Hello,
Thank you so much for posting here.
To further narrow down the issue, we would like to get more detailed information. Would you please help to collect the following information:
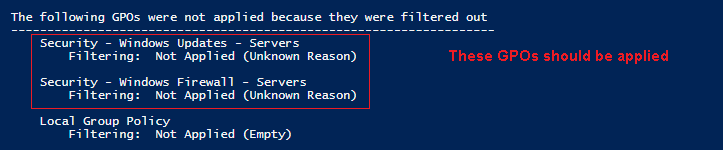
1: The not applied GPOs are under Computer Configuration, right?
2: If these GPOs are under Computer Configuration, are they linked to the OU with computer objects?
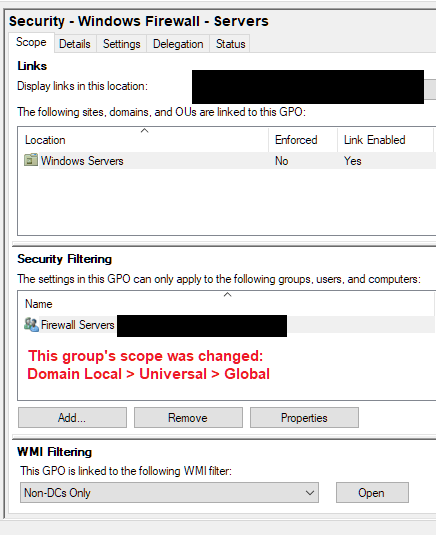
For Security Filtering, this Group Policy now applies to only users or computers that are a member of the security group. However you still need to remember that the user and/or computer should be part of the site/domain/OU to which this Group Policy Object is linked.
3: The not applied GPOs have custom security group added to the Security Filtering. Are users or computers added to this custom security group?
4: Where did we see error message? From gpresult?
5: We could have a check whether this security group has the Read and Apply Group Policy permission. Since we changed the security group scope, we could check whether the Read and Apply permission still exists.
For any question, please feel free to contact us.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.