The answer is in the very bottom of your screenshot of the "Reasons for non-compliance" page. It shows that alias Microsoft.Security/complianceResults/resourceStatus was expected to be either OffByPolicy or Healthy, but instead has value NotHealthy. Since the reason is "Current value must be in the target value.", we can tell from the table in this section in docs (https://learn.microsoft.com/azure/governance/policy/how-to/determine-non-compliance#compliance-details) that the condition is either in or not notIn. That segment of the policy definition isn't in the screenshot, but you are on the right track for understanding why a resource is non-compliant.
How do you debug Azure policies?

Say I have policy below. How do I exactly know why specific resources was compliant/non-compliant? Where do I actually see all the properties for resource which is used for evaluation for compliancy? Custom roles do not show up in Resources blade in portal, neither showing up in results of evaluation in Policy blade
Have to put image instead of code because this website is not allowing big code pastes looks like
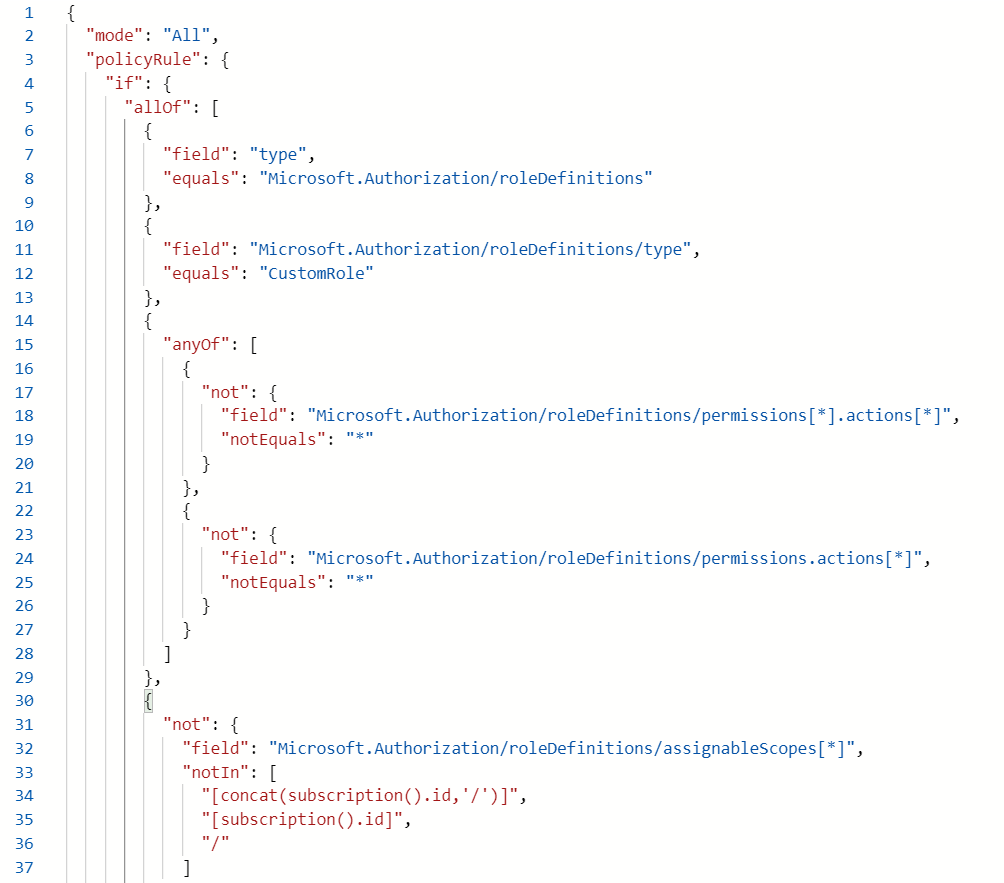
I guess I'm saying there is no report why policy is "Compliant", only when policy is non-compliant where report is being shown as example below
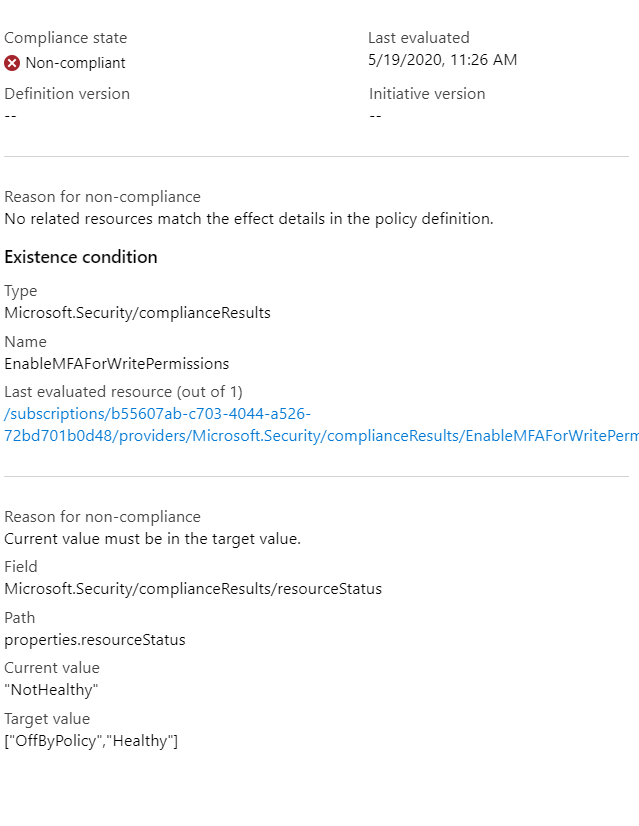
-
 DCtheGeek-MSFT 451 Reputation points Microsoft Employee
DCtheGeek-MSFT 451 Reputation points Microsoft Employee2020-05-19T19:23:17.167+00:00
1 additional answer
Sort by: Most helpful
-
 Gregory Suvalian 186 Reputation points
Gregory Suvalian 186 Reputation points2020-05-19T19:25:07.113+00:00 This was an example of I wanted to see from a different policy. My question is if my policy is compliant when it's not expected to be compliant, how do I know why it's compliant (which specific code path was evaluated to false for policy not to kick in). When policy is
compliantit's not showing the same info like on screenshot why it's compliant.