You may have already solved your issue, however I'll share how I managed to do this for the sake of others after having trawled articles for hours and eventually resorting to a support call, of which I was very grateful to the MS Engineer that helped me.
I was using a managed identity associated with the logic app and given Blob Contributor role to read, write and delete within the required storage account.
Where I went wrong:
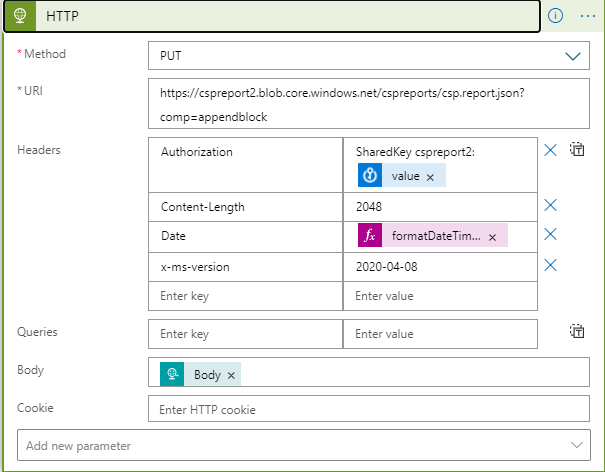
I had manually created an append blob and uploaded it to the container within the storage account and like original poster above was specifying the Content-Length. I kept getting InvalidHeaderValue with the Content-Length being indicated within the error message.
What I needed to do was to create the append blob using Method:PUT, "x-ms-blob-type": "AppendBlob", Content-Length : 0,
x-ms-date : format UTC date like this "Sat, 27 Mar 2021 09:39:44 GMT", x-ms-version: 2019-07-07
Authentication type: Managed identity
Managed identity: System-assigned managed identity
Audience: https://storage.azure.com
Then append to the newly created blob (same as appending to an existing append blob)
using Method:PUT,
at the end of the uri put ?comp=appendblock NB. no need to specify the Content-Length
"x-ms-blob-type": "AppendBlob",
x-ms-date : format UTC date like this "Sat, 27 Mar 2021 09:39:44 GMT", x-ms-version: 2019-07-07
body: put content here
Authentication type: Managed identity
Managed identity: System-assigned managed identity
Audience: https://storage.azure.com
Because I wanted to automate this, I needed to be able to determine if the append blob already existed and whether to create it or append to it. I put a scope action in the logic app and used a GET Http connector basing the Uri on the day's date.
NB. I used x-ms-version: 2019-02-02 for the GET because this worked for using managed identity.
The next action after the GET, was an HTTP PUT action to append to the existing blob as mentioned above, because if the GET was successful then the blob already exists.
Outside of the scope I used a condition which was configured to run if the scope failed.
The condition tested the status of the GET and the error returned:
outputs('name of HTTP Get action')['statusCode'] = 404
outputs('name of HTTP Get action')['headers']['x-ms-error-code'] = BlobNotFound
If True, then as mentioned above, create the append blob and then append to it.