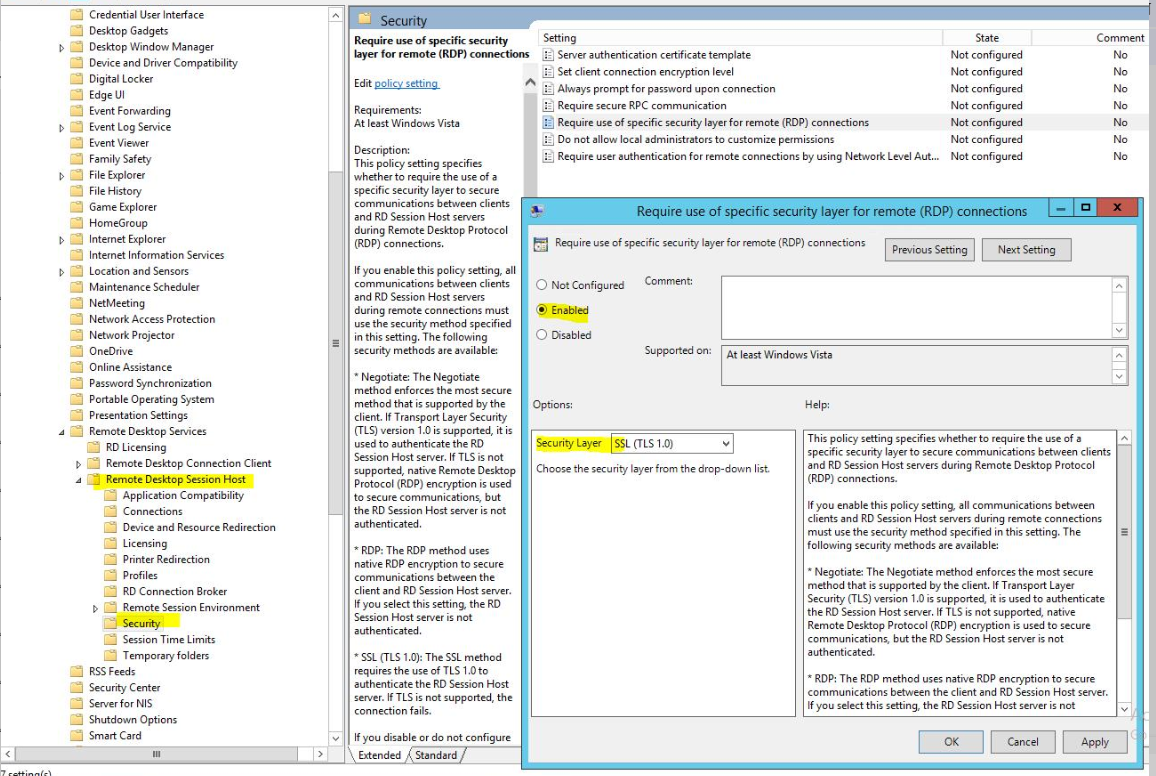
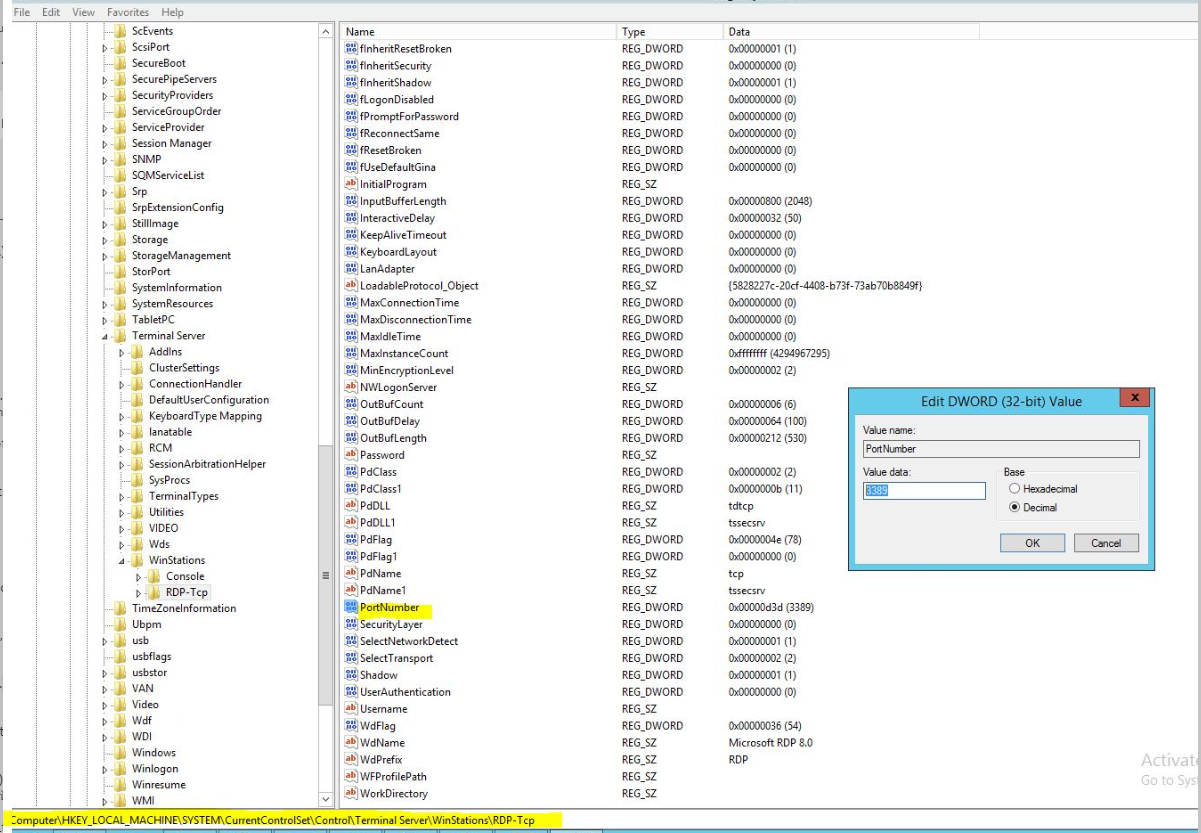
Hello @lra ,
Thank you for posting here.
1.Would you please provide the link of your reference to us?
2.Based on "however the guide that I have as a reference, has some policies or configurations that I am not clear yet", did you mean you can not find the settings or you can not understand the meaning of them or others?
For example:
Access to a computer from the network: Delete the permissions of the "Everyone" group and add authenticated users.
GPO setting, by default there is Everyone group and authenticated users, you can delete the permissions of the "Everyone" group if needed.
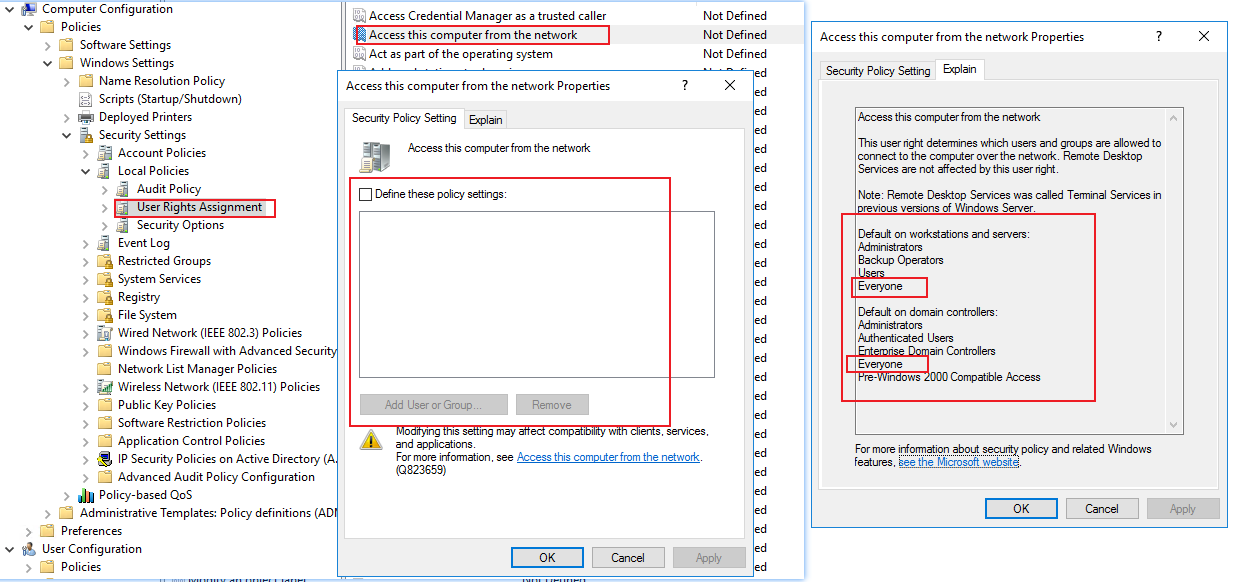
Login on the local machine:
On workstations: Disable the "guest" user of the machine.
If guest is not disable, you can disable it if needed.
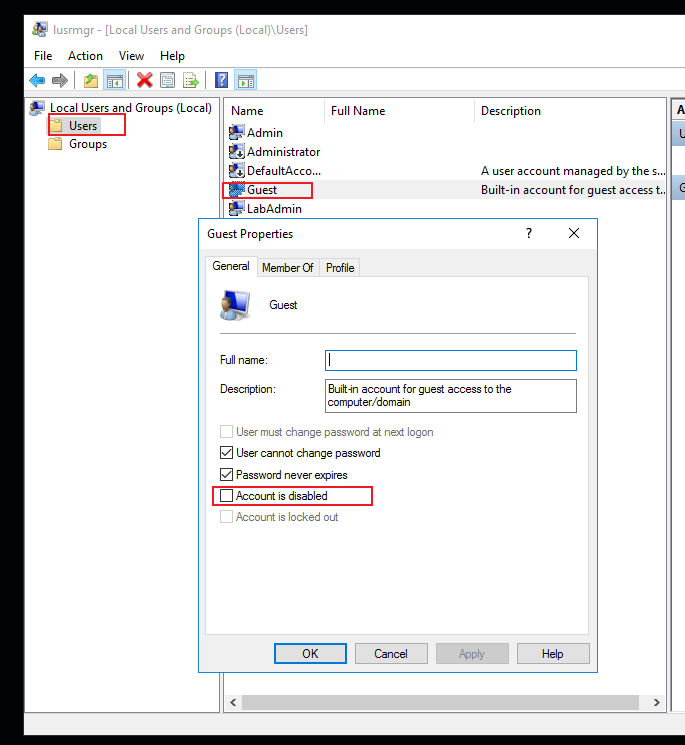
Hope the information above is helpful.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.