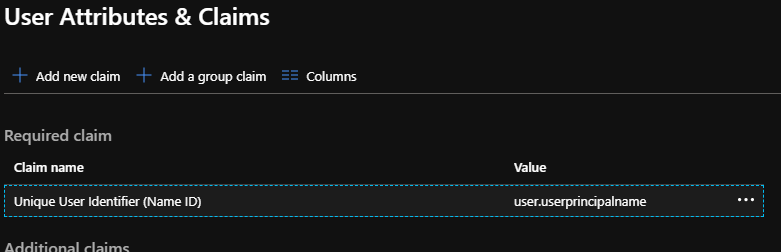
The fix is to use user.localuserprincipalname in the Unique User Identifier (Name ID) claim, this will make it use the .onmicrosoft.com upn for External Azure Active Directory guests as that's their upn in your tenant..
SAML UPN Claim for B2B guest user changing to Mail attribute
I'm using Azure AD to provide authentication for Citrix Netscaler via SAML. To solve a particular problem, I'm setting up a Citrix Storefront for external vendors that I'm wanting to set up for them to use their own companies login via Azure B2B. I've used the Azure B2B to On Premise AD Powershell sync script to sync the B2B users to the on prem AD.
The problem is that Azure AD is transforming the guest users from the UPN format of "user_guestdomain.com#EXT#@keyman .onmicrosoft.com" to the guest users mail address (eg, user@guestdomain.com). This obviously means that the authenticated user isn't matching to the synced on prem user object which creates the UPN in the original format. According to this article this is an automatic transformation that happens with the assumption that the original format wouldn't be desired. Is there anyway to disable this and have it pass through unaltered?
2 additional answers
Sort by: Most helpful
-
 AmanpreetSingh-MSFT 56,311 Reputation points
AmanpreetSingh-MSFT 56,311 Reputation points2020-07-15T11:05:37.097+00:00 Hello @Matt-2690
You have full control over the attributes that you want to pass in SAML token for the federated Citrix Netscaler enterprise application.
For this purpose, you need to navigate to Azure Portal > Azure AD > Enterprise Applications > Citrix Netscaler > Single sign-on > SAML-based Sign-on > edit User Attributes & Claims > edit the claim you want to customize i.e., Name ID or any other claim that you want to pass in the SAML token and select the attribute you want to pass as Claim. You can also add additional claims and transform the claims using this option.
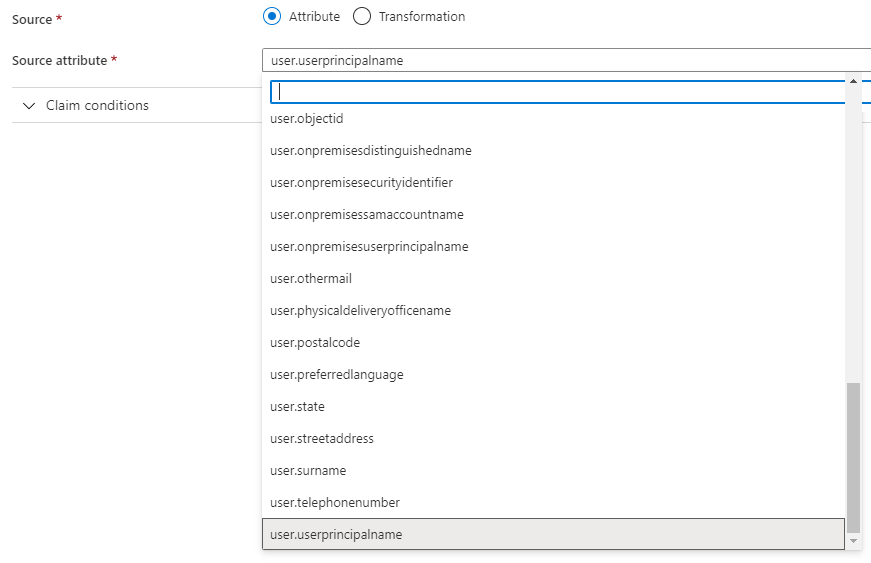
Below is a snippet from one of my SAML token where I am passing mail as emailaddress and UPN as name claim:
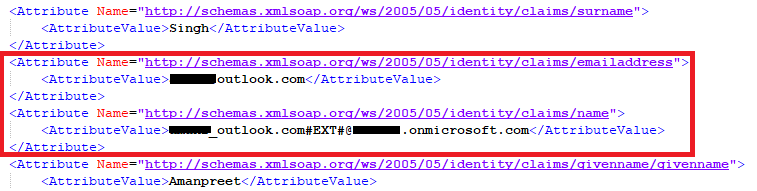
Please do not forget to "Accept the answer" wherever the information provided helps you. This will help others in the community as well.
-
Phil_L 1 Reputation point
2020-10-19T17:53:53.397+00:00 It's been a few months since this thread opened but I wanted to see if there has been any better understanding of this.
I have an app which I am using UPN for the uniqueID. I can't use email because that can change for a user but UPN will never change. So, in my SSO apps, I use the 'user.userprincipalname'I came across the "user_guestdomain.com#EXT#@keyman .onmicrosoft.com" format when I included my Gmail account as a guest SSO user. That is what was on the token for the NameID. If I use that in the SSO app for my fedID, I get access. Now, when I setup another external user and I assumed the NameID would be the same so that's what I used in the app but for this user, the token had their real email address for the NameID on the token. I found that the user with their real email as the NameID is using their Azure federation credentials. In the Azure AD user profile, that user is a type:Guest BUT the source shows: External Azure Active Directory. My Gmail account source is: Microsoft Account.
I haven't dug deeper into this yet but this is my suspicion. I was doing that research when I came on this article. Can anyone else confirm what I'm seeing?
Thansk,
Phil