Hi @ParshwaAmitkumarShah-5758 ,
I've gotten this error for a variety of reasons while using the NPS extension so I'll give several things to try.
- It's possible that the request is timing out too soon. In that case, make sure that it's set to at least 60 seconds to give enough time for the request to succeed.
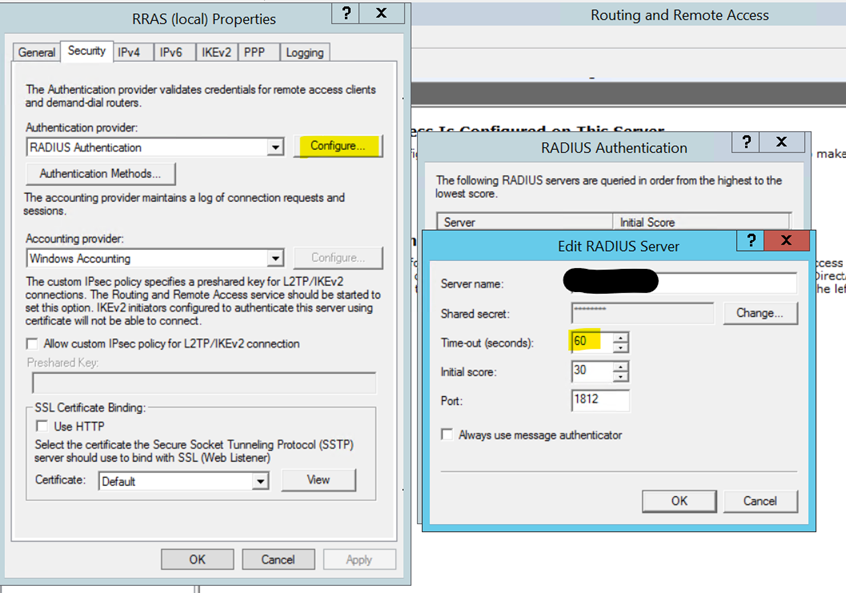
- Make sure you have the latest version of the extension installed. Older versions sometimes threw that DLL error. https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension-rdg#install-the-nps-extension
- Make sure that there aren't any duplicate or old certificates on the server.
You can check using:
Get-MsolServicePrincipalCredential -AppPrincipalId "app-principal-id" -ReturnKeyValues 1
Then you can remove duplicates using:
Remove-MsolServicePrincipalCredential -AppPrincipalId "app-principal-id" -KeyIds <enterkeyidhere>
See also the related discussion: https://www.reddit.com/r/AZURE/comments/a0qp5p/azure_mfa_nps_extension_for_rdgateway/
If you're still having this issue feel free to send your event logs to me at AzCommunity@microsoft.com and I can help troubleshoot.
Thanks!
Marilee