Action Required for Attested Data TLS with Azure Instance Metadata Service

Hello Azure Customers in the community,
Microsoft is updating Azure services in a phased manner to use TLS certificates from a different set of Certificate Authorities (CAs). We expect that most Azure Instance Metadata Service Attested data customers will not be impacted. However, immediate action is required if you are impacted. Please read following carefully to determine the impact to you.
- Who will be impacted? If you explicitly specify a list of acceptable CAs (a practice known as “certificate pinning”) in Azure instance metadata service attested data,
you are impacted. - When did the TLS certificates change happen? It began August 13, 2020 and concluding approximately on December 1st 2020.
- What is the scope of the TLS certificates change? This change is limited to services in public Azure cloud and US Government cloud. There are no changes in other sovereign clouds like Azure
China. - Why did Azure make the TLS certificates change? This change is being made because the current CA certificates do not comply with one of the CA/Browser Forum Baseline requirements. This
was reported on July 1, 2020 and impacts multiple popular Public Key Infrastructure (PKI) providers worldwide. Today, most of the TLS
certificates used by Azure services are issued from the "Baltimore CyberTrust Root" PKI.
Azure Instance metadata service will remain chained to the Baltimore CyberTrust Root*, but the TLS server certificates will be issued by new
Intermediate Certificate Authorities (ICAs). Other Azure service TLS certificates may be issued by a different PKI If any client application has pinned to an Intermediate CA rather than the Baltimore CyberTrust Root, immediate action is required to
prevent disruption in the services which rely on Azure In stance metadata service. Determine the change in your code
The table below provides information about the certificates that are being rolled. Depending on which certificate your service uses for
establishing TLS connections, action may be needed to prevent loss of connectivity.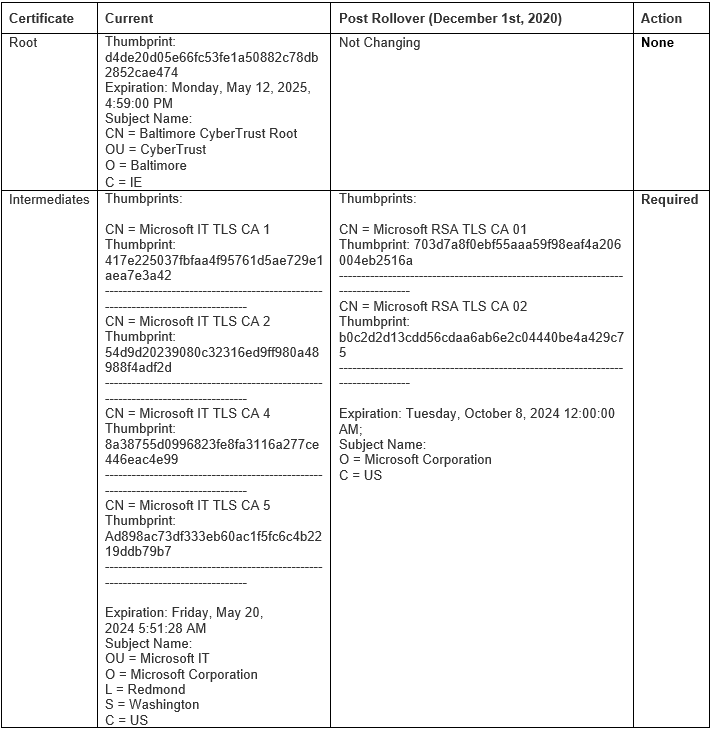 Note: Intermediate certificates are expected to change frequently. We recommend not taking dependencies on them and instead pinning the root certificate as it rolls less frequently.
Note: Intermediate certificates are expected to change frequently. We recommend not taking dependencies on them and instead pinning the root certificate as it rolls less frequently.
Action Required
- If your client application has pinned to an Intermediate CA listed in the table, then Search your source code for the thumbprint, Common Name, and other cert properties of any of the 4 Microsoft IT TLS CAs listed above. If there is a match, then your application will be impacted, immediate action is required: a. To resolve this problem, update the source code to include the new intermediate CAs. To continue pinning intermediaries, add the new intermediates CAs:
i. Microsoft RSA TLS CA 01
(Thumbprint: 703d7a8f0ebf55aaa59f98eaf4a206004eb2516a)
ii. Microsoft RSA TLS CA 02
(Thumbprint: b0c2d2d13cdd56cdaa6ab6e2c04440be4a429c75) Once you have made the changes above please validate to make make sure the attested data endpoint validation code of your feature continues to work.
Additional Information
Microsoft wide communications: To broadly notify customers, Microsoft had sent a Service Health portal notification on Aug 3rd, 2020 and released a public document that includes timelines, actions that need to be taken, and details regarding the upcoming changes to our Public Key Infrastructure (PKI).