Hi, I'm trying to create groups in AD B2C via the graph SDK. So far I've been able to create applications via the graph with no issues, but creating a group results in the following:
Microsoft.AspNetCore.Components.Server.Circuits.CircuitHost[111]
Unhandled exception in circuit 'qXQW3GHjtM5v-OhOsYi83lIbG67FlVsBhjS2AygCShY'.
Status Code: BadRequest
Microsoft.Graph.ServiceException: Code: NoLicenseForOperation
Message: Tenant does not have proper license.
Inner error:
AdditionalData:
date: 2020-12-16T23:06:47
request-id: 1330c157-48c4-4a95-ba62-7e7515a0588a
client-request-id: 1330c157-48c4-4a95-ba62-7e7515a0588a
ClientRequestId: 1330c157-48c4-4a95-ba62-7e7515a0588a
I've come across nothing in the documentation about license requirements for this operation - so is this user error, a bug in Azure or incomplete documentation? The code I'm using to create it is:
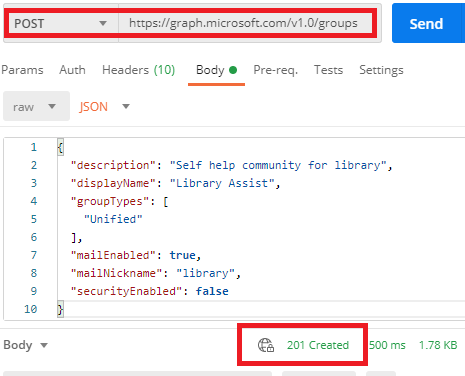
var toCreate = new Group
{
DisplayName = DisplayName(groupType, appName),
MailEnabled = false,
GroupTypes = new string[] { "Security" },
MailNickname = "",
MembershipRule = "Assigned"
};
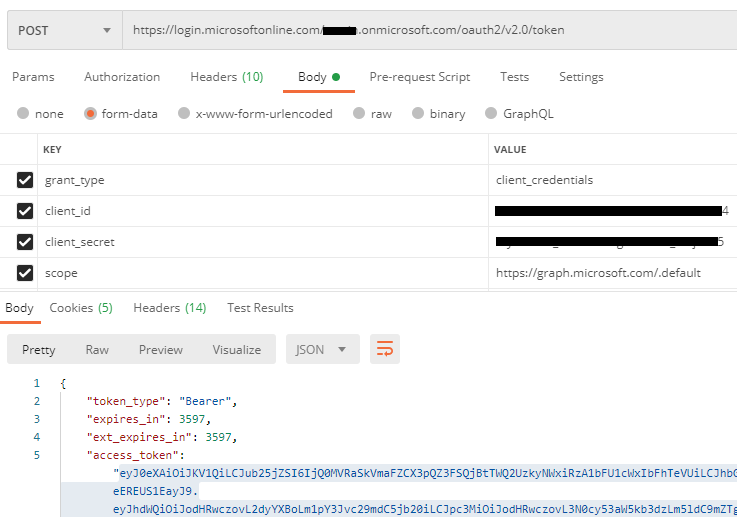
var result = await graph
.Groups
.Request()
.AddAsync(toCreate);
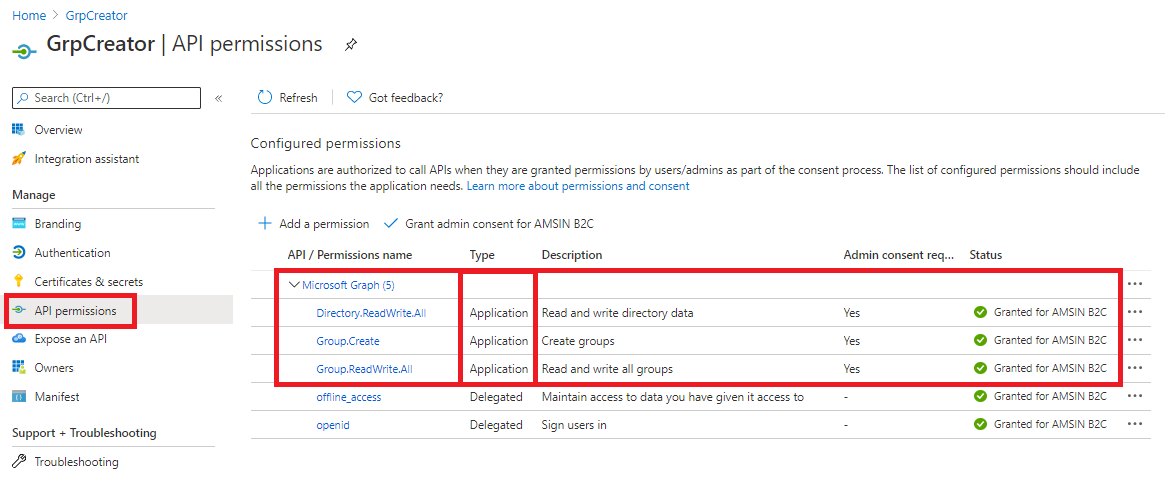
I'm using app based auth/delegation to connect to Graph - again, I've been able to create an Application with it just fine, so I'd have assumed that creating security groups to support it would require the same level of permissions - and yes, I've added Groups.Create to the list of API/Graph permissions used by my application.
Cheers,
Matt.
[UPDATE]
Talked to one of the oher devs here, and he was able to create groups via the graph SDK, but that was when he connected the app (still using app permissions, not user) to AD, not B2C. In fact, I just realised that if I want to create groups via the Azure Dashboard then I have to do it via the AD page; groups don't even show up in the B2C page.
So if this is the problem, is the solution to just have more than multiple ways of authenticating against azure for the app? The app itself needs B2C because that's what we're using to auth people, but I can create an AD connection as well for things like this if needed. That said, it would be nice to have a single piece of configuration! i.e. The app will need to auth against B2C to create an application via the graph, but then create another connection to create groups, but this time via AD?