Hello @King Xi ,
Thank you for posting here.
From the link below, we can see, if we configure the following 3 group policy settings under GPO (Default Domain Policy).
1.Computer Configuration\Windows settings\security settings\local policies\audit policy\Audit Directory Service Access =>Audit Success and Failure
2.Computer Configuration\Windows settings\security settings\Advanced Audit Policy Configuration\Audit Policies\Object Access\Audit SAM =>Audit Success and Failure
3.Computer Configuration\Windows settings\security settings\Advanced Audit Policy Configuration\Audit Policies\Object Access\Audit Handle Manipulation => Audit Success and Failure
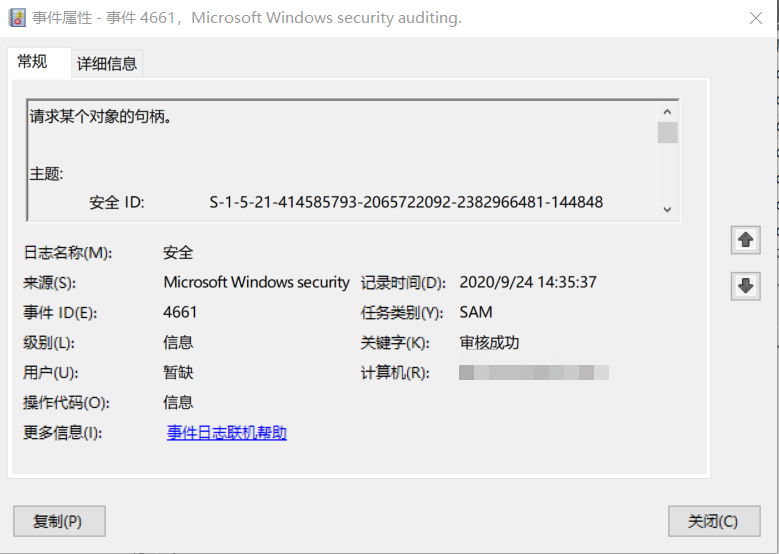
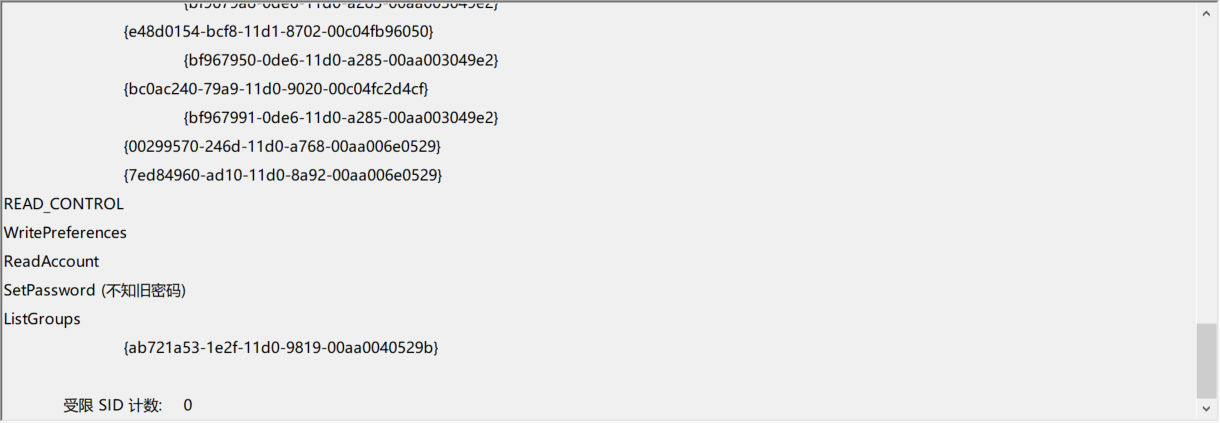
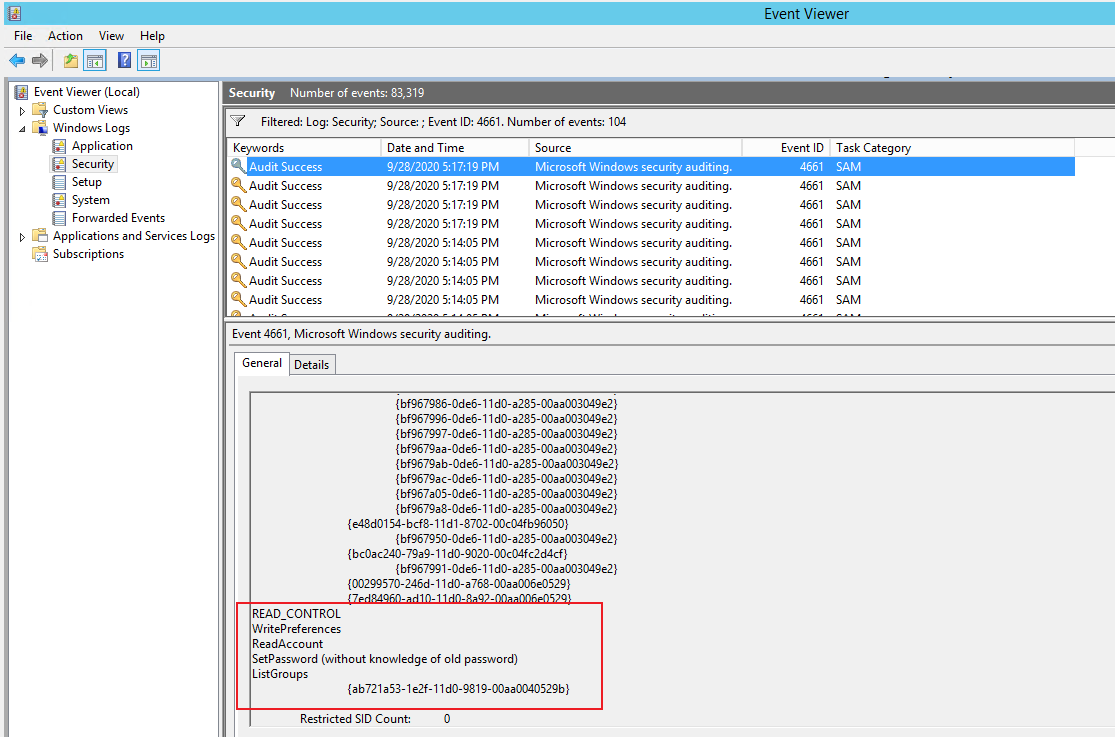
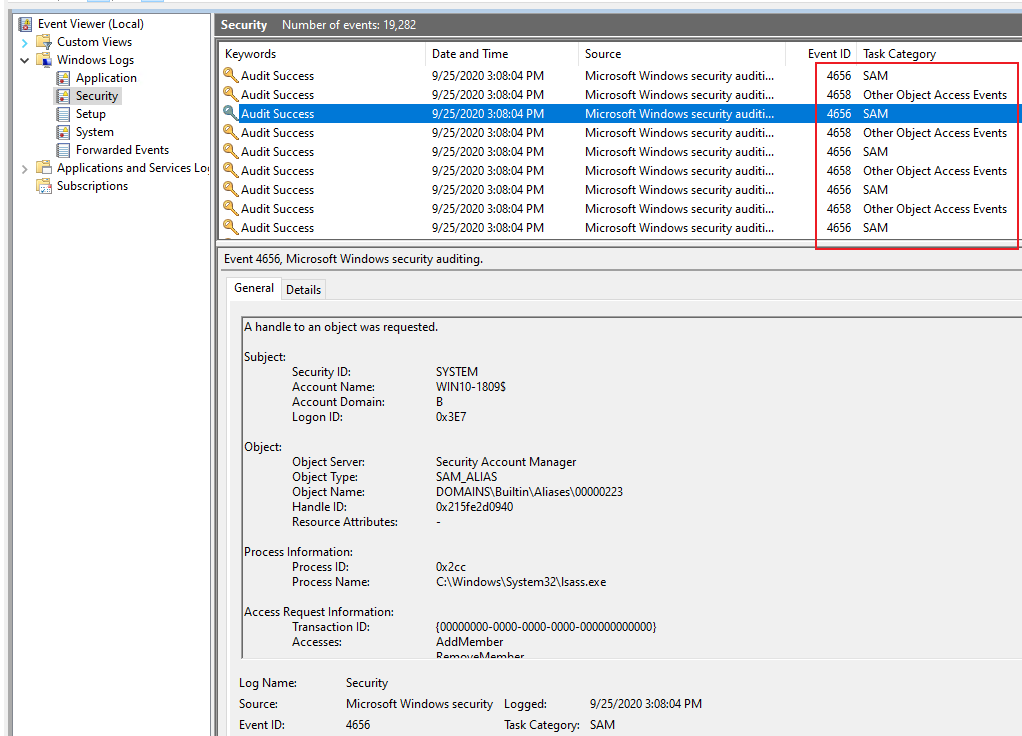
4661(S, F): A handle to an object was requested.
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4661
Then run the following commands on DCs and domain-joined clients.
gpupdate /force
auditpol /get /category:*
If we access C:\Windows\System32\config\SAM file, the event ID 4661 will be generate.
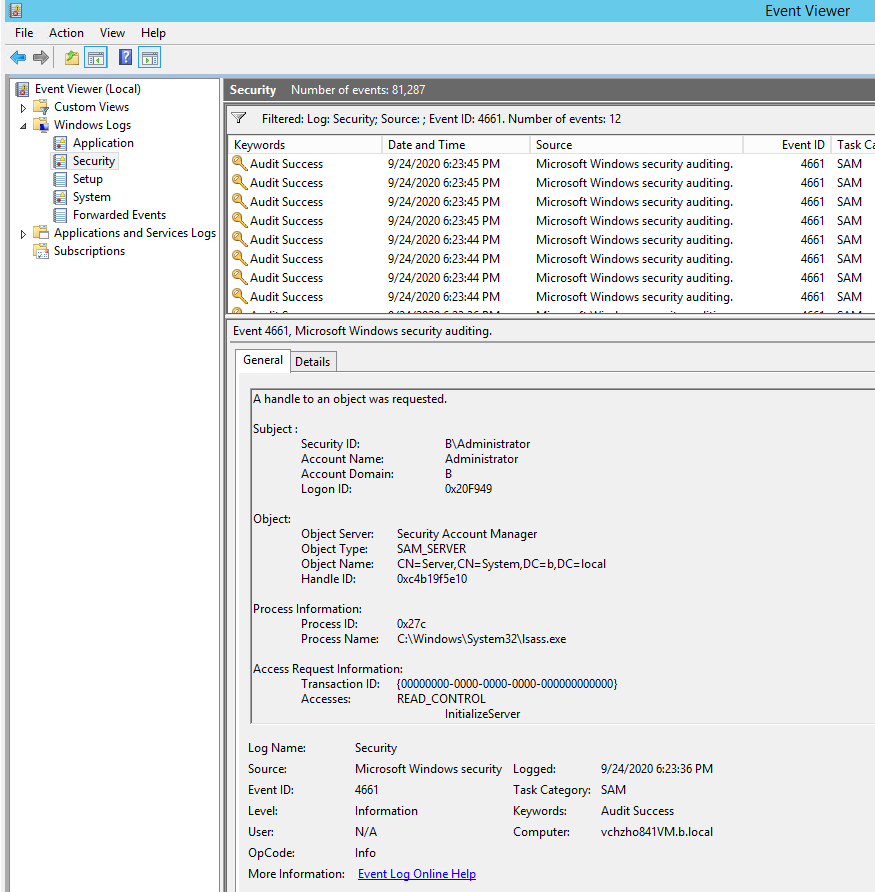
And about SAM, we can refer to the link below.
Security Account Manager
https://en.wikipedia.org/wiki/Security_Account_Manager
Hope the information above is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.