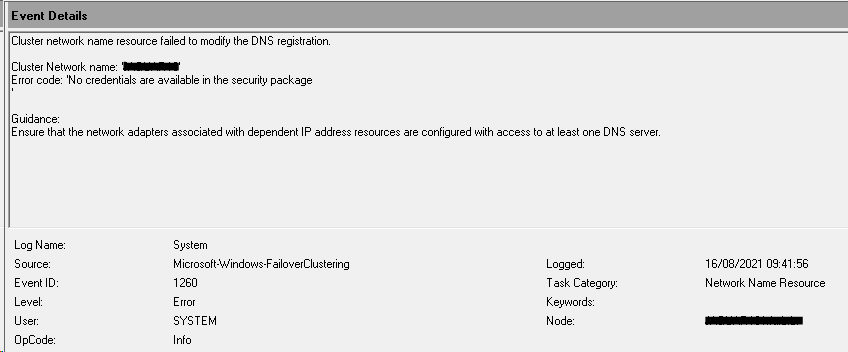
So we have had this same issue that i have battled for a month, checking literally every nook and cranny relating to security, authentication, and DNS. I finally found the root cause, and I wanted to get this out there since our env is identical in regards to using gMSA on 2012r2 for ad.
TLDR: in my case, it is KB related. KB5006672, KB5005568, KB5005030, and KB5004244 all cause this. It is really easy to test as well for anyone who wants to confirm:
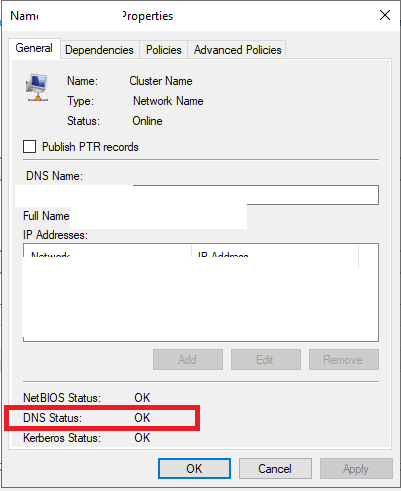
In your failover cluster manager, double click on your cluster under cluster core resources to check dns status:
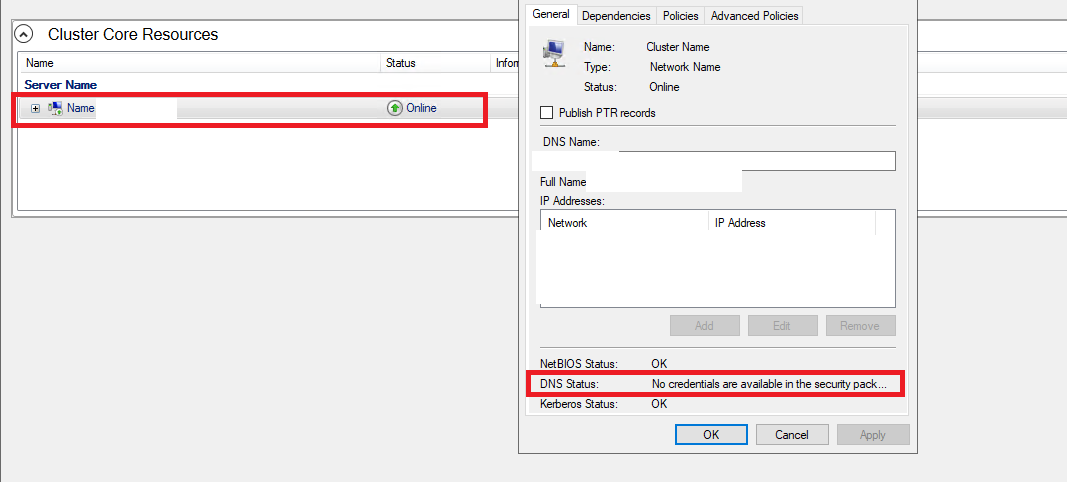
This will be your confirmation check after uninstalling each KB.
Uninstall any KB's that are mentioned. It looks like it started happening in july of 2021 the earliest. Preview cumulative updates can also potentially hold this problem.
After uninstall, if DNS shows OK, that was the root cause. please note that since these are cum sec updates, and further monthly updates can potentially cause as well.
I also tested this on a sandbox ADDS .local domain that was on server 2019 with AD most up to date. The thinking was since (my/the) environment is security heavy, a GPO could have been causing the issues. We confirmed that is not the case and just used an out of the box domain w/o any GPO's whatsoever, and still reproduced the DNS cred missing problem with said KB articles.
Hope this helps.
PS: if this does end up fixing anyones problem (as of november 9th, 2021), please open a ticket with microsoft and share your findings. The more light people can shed, the better.
edit: our environment was AD on 2012r2, and cluster was on server 2019 using group managed service accounts.
also tested on an "out-of-the-box" test AD environment with only default settings on server 2019, and reproduced the issue confirming it was windows update related.