You might have one of the below scenario. Follow the one which fits in your situation.
1. User Sign-in scenario
If your users sign-in using the AAD app, you can restrict that by leveraging "User Assignment" feature of Azure AD 'Enterprise Application' blade to restrict application to a set of users (or groups). For details, refer How to: Restrict your Azure AD app to a set of users in an Azure AD tenant.
- You need global admin role
- Enterprise Applications -> Your Application's Overview page -> Properties -> User assignment required? and set it to Yes
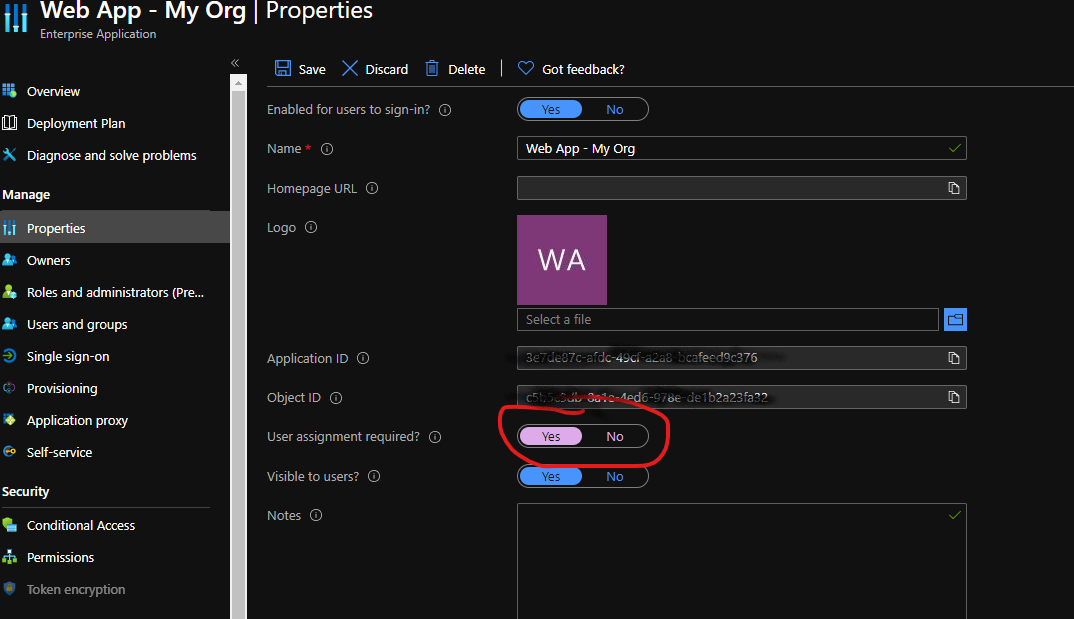
- Users and groups in app menu -> Add Assignment -> Select users/groups -> Assign
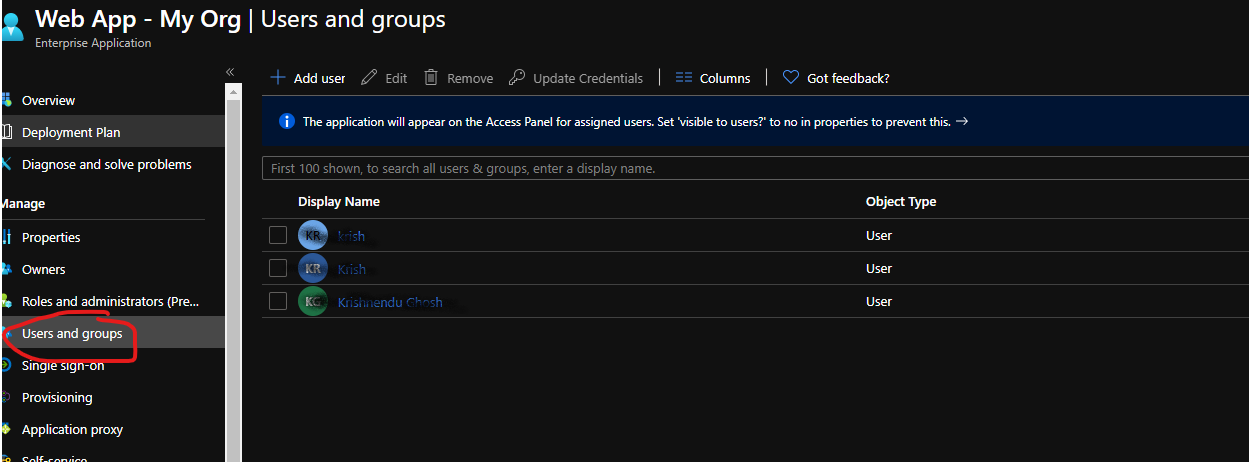
However you should keep in mind some limitation.
This feature is available for web app/web API and enterprise applications only. Apps that are registered as native cannot be restricted to a set of users or security groups in the tenant.
The option to restrict an app to a specific set of users or security groups in a tenant works with the following types of applications:
- Applications configured for federated single sign-on with SAML-based authentication
- Application proxy applications that use Azure AD pre-authentication
- Applications built directly on the Azure AD application platform that use OAuth 2.0/OpenID Connect authentication after a user or admin has consented to that application.
OR
2. Application identity scenario
If you are using app identity (client credential flow) to authenticate, you can restrict the app for only specific users by leveraging ApplicationAccessPolicy. For details, refer Scoping application permissions to specific Exchange Online mailboxes
- Connect to Exchange Online PowerShell. For details, see Connect to Exchange Online PowerShell. NOTE: Be aware of the prerequisites as it is supported in Windows only and Linux support is in preview whereas Mac is not supported yet.
- Identify the app’s client ID and a mail-enabled security group to restrict the app’s access to.
- Identify the app’s application (client) ID in the Azure app registration portal.
- Create a new mail-enabled security group (if not already created) or use an existing one and identify the email address for the group. NOTE: "mail-enabled security group" is not a regular AAD group. You can create it using Office365 Portal. Exchange ECP, or PowerShell. Refer Manage mail-enabled security groups
Run the following command New-DistributionGroup -Name "{name of the group}" -Alias "{alias}*" -Type security *Alias = This is the portion of the email address that appears to the left of the at (@) symbol. - Once your group is created, you can add/remove users to the group using Offce365 portal, Exchange ECP, Powershell or Graph API
- Create an application access policy.
Run the following command, replacing the AppId, PolicyScopeGroupId, and Description arguments. New-ApplicationAccessPolicy -AppId e7e4dbfc-046f-4074-9b3b-2ae8f144f59b -PolicyScopeGroupId EvenUsers@contoso.com -AccessRight RestrictAccess -Description "Restrict this app to members of distribution group EvenUsers." - Test the newly created application access policy.
Run the following command, replacing the AppId and Identity arguments. Test-ApplicationAccessPolicy -Identity user1@contoso.com -AppId e7e4dbfc-046-4074-9b3b-2ae8f144f59b The output of this command will indicate whether the app has access to User1’s mailbox.
Note: Changes to application access policies can take up to 30 minutes to take effect in Microsoft Graph REST API calls.

