Hi, we have problem to connect from active directory to key vault during authentication.
Something in Azure or in AD has to change, because we used the same way of authentication including key vault as before and now we are unable to proceed with authentication for any new app registrations in AD. All previously created app registrations in AD are working just fine (using key vault), any new one is not working. We only receive error:
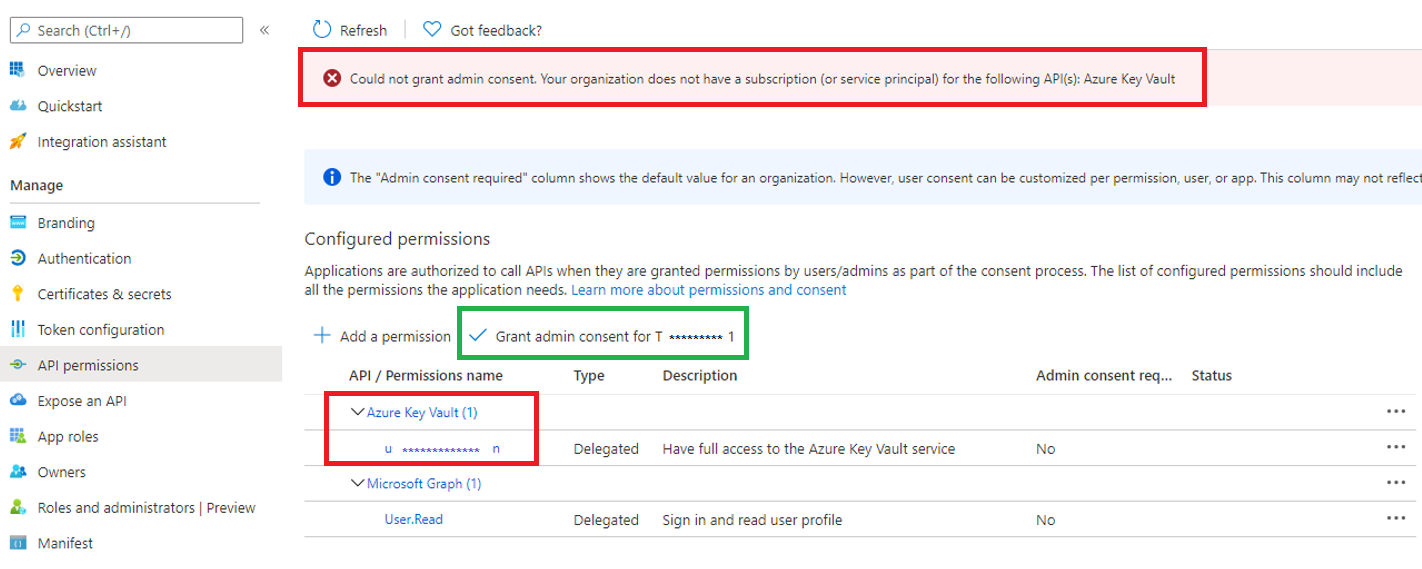
System.Exception: An error was encountered while handling the remote login. ---> Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectProtocolException: Message contains error: 'access_denied', error_description: 'AADSTS650052: The app needs access to a service ('https://vault.azure.net') that your organization 'AZURE TENANT ID' has not subscribed to or enabled. Contact your IT Admin to review the configuration of your service subscriptions.
We have multiple Azure ADs: AD1 containing all azure resources (including key vault), and AD2 only for user authentication (there are no subscriptions or resources in AD2).
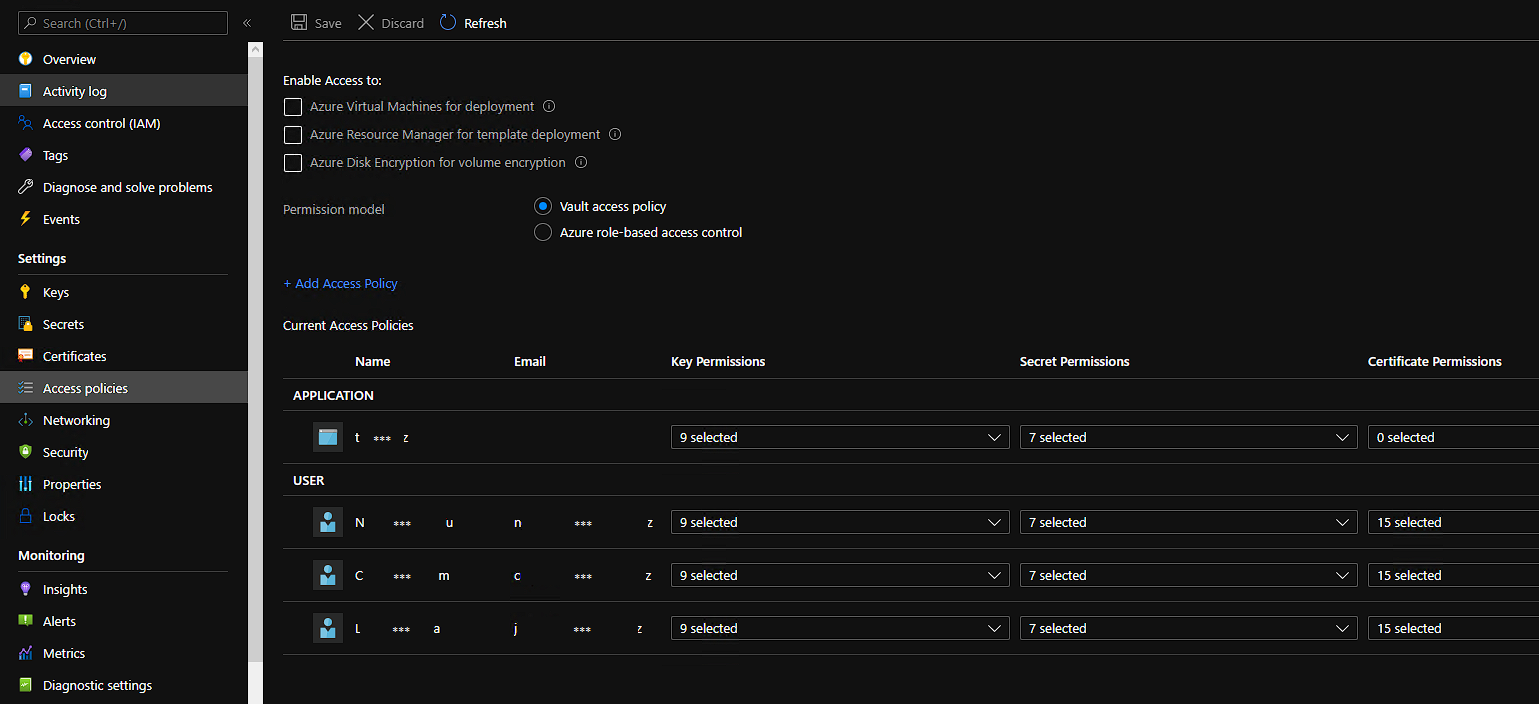
Our app is hosted in Azure App service and its identity is included into key vault access policy - all in AD1.
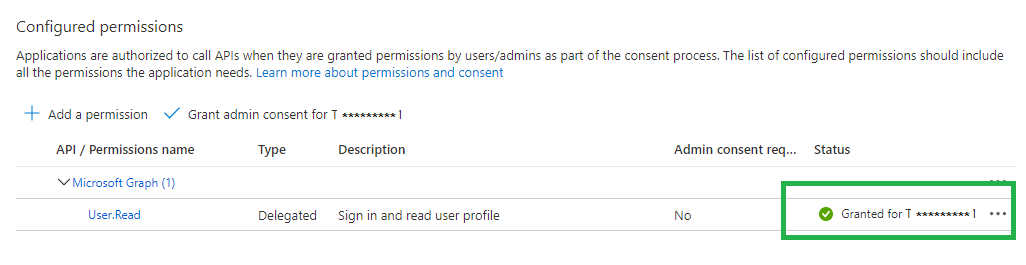
In AD2 we created app registration as usually, added user_impersonation to have full access to the Azure Key Vault service. We did the same scenario as we did before for other environments in different ADs (all of them are connecting to AD1).
Environment is set in the same way as other working environments, however we receive only error above when trying to access out application.
If we use already created app registration (created in the year 2020) everything works just fine. When we try to create new app registration in Azure AD, nothing is working after connecting to this app registration. Environment which was operating just fine have the error above after connected via new app registration.
And new app registration is set in the same way as the operating one.