Hello @Shrijan Tiwari ,
Apologies for the delay in response.
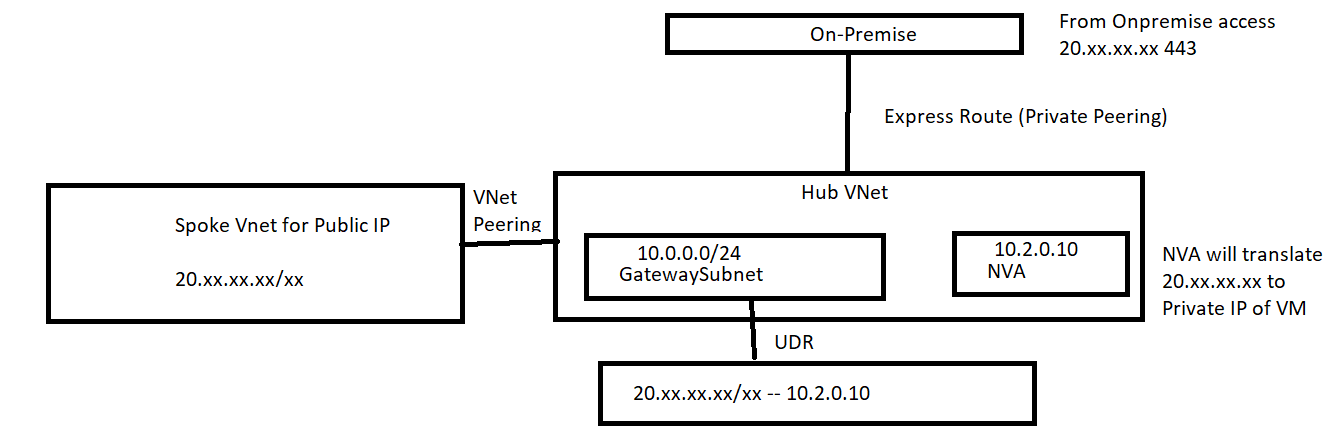
1) The ExpressRoute gateway will advertise the Address Space(s) of the Azure VNet, you can't include/exclude at the subnet level. It is always the VNet Address Space that is advertised. Also, if VNet Peering is used and the peered VNet has "Use Remote Gateway" enabled, the Address Space of the peered VNet will also be advertised. From a routing perspective, all virtual networks linked to the same ExpressRoute circuit are part of the same routing domain and are not isolated from each other. If you need route isolation, you need to create a separate ExpressRoute circuit.
Reference : https://learn.microsoft.com/en-us/azure/expressroute/expressroute-faqs#how-are-vnets-advertised-on-expressroute-private-peering
2) An ExpressRoute circuit, once set up, allows you to access services within a virtual network and other Azure services simultaneously. You connect to virtual networks over the private peering path, and to other services over the Microsoft peering path.
Azure Private peering lets you connect to virtual machines and cloud services directly on their private IP addresses.
Azure Public IP addresses for IaaS (Virtual Machines, Virtual Network Gateways, Load Balancers, etc.) is supported over Azure Microsoft peering.
Microsoft supports bi-directional connectivity on the Microsoft peering. You must connect to Microsoft cloud services only over public IP addresses that are owned by you or your connectivity provider and you must adhere to all the defined rules.
So, in order to access the Public IP (20.xx.xx.xx) from your on-premises over ExpressRoute, you should create a Microsoft peering in your ExpressRoute circuit.
Reference : https://learn.microsoft.com/en-us/azure/expressroute/expressroute-faqs#supported-services
https://learn.microsoft.com/en-us/azure/expressroute/expressroute-circuit-peerings
https://learn.microsoft.com/en-us/azure/expressroute/expressroute-nat
https://learn.microsoft.com/en-us/azure/expressroute/expressroute-howto-routing-portal-resource-manager
Kindly let us know if the above helps or you need further assistance on this issue.
Please "Accept the answer" below if the information helped you. This will help us and others in the community as well.