VM audio output | Yes | Yes | Yes |
| Disable copy/paste (web-based clients) | No | No | Yes |
For more information about SKUs, including how to upgrade a SKU and information about the new Developer SKU (currently in Preview), see the Configuration settings article.
Architecture
Azure Bastion offers multiple deployment architectures, depending on the selected SKU and option configurations. For most SKUs, Bastion is deployed to a virtual network and supports virtual network peering. Specifically, Azure Bastion manages RDP/SSH connectivity to VMs created in the local or peered virtual networks.
RDP and SSH are some of the fundamental means through which you can connect to your workloads running in Azure. Exposing RDP/SSH ports over the Internet isn't desired and is seen as a significant threat surface. This is often due to protocol vulnerabilities. To contain this threat surface, you can deploy bastion hosts (also known as jump-servers) at the public side of your perimeter network. Bastion host servers are designed and configured to withstand attacks. Bastion servers also provide RDP and SSH connectivity to the workloads sitting behind the bastion, as well as further inside the network.
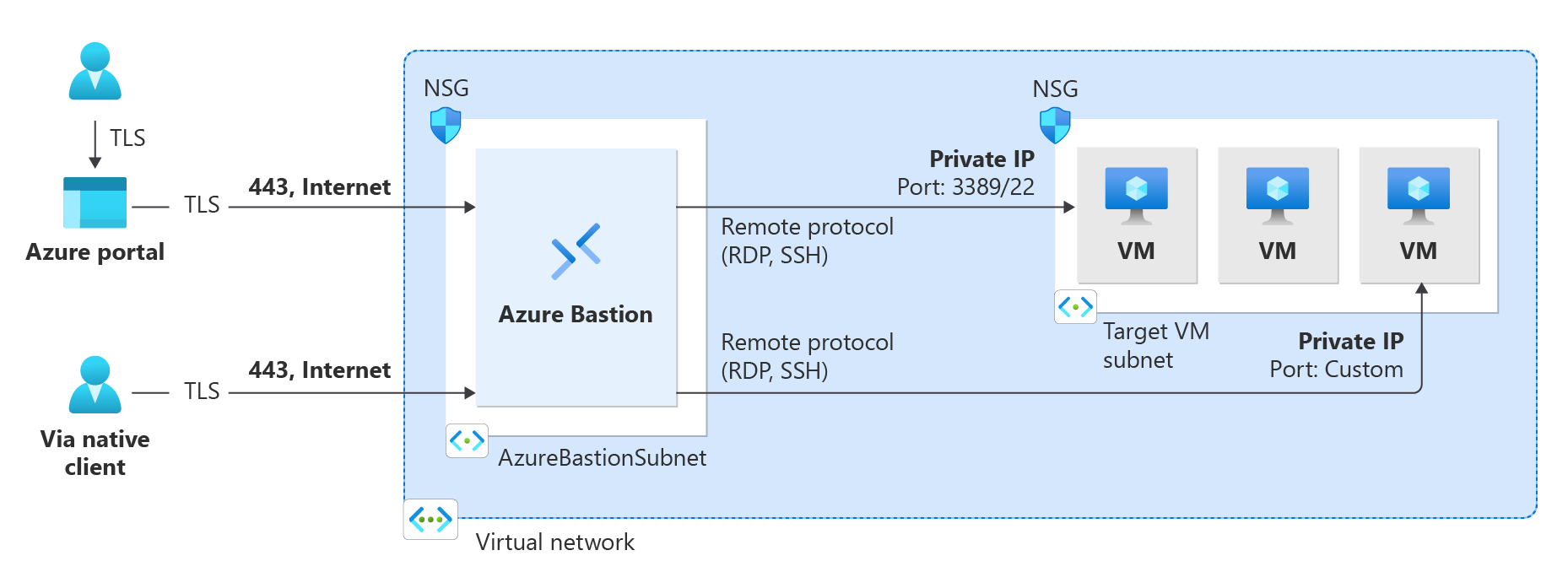
Diagram: Bastion - Basic SKU and higher
- The Bastion host is deployed in the virtual network that contains the AzureBastionSubnet subnet that has a minimum /26 prefix.
- The user connects to the Azure portal using any HTML5 browser.
- The user selects the virtual machine to connect to.
- With a single click, the RDP/SSH session opens in the browser.
- For some configurations, the user can connect to the virtual machine via the native operating system client.
- No public IP is required on the Azure VM.
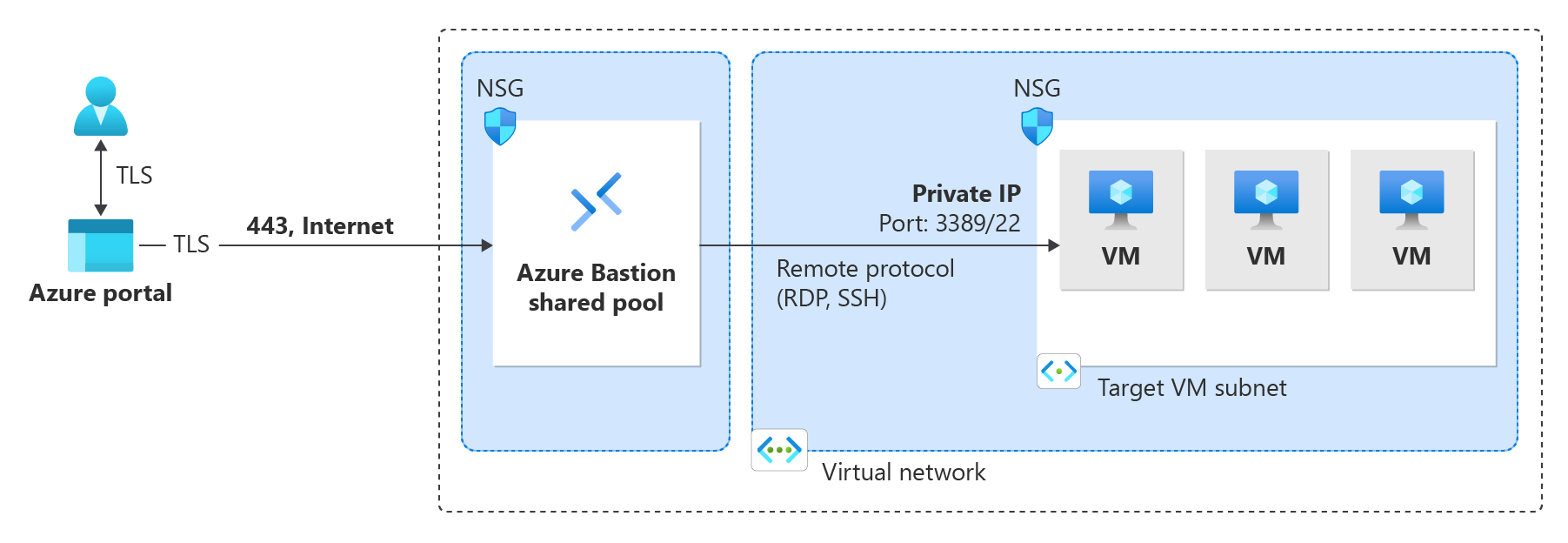
Diagram: Bastion - Developer SKU
The Bastion Developer SKU is a free, lightweight SKU. This SKU is ideal for Dev/Test users who want to securely connect to their VMs, but don't need additional Bastion features or host scaling. With the Developer SKU, you can connect to one Azure VM at a time directly through the virtual machine connect page.
When you deploy Bastion using the Developer SKU, the deployment requirements are different than when you deploy using other SKUs. Typically when you create a bastion host, a host is deployed to the AzureBastionSubnet in your virtual network. The Bastion host is dedicated for your use. When you use the Developer SKU, a bastion host isn't deployed to your virtual network and you don't need an AzureBastionSubnet. However, the Developer SKU bastion host isn't a dedicated resource. Instead, it's part of a shared pool.
Because the Developer SKU bastion resource isn't dedicated, the features for the Developer SKU are limited. See the Bastion configuration settings SKU section for features by SKU. You can always upgrade the Developer SKU to a higher SKU if you need to support more features. See Upgrade a SKU.
Availability zones
Some regions support the ability to deploy Azure Bastion in an availability zone (or multiple, for zone redundancy). To deploy zonally, deploy Bastion using manually specified settings (don't deploy using the automatic default settings). Specify the desired availability zones at the time of deployment. You can't change zonal availability after Bastion is deployed.
Support for Availability Zones is currently in preview. During preview, the following regions are available:
- East US
- Australia East
- East US 2
- Central US
- Qatar Central
- South Africa North
- West Europe
- West US 2
- North Europe
- Sweden Central
- UK South
- Canada Central
Host scaling
Azure Bastion supports manual host scaling. You can configure the number of host instances (scale units) in order to manage the number of concurrent RDP/SSH connections that Azure Bastion can support. Increasing the number of host instances lets Azure Bastion manage more concurrent sessions. Decreasing the number of instances decreases the number of concurrent supported sessions. Azure Bastion supports up to 50 host instances. This feature is available for the Azure Bastion Standard SKU only.
For more information, see the Configuration settings article.
Pricing
Azure Bastion pricing is a combination of hourly pricing based on SKU and instances (scale units), plus data transfer rates. Hourly pricing starts from the moment Bastion is deployed, regardless of outbound data usage. For the latest pricing information, see the Azure Bastion pricing page.
What's new?
Subscribe to the RSS feed and view the latest Azure Bastion feature updates on the Azure Updates page.
Bastion FAQ
For frequently asked questions, see the Bastion FAQ.
Next steps
- Quickstart: Deploy Bastion automatically - Basic SKU
- Quickstart: Deploy Bastion automatically - Developer SKU
- Tutorial: Deploy Bastion using specified settings
- Learn module: Introduction to Azure Bastion
- Learn about some of the other key networking capabilities of Azure
- Learn more about Azure network security
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for