@SwathiDhanwada-MSFT Thank you for your time.
To make non-complaint resources complaint, you need to go to respective resource and install the extensions
- My understanding was that the policy checked for 'installed' extensions against a list of "allowed" extenions, and highlighted/failed those that
were not previously defined in the policy exemptions.
is there a requirement that the extenison is also installed? ( I cant see this to be true as, for example, there would be no need to install
"SqlIaasExtension" on a non-SQL VM). But you would need to add it to the policy exclusions for the applicable VM's. - Please Clarify.
Which effect are you using for this Policy (Audit , Deny, Disabled)
Audit
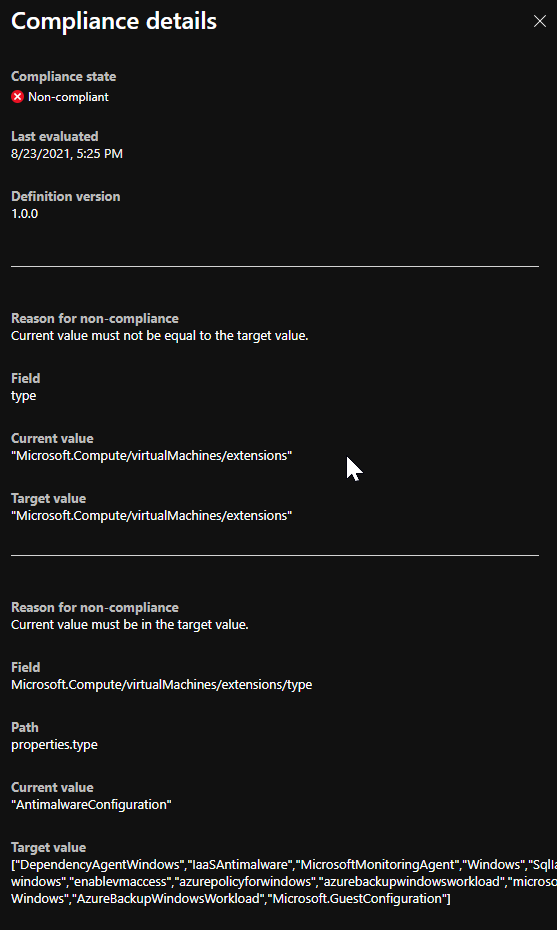
- Screenshot
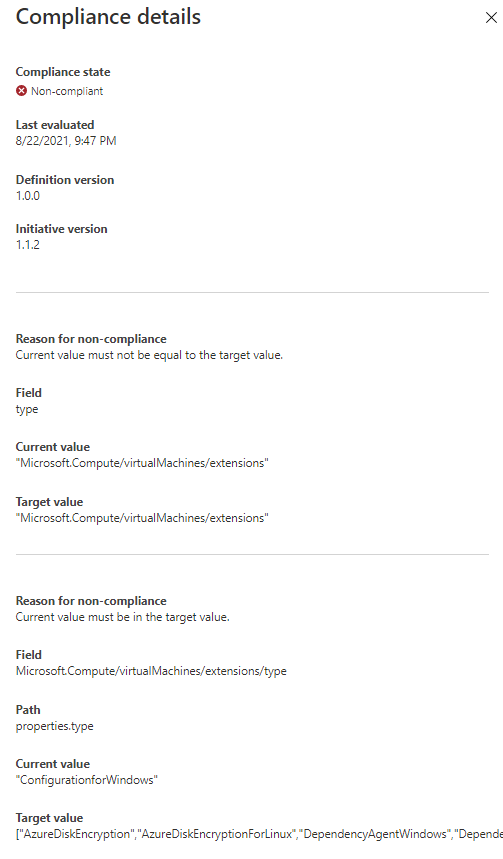
Although not shown in the screenshot, the extension is clearly listed (1st post 7th parameter). This is the same with all of the "non-compliant" extensions - they have all been added to parameters however are still showing as non-compliant.