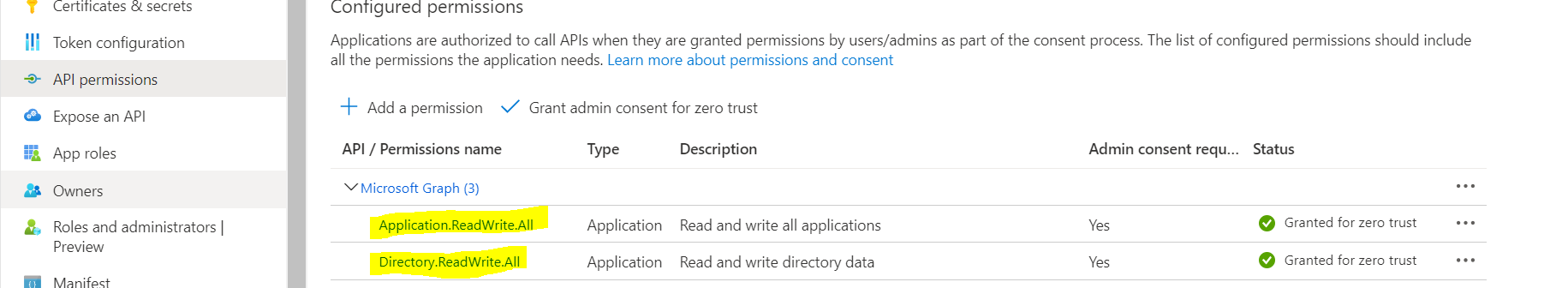
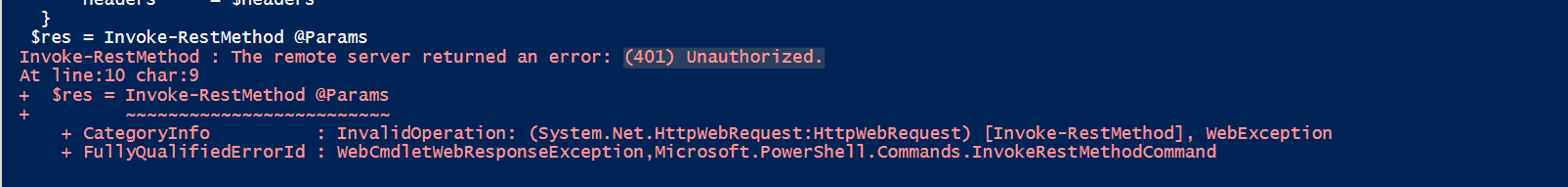
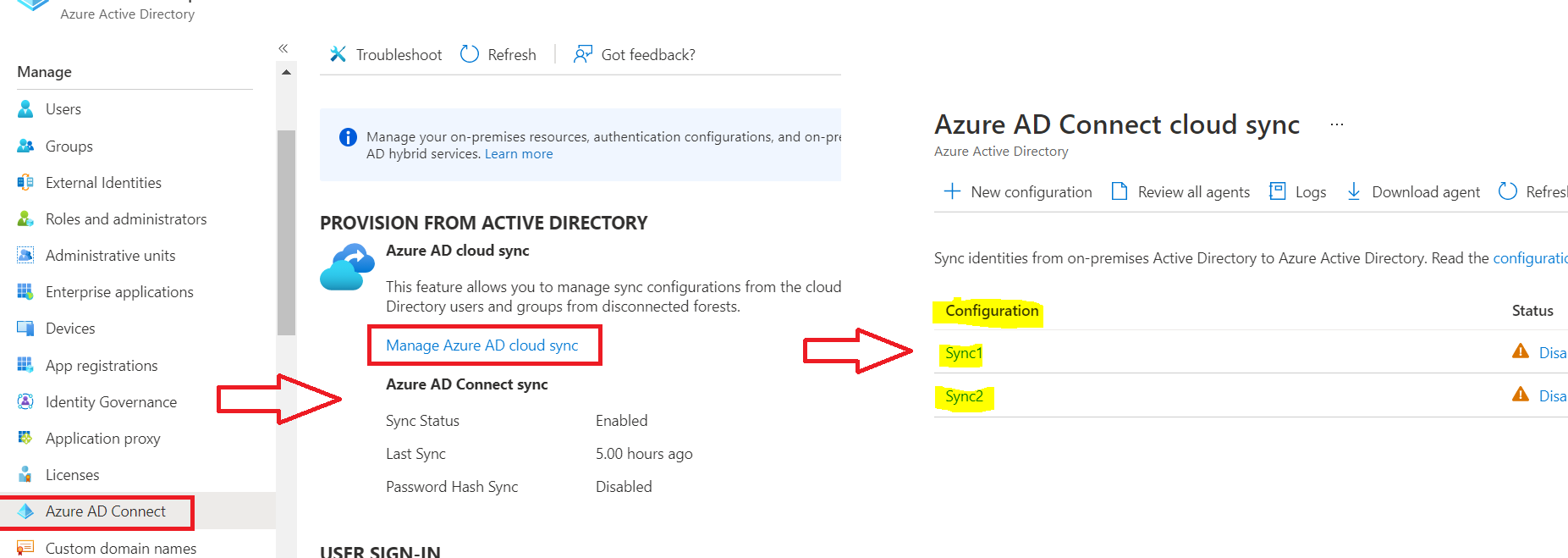
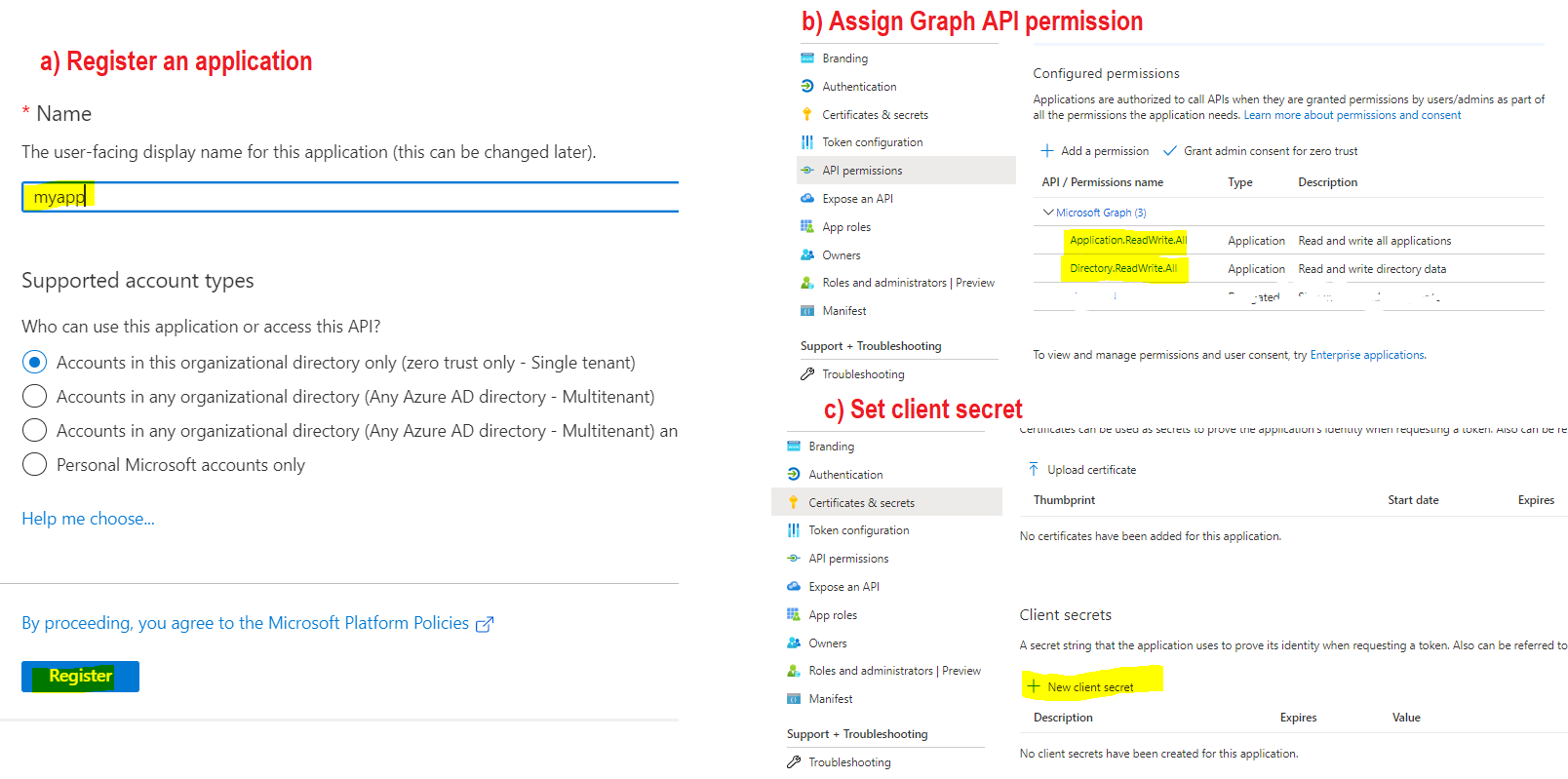
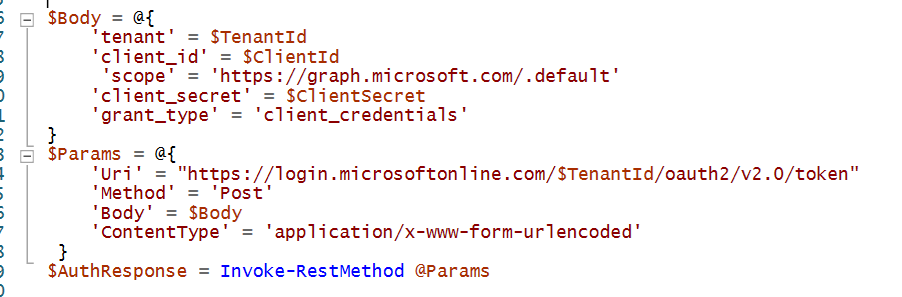
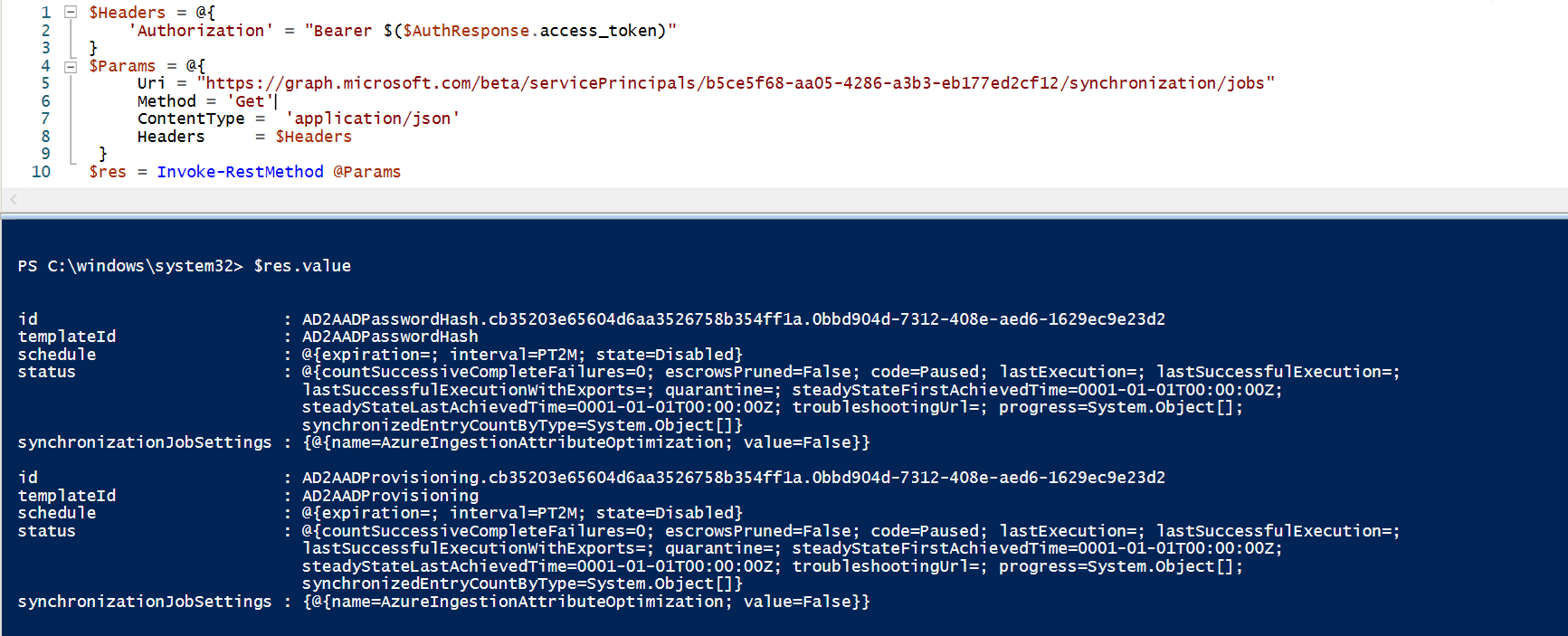
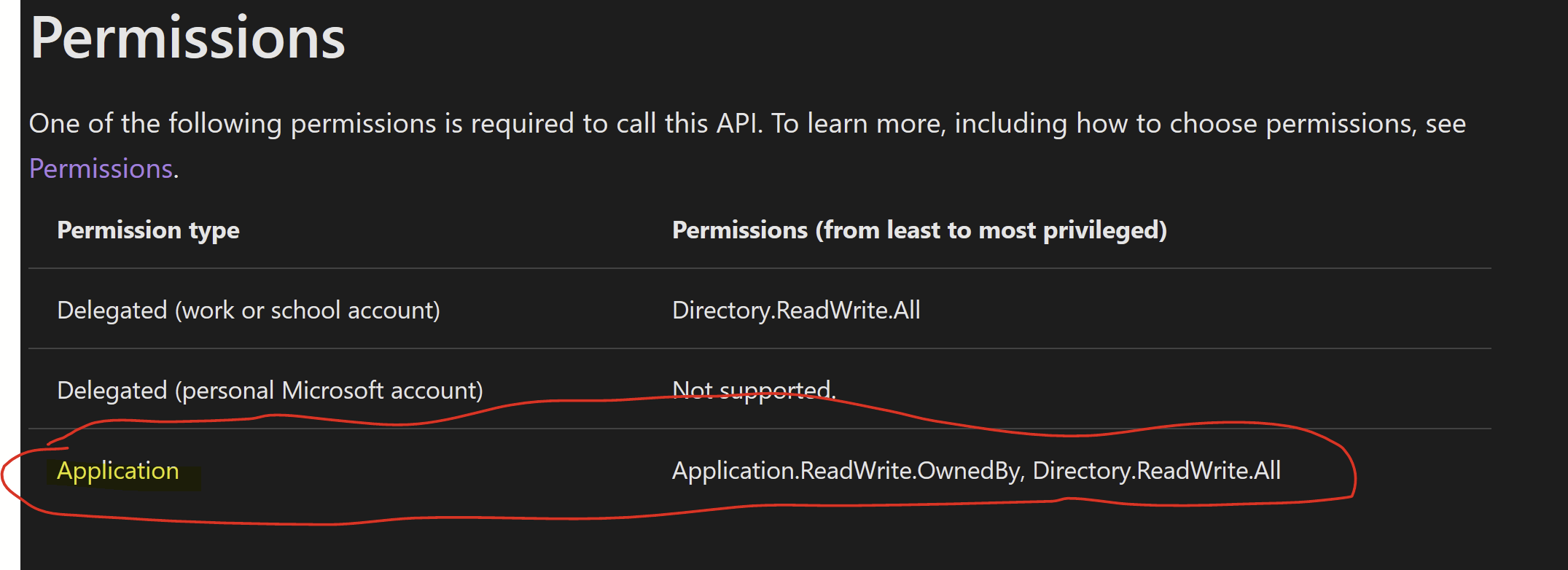
EDIT: The service principal needs the role "Hybrid Identity Administrator" (or Global administrator) for this to work!
Another way with user creds, ROPC flow (username/password) this user also needs Hybrid Identity Admin role:
$Body = @{
'tenant' = $TenantId
'client_id' = $ClientId
'scope' = 'https://graph.microsoft.com/.default'
'username' = $Username
'password' = $Password
'grant_type' = 'password'
}
$Params = @{
'Uri' = "https://login.microsoftonline.com/$TenantId/oauth2/v2.0/token"
'Method' = 'Post'
'Body' = $Body
'ContentType' = 'application/x-www-form-urlencoded'
}
$AuthResponse = Invoke-RestMethod @Params