Thanks for reaching out. You would need to add the Azure active directory connector in Azure Sentinel workspace. We collect the sign in Info in AAD logs.
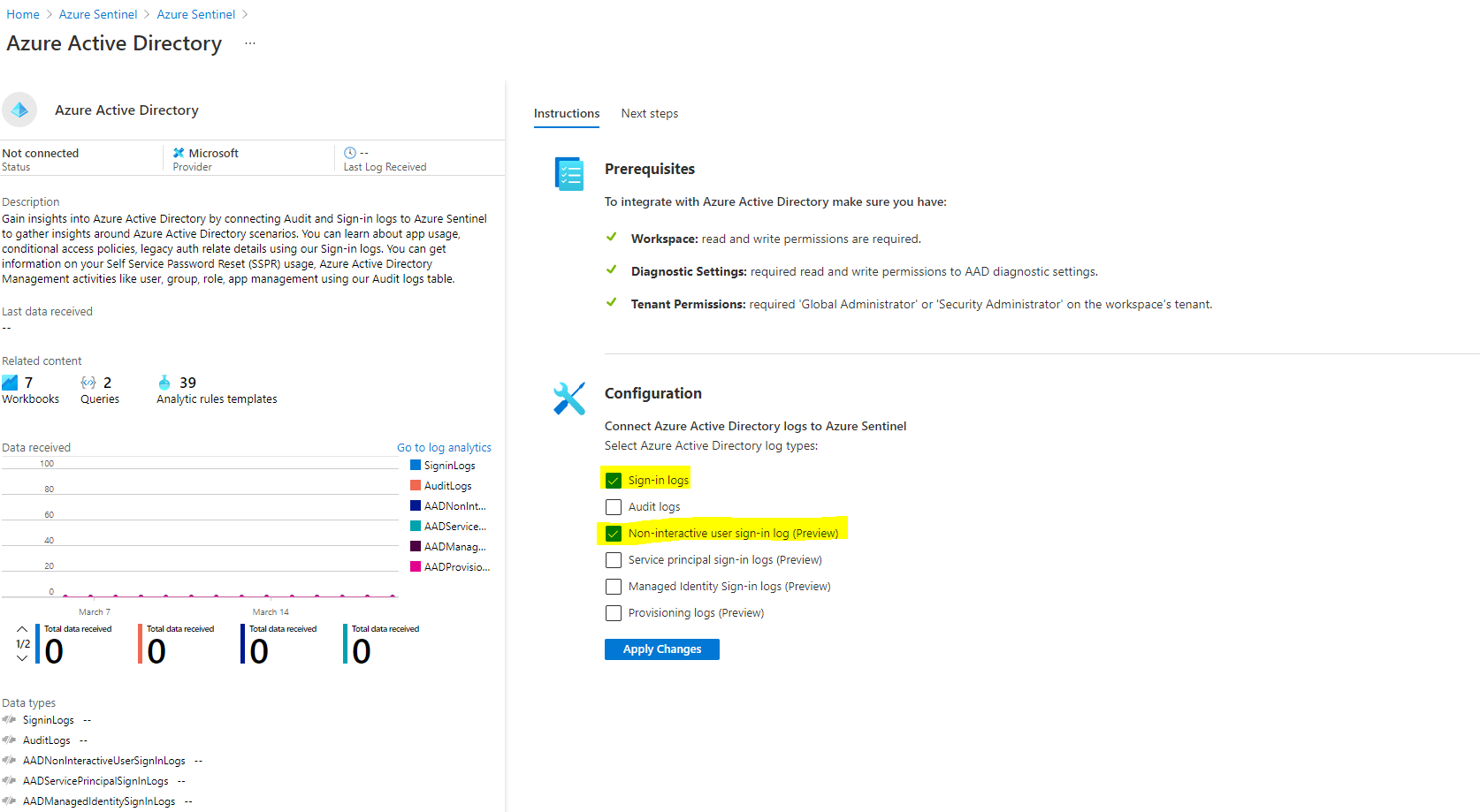
Once the logs are ingested which can take some time, there are inbuilt queries which you can modify to get just the office 365 portal logs.
That is denoted as Microsoft Office 365 Portal in Sign in reports.
So you can run a basic query which as basic as
SigninLogs
| where AppDisplayName == "Microsoft Office 365 Portal"
| take 100
Which will take the result from sign in logs table and show top 100 results. The query can be modified to any specific UPN, location or device as per need.
You can check few of the templates in AAD connector which has lots of sample queries inbuilt.