Hi
1 - https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/overview/ad-fs-openid-connect-oauth-flows-scenarios#client-credentials-grant-flow
[2] - https://tools.ietf.org/html/rfc6749#section-4.4
My goal is to use the OAuth 2.0 client credentials grant specified in RFC 6749 [2], to access web-hosted resources by using the identity of an application. This type of grant is commonly used for server-to-server interactions that must run in the background, without immediate interaction with a user. I'm trying to set Second case: Access token request with a certificate described in the Microsoft Learn 1
Testing on Windows Server 2019 with AD FS role.
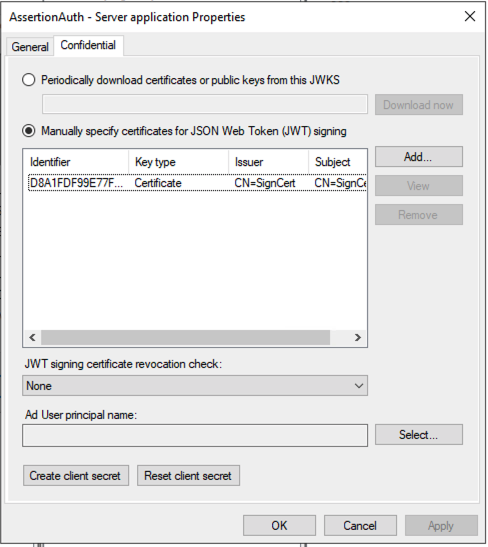
I've setup the Application Group with a Server Application configured to use a certificate for JWT token verification.
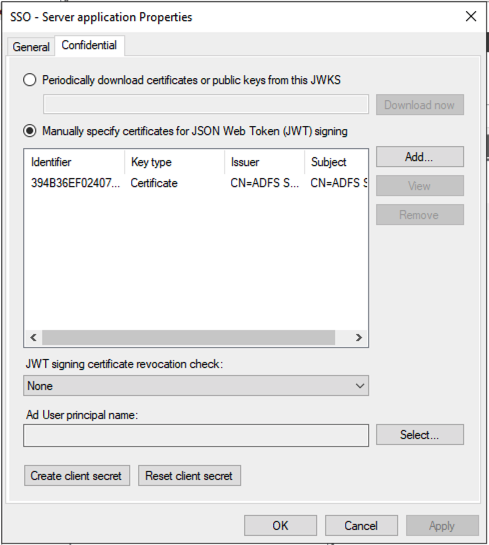
I've tried to issue tokens for client_assertion with two different IDP systems, ADFS and RedHat SSO. But the result is the same.
If anybody had the same issue and have any direction to resolve this?
When I send a request as shown in documentation 1:
POST /adfs/oauth2/token HTTP/1.1
// Line breaks for clarity
Host: https://adfs.contoso.com
Content-Type: application/x-www-form-urlencoded
&client_id=1dfc3dfe-5146-41d0-b32d-9b6019f2f7fd
&client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer
&client_assertion=<JWS TOKEN>
&grant_type=client_credentials
The response is:
{
"error": "invalid_client",
"error_description": "MSIS9622: Client authentication failed. Please verify the credential provided for client authentication is valid."
}
In the server log I see this error:
Log Name: AD FS/Admin
Source: AD FS
Date: 2/21/2021 11:02:05 PM
Event ID: 1021
Task Category: None
Level: Error
Keywords: AD FS
User: MOTO\grp-MAS-ADFS$
Computer: server3.moto.lab.mbctg.com
Description:
Encountered error during OAuth token request.
Additional Data
Exception details:
Microsoft.IdentityServer.Web.Protocols.OAuth.Exceptions.OAuthClientCredentialAuthenticationException: MSIS9344: OAuth Client JsonWebSecurityToken validation failed for the client 'http://sts.moto.lab.mbctg.com/adfs/services/trust'. Unable to find a certificate or public key configured under the client which can validate the signature.
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientSigningKeyResolver.TryResolveTokenCore(SecurityKeyIdentifierClause keyIdentifierClause, SecurityToken& token)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientSigningKeyResolver.TryResolveTokenCore(SecurityKeyIdentifier keyIdentifier, SecurityToken& token)
at Microsoft.IdentityModel.Tokens.JSON.JsonWebSecurityTokenHandler.ReadToken(String rawToken)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientJsonWebSecurityTokenHandler.ReadToken(String rawToken)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthTokenRequestContext.ValidateCore()
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthClientCredentialsContext.ValidateCore()
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="AD FS" Guid="{2ffb687a-1571-4ace-8550-47ab5ccae2bc}" />
<EventID>1021</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000001</Keywords>
<TimeCreated SystemTime="2021-02-21T23:02:05.808907600Z" />
<EventRecordID>7767</EventRecordID>
<Correlation ActivityID="{8af03d56-becc-4b4f-1300-0080000000af}" />
<Execution ProcessID="4444" ThreadID="3908" />
<Channel>AD FS/Admin</Channel>
<Computer>server3.moto.lab.mbctg.com</Computer>
<Security UserID="S-1-5-21-118681301-3582131884-591599284-2103" />
</System>
<UserData>
<Event xmlns="http://schemas.microsoft.com/ActiveDirectoryFederationServices/2.0/Events">
<EventData>
<Data>Microsoft.IdentityServer.Web.Protocols.OAuth.Exceptions.OAuthClientCredentialAuthenticationException: MSIS9344: OAuth Client JsonWebSecurityToken validation failed for the client 'http://sts.moto.lab.mbctg.com/adfs/services/trust'. Unable to find a certificate or public key configured under the client which can validate the signature.
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientSigningKeyResolver.TryResolveTokenCore(SecurityKeyIdentifierClause keyIdentifierClause, SecurityToken& token)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientSigningKeyResolver.TryResolveTokenCore(SecurityKeyIdentifier keyIdentifier, SecurityToken& token)
at Microsoft.IdentityModel.Tokens.JSON.JsonWebSecurityTokenHandler.ReadToken(String rawToken)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthClientJsonWebSecurityTokenHandler.ReadToken(String rawToken)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthTokenRequestContext.ValidateCore()
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthClientCredentialsContext.ValidateCore()
</Data>
</EventData>
</Event>
</UserData>
</Event>
======================================================
In addition, I tested the same Application client to use a secret and it works perfectly as expected.
POST /adfs/oauth2/token HTTP/1.1
//Line breaks for clarity
Host: https://adfs.contoso.com
Content-Type: application/x-www-form-urlencoded
client_id=535fb089-9ff3-47b6-9bfb-4f1264799865
&client_secret=qWgdYAmab0YSkuL1qKv5bPX
&grant_type=client_credentials
Response with token:
{
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6Ik9VczI3d0pBYzAwQ0NMRzVuWW05SnlER0ZUOCIsImtpZCI6Ik9VczI3d0pBYzAwQ0NMRzVuWW05SnlER0ZUOCJ9.eyJhdWQiOiJ1cm46bWljcm9zb2Z0OnVzZXJpbmZvIiwiaXNzIjoiaHR0cDovL3N0cy5tb3RvLmxhYi5tYmN0Zy5jb20vYWRmcy9zZXJ2aWNlcy90cnVzdCIsImlhdCI6MTYxMzk0OTc2MSwibmJmIjoxNjEzOTQ5NzYxLCJleHAiOjE2MTM5NTMzNjEsImFwcHR5cGUiOiJDb25maWRlbnRpYWwiLCJhcHBpZCI6IjFkZmMzZGZlLTUxNDYtNDFkMC1iMzJkLTliNjAxOWYyZjdmZCIsImF1dGhtZXRob2QiOiJodHRwOi8vc2NoZW1hcy5taWNyb3NvZnQuY29tL3dzLzIwMDgvMDYvaWRlbnRpdHkvYXV0aGVudGljYXRpb25tZXRob2QvcGFzc3dvcmQiLCJhdXRoX3RpbWUiOiIyMDIxLTAyLTIxVDIzOjIyOjQxLjQ4NloiLCJ2ZXIiOiIxLjAifQ.Izcx1KIpZGFK6ewKcZiv2g4mNn6lTXGZQCxjIYG24PrPRRr_3qUoYedWnoXfysqGzE0NdS-Bh3Y9CwHBdWBp5QHttedz9NEg9pNsjjRP209Qc75A4z0TdoIrxbpKFXQ4HfmgOu0miWXNCHbky28Z2ILGg8TWsYC7z6Kf1jHInmxUk96rJOEn1CaJ2AdL_Excic0B_v3FxkVQt-sOlzha71Q5jw2lBNyhR2wu108OwZ3MKN2iyqGl0Q6TJ5PAasBjJsy45L2CPTSaljFQcPmv_-ncXAIV-kYKVn4uvT5aRAGW9zLHtR4zatpozgBPXrWu-FycG7grkNl7DZoVxJXNbg",
"token_type": "bearer",
"expires_in": 3600
}
1 - https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/overview/ad-fs-openid-connect-oauth-flows-scenarios#client-credentials-grant-flow
[2] - https://tools.ietf.org/html/rfc6749#section-4.4