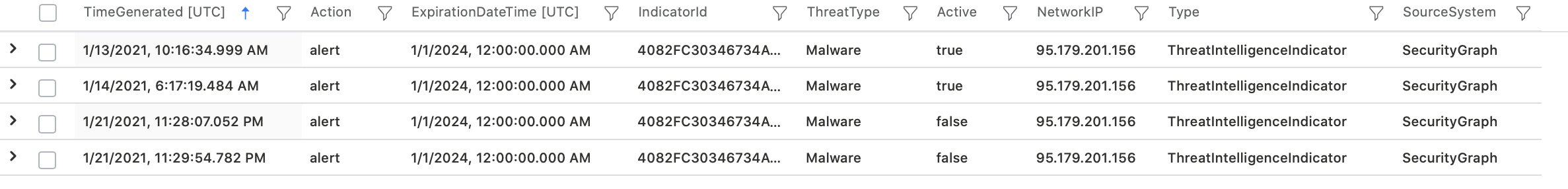
So I figured out a way to filter out the indicators with "false" active status. If anyone knows a better / more efficient way, please suggest:
// Get a list of inactive indicators (FPs)
let InactiveIndicators = materialize(
ThreatIntelligenceIndicator
| where
isnotnull(NetworkIP)
and TimeGenerated > todatetime('2021-01-01')
and Active == false
| distinct NetworkIP
);
// Get a list of active indicator filtering out FPs
let ActiveIndicators = materialize(
ThreatIntelligenceIndicator
| where ExpirationDateTime > now()
and TimeGenerated > todatetime('2021-01-01')
and Active == true
and isnotnull(NetworkIP)
| distinct NetworkIP
| where NetworkIP !in (InactiveIndicators)
);
// Return events match IPs on Destination
CommonSecurityLog
| where not(ipv4_is_private(DestinationIP)) and TimeGenerated >= ago(24h)
| join (ActiveIndicators) on $left.DestinationIP == $right.NetworkIP