Hi,
I am trying to migrate away from the Log Analytics agent to the Azure monitoring agent for the security events in Azure sentinel. Reason being that I only need certain event ID's. For that I have already configured one server with the azure monitoring agent which is not visible in Arc.
However, when I configure a custom data collection rule, it is not working. I have tested the xpath query locally on the domain controller and there it works fine.
All the other agents that are still using the old Security Events solution are working fine. But I don't see any data coming in from the new domain controller with the Azure monitoring agents.
The Azure monitoring agent is in a healthy state in the Azure portal.
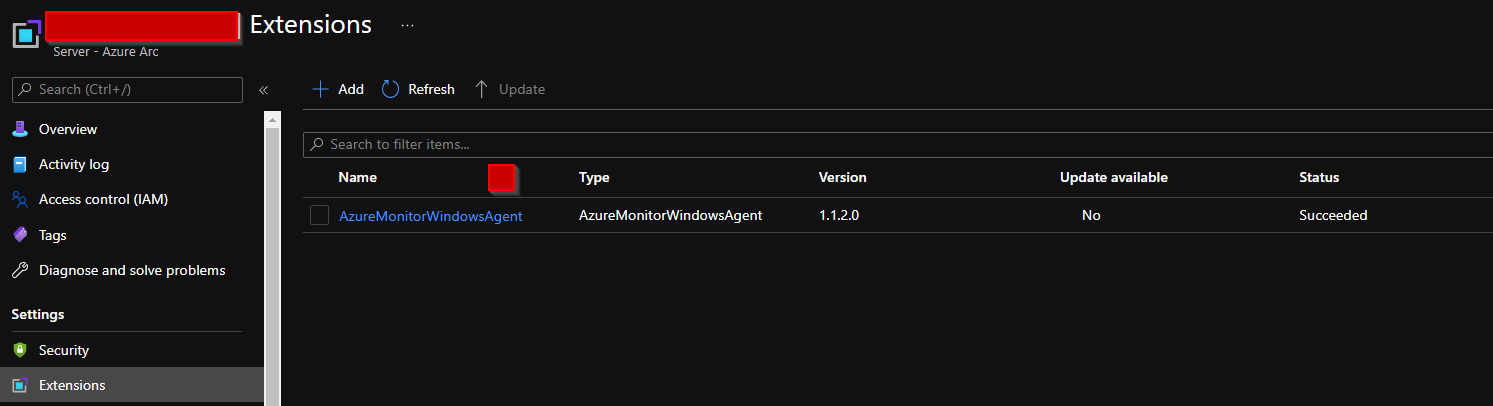
I currently have the Security Events and Windows Security Events (Preview) active in Azure sentinel.
Here are the two event collection rules that I have configured:
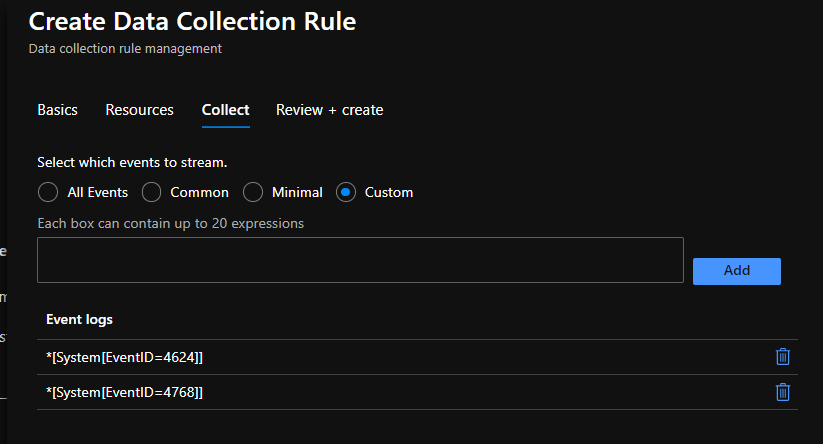
I have tried various xpath queries already but none seem to be collecting the data.
Any ideas?
Br,
Jasper

