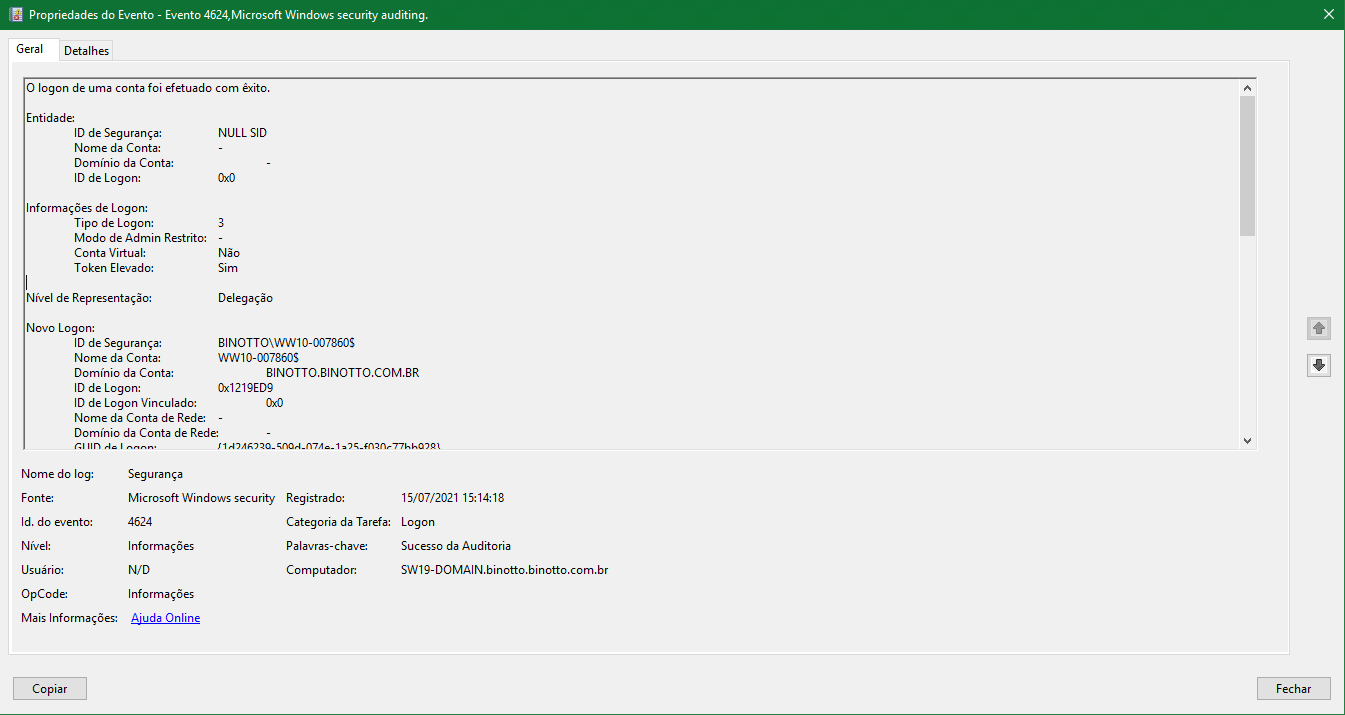
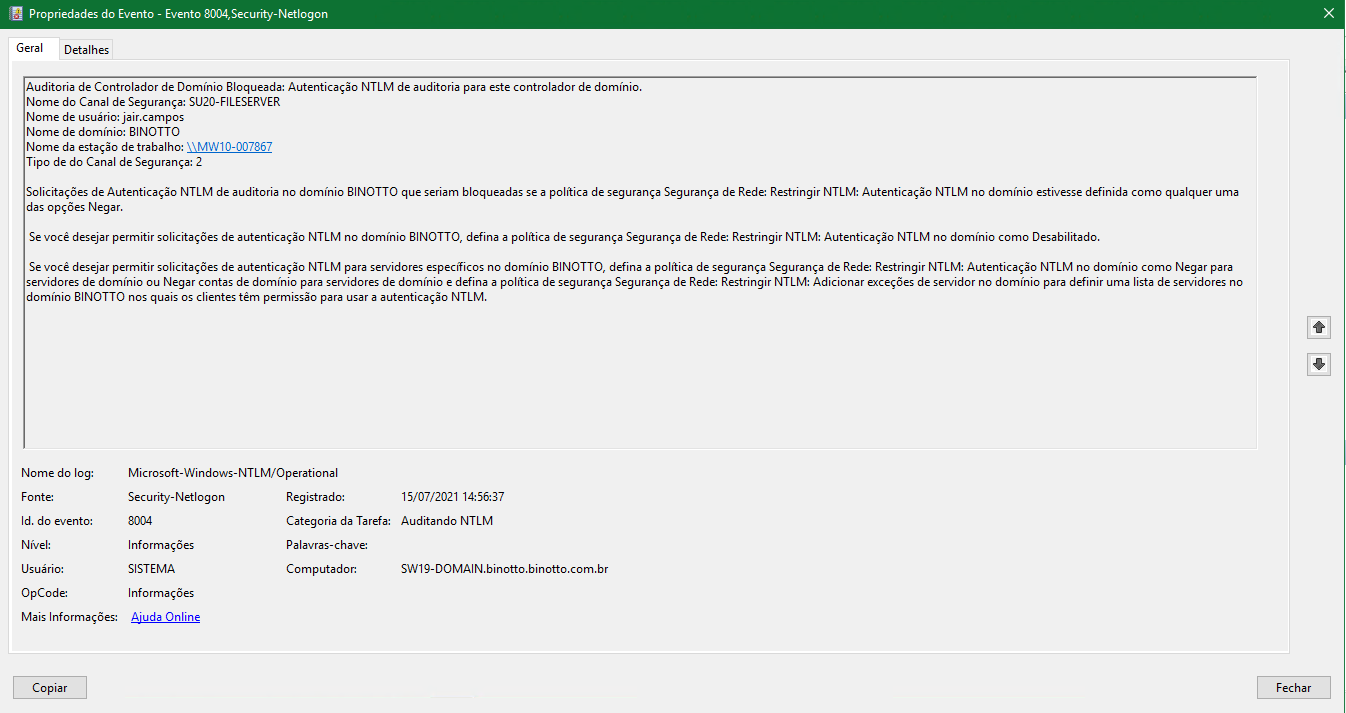
Hello @PauloDiegodaSilva-8951,
Thank you so much for posting here.
Normally, for AD environment, the Kerberos authentication will be tried firstly, and if it fails, then falls back to NTLM.
I tried to disable NTLM authentication and enabled the audit in my lab. When trying to authenticate with NTLM, there will be warning that NTLM authentication requests to this server have been blocked.
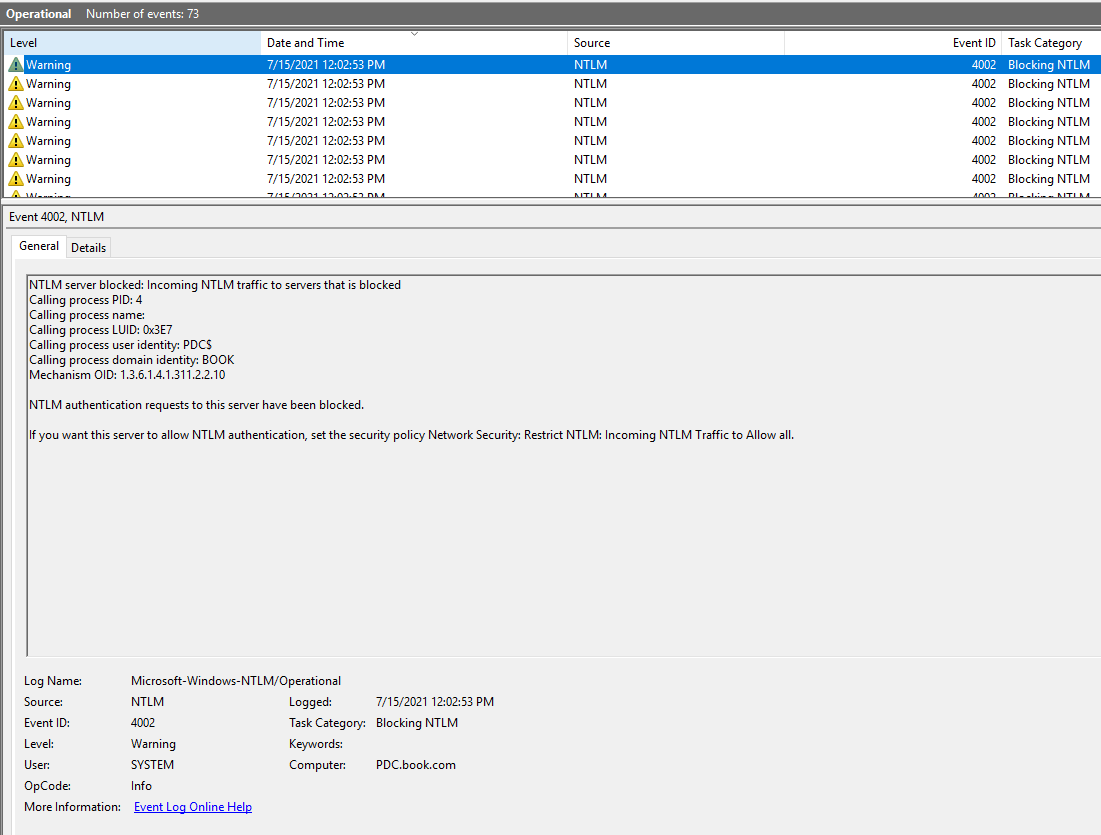
As for the NTLM request we mentioned, would you please kindly provide us more information or more screenshots about the event logs?
Q1: how do I enforce Kerberos onto these servers and/or file shares?
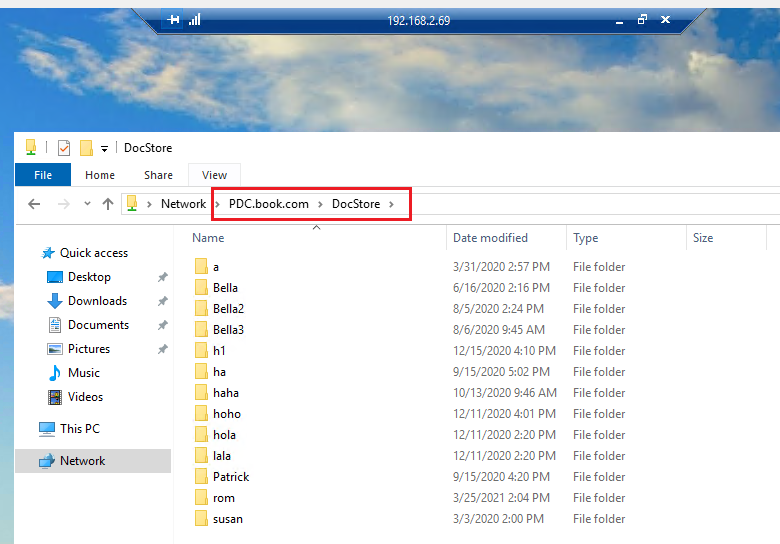
I did the test as shown below:
Domain user accesses the server (domain joined server) via RDP, and then access the file server by their DNS names, for example: \PDC.book.com\DocStore. It could be successful.
Q2: Also, at any workstation if I try to log via RDP into any server I get asked for password, which I believe is a NTLM behavior thing, so it's like my workstations use Kerberos just fine to log the user in, but they don't use it to log into other services.
It is hard to say it is a NTLM behavior. In my previous tests, I tried to log via RDP and it also asked for the password.
Q3: I had a look into this option but didn't quite understand if I can enforce this via GPO or it'll cause any problems in my environment.
The option should be assigned only if there is a clear need for its functionality. When you assign this right, you should investigate the use of constrained delegation to control what the delegated accounts can do.
Reference: https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/enable-computer-and-user-accounts-to-be-trusted-for-delegation
For any question, please feel free to let me know.
Best regards,
Hannah Xiong