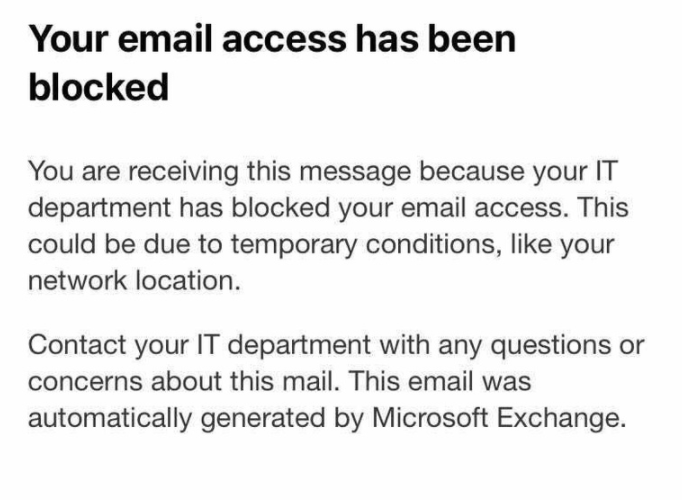
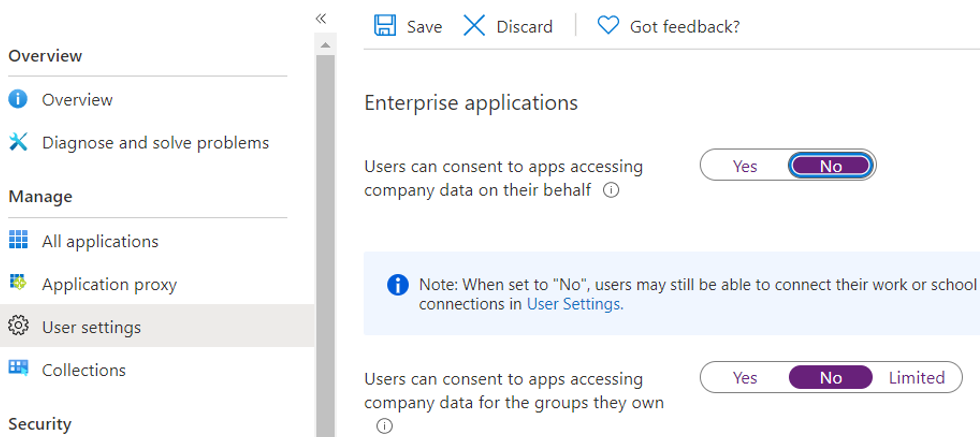
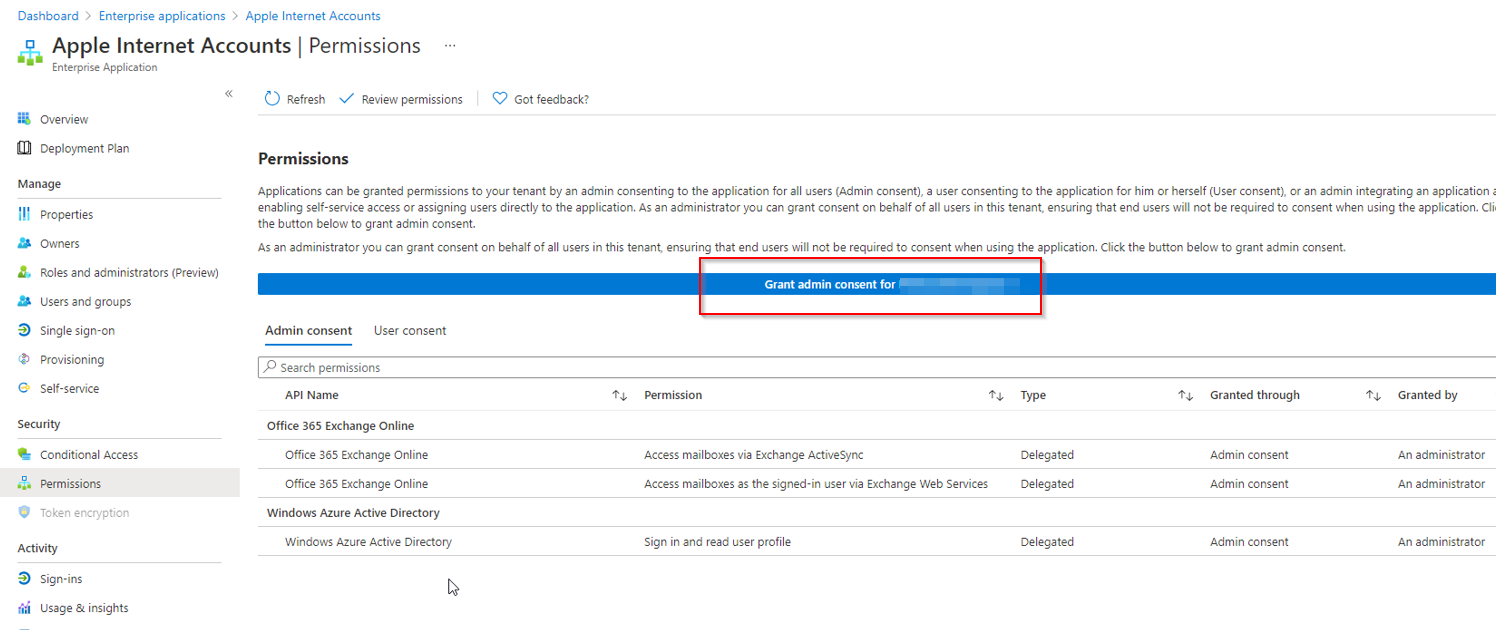
You are saying whether or not you have CA policy, you are not able to access email on iOS native app right?
This makes me think this restriction is coming from Exchange admin side. Check you Exchange admin center or your exchange admin
Exchange admin center > mobile