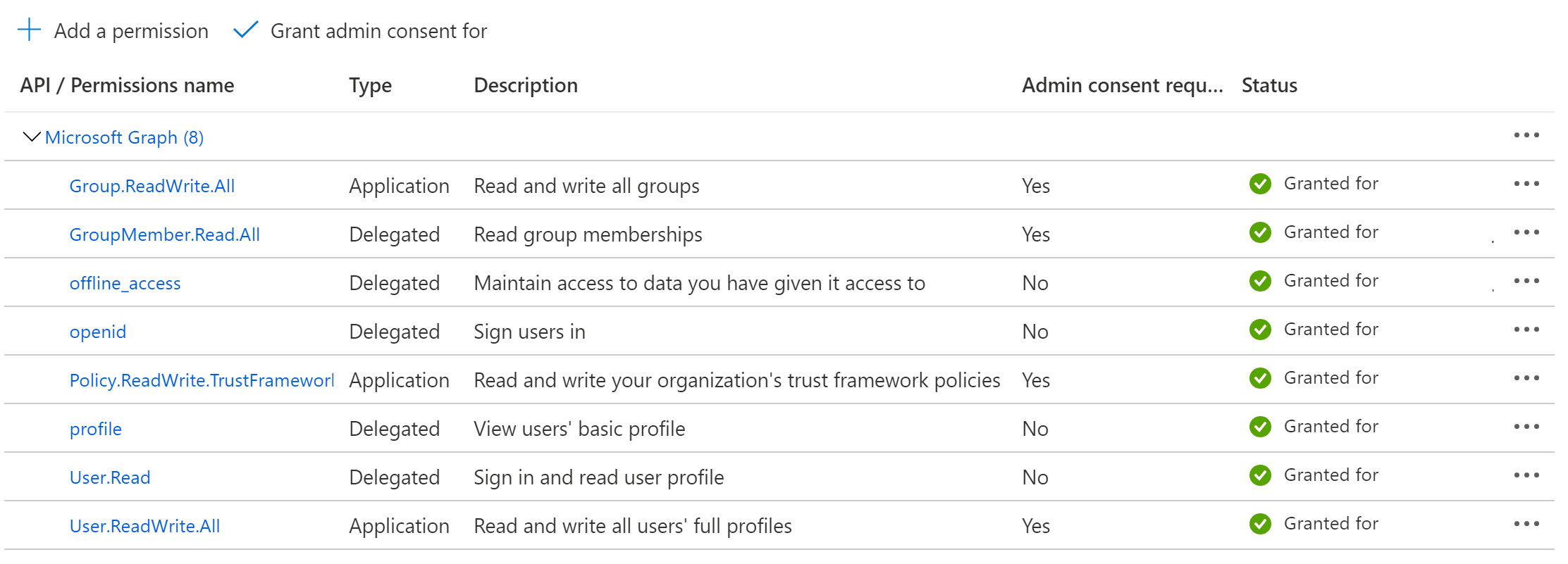
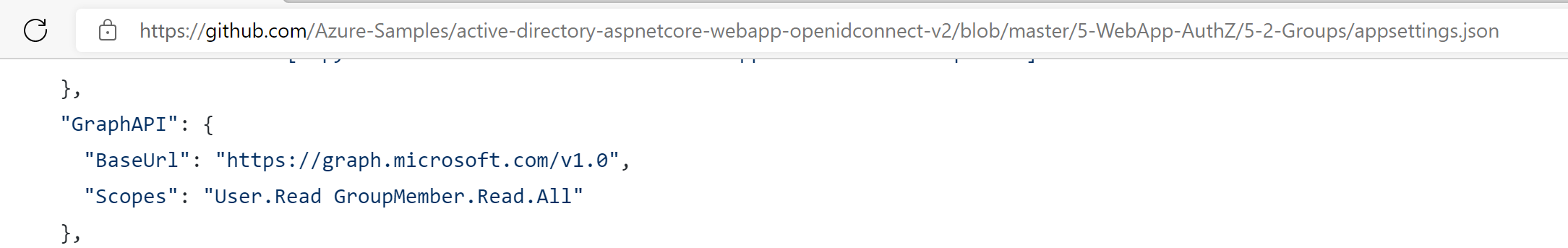
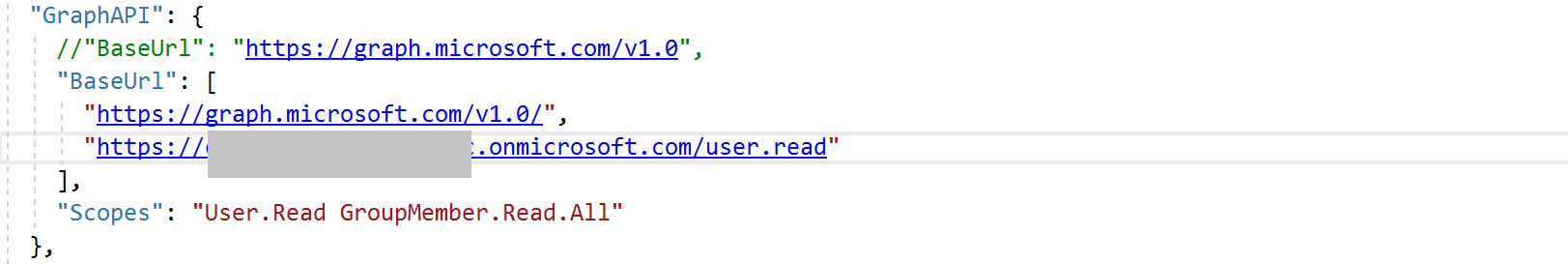
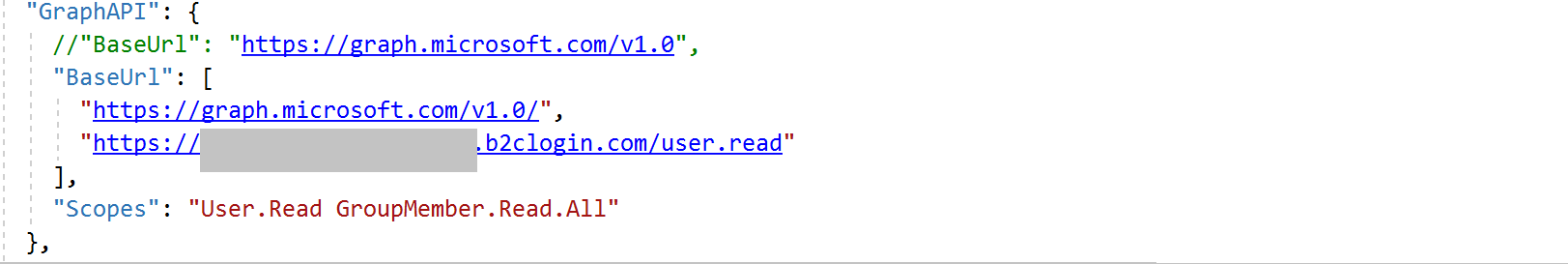
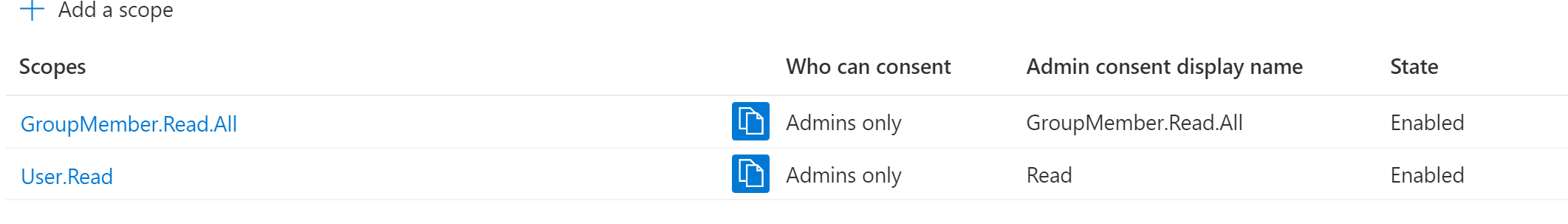
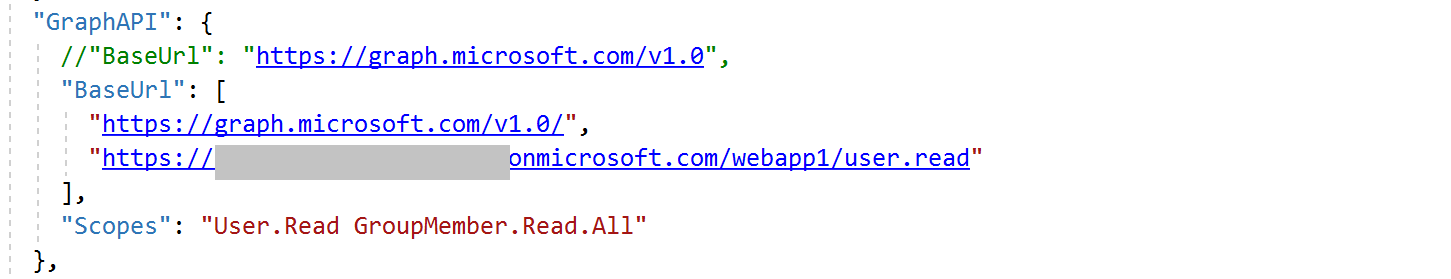
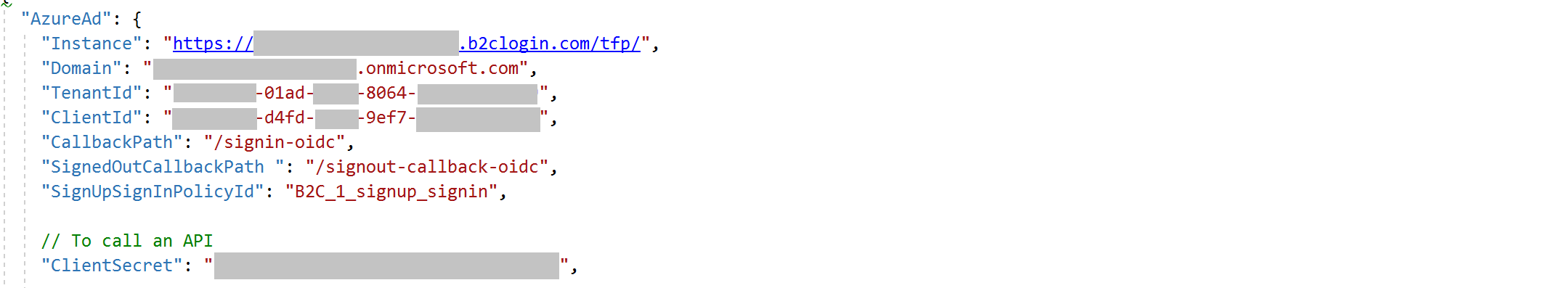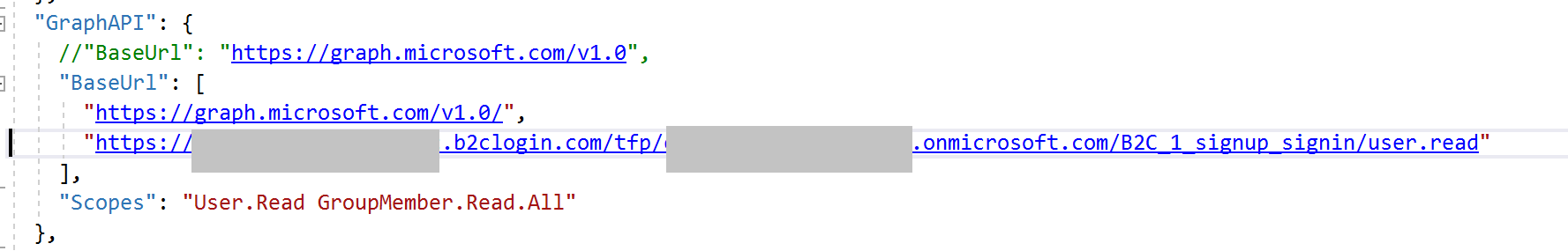Hi @Carol Lai , are you using B2C authority? Please reference this sample. You may need to add the b2c authority uri to the scope (instead of only user.read), like this:
'https://graph.microsoft.com/v1.0/me', ["https://authorityuri/user.read"]
Please let me know if this works. If not I can help you further.
If this answer helped you, please mark it as "Verified" so other users may reference it.
Thank you,
James Hamil