Hello @JohnpCurtiss,
Thank you for posting here.
Here are the answers for your references.
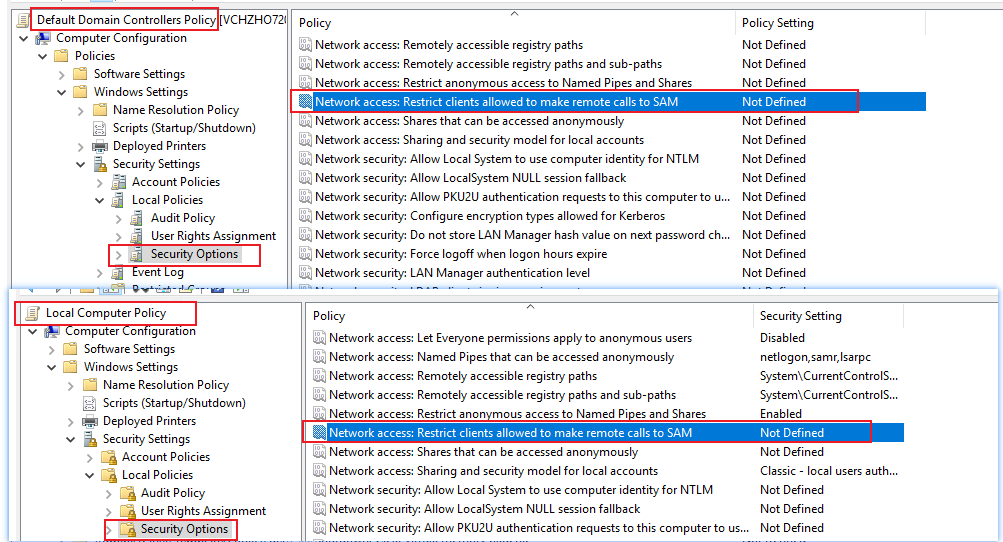
Q1: but on domain controllers, it is "everyone". however, i just promoted a bunch of 2016 DCs, and this does not seem to be the case.
A1: By default, we can see the setting is "Not Defined" (we cannot explicitly see Everyone on Domain Controller or see "administrators" on member servers,), but they have such "Existing" setting on different versions of Windows as the article mentioned.
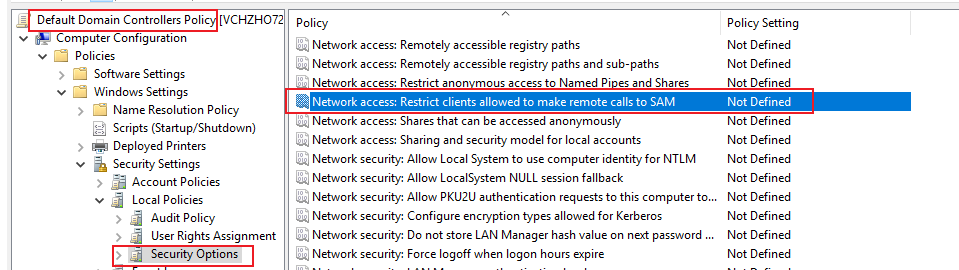
Q2: are 2016 domain controllers really supposed to have "everyone" in this?
A2: Yes, see A1.
Q3: this has been working for years on 2012 R2 domain controllers, which don't have this "restrict clients who can make same calls" setting.
A3: The setting was first supported by Windows 10 version 1607 and Windows Server 2016 (RTM) and can be configured on earlier Windows client and server operating systems by installing updates from the KB articles listed in Applies to section of this topic.
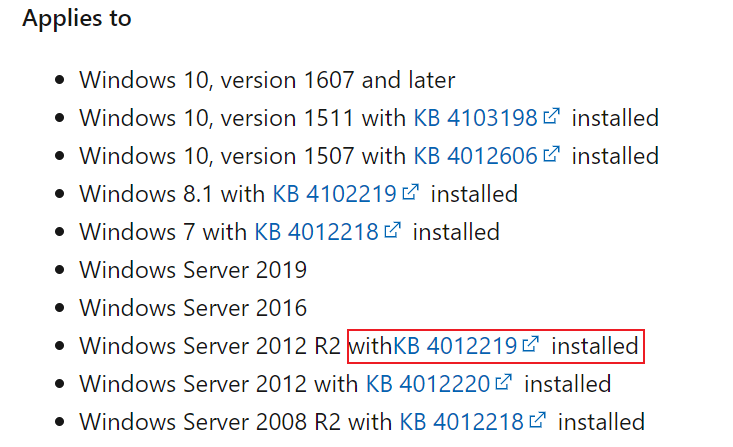
In my lab Windows server 2012 R2 DC, because I did not install KB4012219 on this DC, I cannot see such gpo setting (network access - restrict clients allowed to make remote calls to SAM), either.
Hope the information above is helpful.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.