@Sergey S , You can use the following PS snippet:
$type = "SAML APP"
Get-AzureADServicePrincipal -All $true | Where-Object {($_.Tags -contains "WindowsAzureActiveDirectoryGalleryApplicationNonPrimaryV1") -or ($_.Tags -contains "WindowsAzureActiveDirectoryCustomSingleSignOnApplication")} | Select DisplayName, @{Name="AppType"; Expression={$type}}
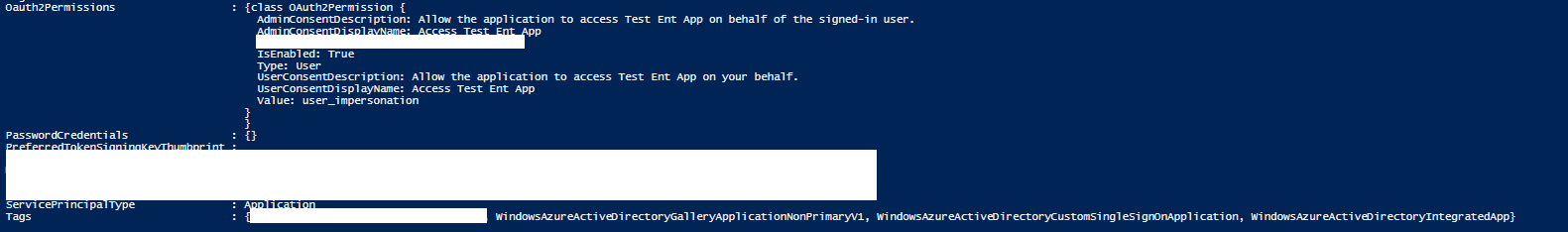
Every Application be it an OAuth app or SAML app (both gallery and non-gallery apps) would have two objects created in AAD when their registration happens. One is called the Application Object and the other is the Service Principal object. Now I used the Service Principal object to prepare this snippet. When you dump the properties of a Service Principal Object using PS, you would find that every application has a certain number of Tags associated with it like:
- OAuth apps would have a tag called "WindowsAzureActiveDirectoryIntegratedApp"
- Gallery SAML Apps would have a tag called "WindowsAzureActiveDirectoryGalleryApplicationPrimaryV1"
- Non-Gallery SAML Apps would have a tag called "WindowsAzureActiveDirectoryCustomSingleSignOnApplication"
Hence you can use the following Tags and find out what kind of app is it. Now the following Tag "WindowsAzureActiveDirectoryIntegratedApp" is common to all types of apps {categories as mentioned in the above list}, hence the snippet i shared above, by using that you can list all the SAML apps (both gallery and non-gallery) and rest of the apps would be your OAuth apps.
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.