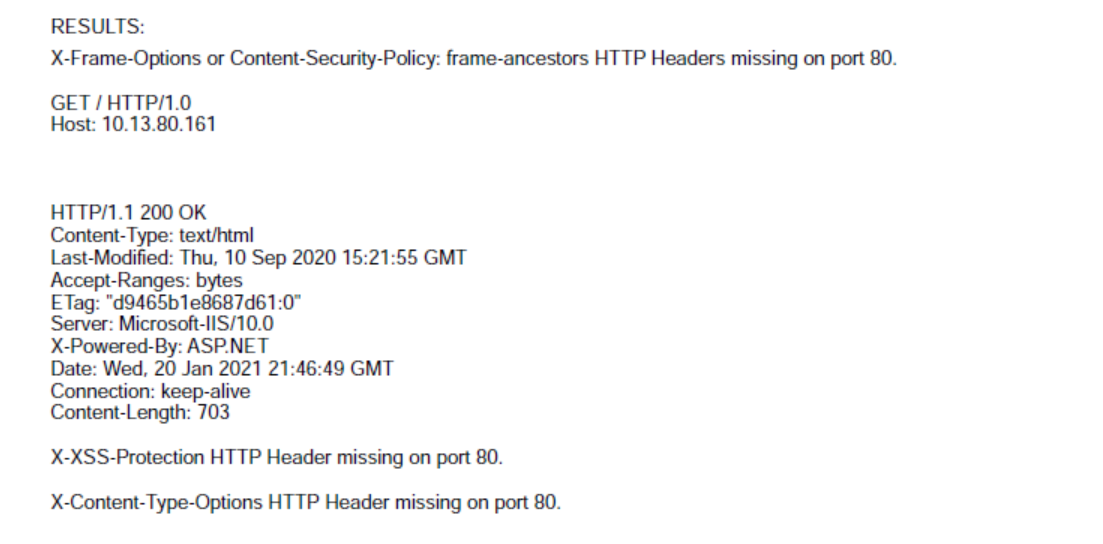
These are related to the security recommendations for sites, known as a CSP. You should really talk to your security team on how to solve these problems. They already know how to do it. You should also research what each security option does as some of them can break existing apps. MDN is a great resource for this. For the security implications refer to the OWASP site.
For these issues you just need to add the appropriate response headers with the appropriate settings. What those settings are depends upon your app. How you append the headers depends on the type of app you have. For ASP.NET Webforms/MVC you general either set a configuration option, if supported, or you need to add it via third party code or perhaps a URL rewrite rule, depending upon the header.
X-XSS-Protection is really not useful in sites anymore and not enforced in newer browsers. You should be using a content security policy instead. Nevertheless for X-XSS-Protection you can probably just inject this header into any response and set the value to 1; mode=block. Refer to MDN for the meaning of the values. You can do this via the config file IIRC.
For X-Content-Type-Options refer to the docs as well. Inject that into your response like the other header.