@WMio Connectors , The following Admin consent page is coming up because of the following option set to "No" [Please refer to the screenshot]
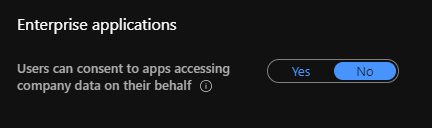
If this option is set to "No" normal users wont be able to provide user consent. If you want to go ahead with this option set to "No" and still want to Multitenant App to work, the only other option is to use the "Admin Consent Requests (Preview)" and set that to "Yes". Doing this, the normal user while accessing the app and entering the username and password, he/she would get the consent page and would ask the user to provide a justification for the Admin to approve. Once the admin approves it, the user would be able to access the app, and in the backend the app's service principal would get added to the user's tenant.
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.