I found the solution, In the API Header, I was specifying the Content-Length= 67 which was not required. Now I am able to get the Success response
Register an application on Azure AD using MS Graph API
Hi,
I am trying to register an application on the azure ad using the Graph API calls.
I am using the postman to hit the APIs and I have admin access in Azure.
So Far I have tried the following things
- I registered an application manually on Azure AD using this doc- https://learn.microsoft.com/en-us/azure/databricks/dev-tools/api/latest/aad/service-prin-aad-token. (I gave all the required permissions to my application)
- I am fetching the token using the service to service call client credentials- https://learn.microsoft.com/en-us/azure/active-directory/azuread-dev/v1-oauth2-client-creds-grant-flow.
- After getting the token I pass it in the Authorization and hit the MS graph Create Application endpoint. https://learn.microsoft.com/en-us/graph/api/application-post-applications?view=graph-rest-1.0&tabs=http.
- But In the postman, I am not getting any response body. I have checked my Azure Tenant but I am not able to find any newly Registered App.
For Token service(Get)
Endpoint- https://login.microsoftonline.com/{my-tenant-id}/oauth2/token
body-
grant_type:**client_credentials
**client_id:{app-id}
scope:**https://graph.microsoft.com/.default
**client_secret:{secret}
//resource:https://graph.microsoft.com
Response success(200) with token
For Create App(POST)
https://graph.microsoft.com/v1.0/applications
body: {
"displayName": "Created with MS Graph API"
}
Authorization: Bearer {token}
Response: Nothing is showing in response
1 additional answer
Sort by: Most helpful
-
 AmanpreetSingh-MSFT 56,306 Reputation points
AmanpreetSingh-MSFT 56,306 Reputation points2021-07-30T07:15:04.857+00:00 Hi @Ayush Sharma · Thank you for reaching out.
Could you please try decoding your Access Token at https://jwt.ms and confirm if below application permissions are present under Roles claim:
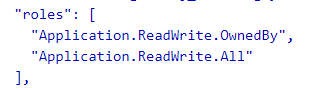
If these permissions are not present, go to Azure Portal and open the application, that you are using to acquire the token. Under the application permissions blade, please add below Application Permissions under API Permissions blade of the application and Grant Admin consent.
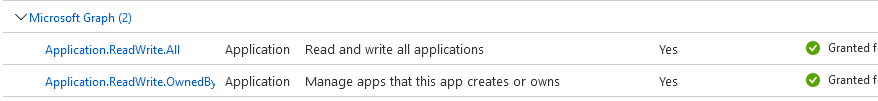
Once you have these permissions in the token, pass it as bearer token to make the POST call to create the application.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.