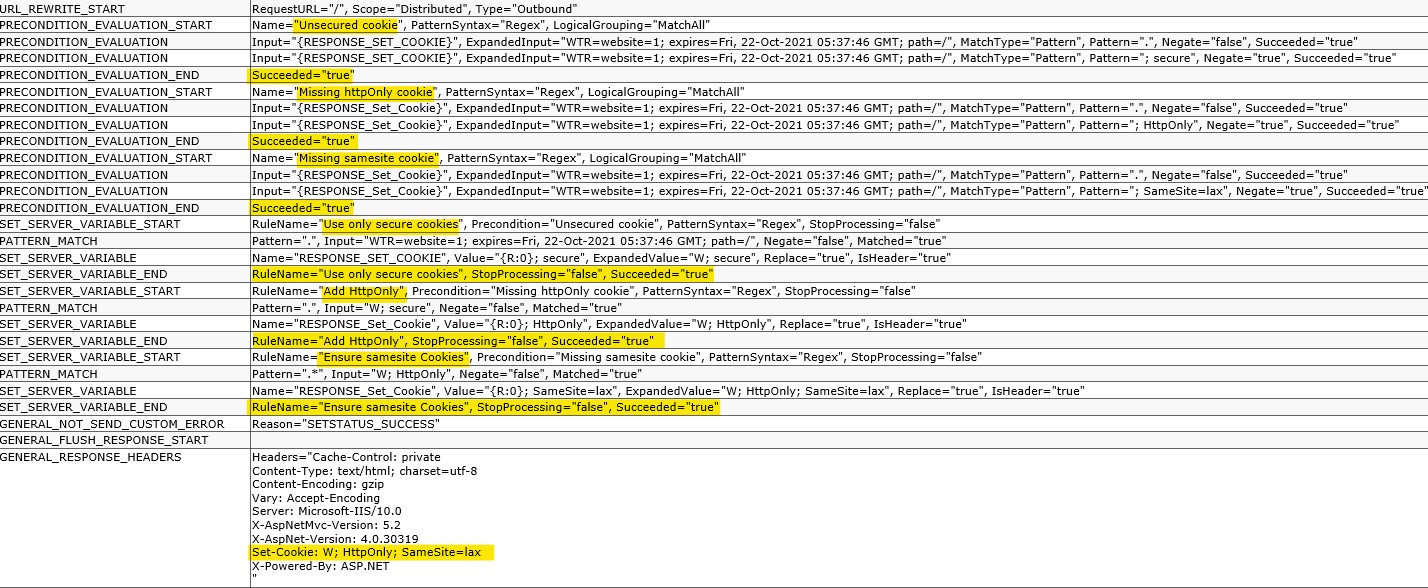
I hosted an angular JS application on windows IIS, when i viewed the application cookies on CHROME DEVELOPER TOOL, i noticed that some cookies were not set to HTTPONLY and SameSite not set to lax, meanwhile got some articles online on how to secure cookies which i used on my web.config yet am still getting some cookies HTTPONLY and samesite not set. Secondary i did not use any cookies on the application. Below is my web.config code.
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="Angular Routes" stopProcessing="true">
<match url="." />
<conditions logicalGrouping="MatchAll">
<add input="{REQUEST_FILENAME}" matchType="IsFile" negate="true" />
<add input="{REQUEST_FILENAME}" matchType="IsDirectory" negate="true" />
</conditions>
<action type="Rewrite" url="./index.html" />
</rule>
<rule name="IbankRedirecturl" stopProcessing="true">
<match url="(.)" />
<conditions>
<add input="{HTTPS}" pattern="^OFF$" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}{REQUEST_URI}" appendQueryString="false" />
</rule>
</rules>
<outboundRules>
<rule name="Use only secure cookies" preCondition="Unsecured cookie">
<match serverVariable="RESPONSE_SET_COOKIE" pattern="." negate="false" />
<action type="Rewrite" value="{R:0}; secure" />
</rule>
<rule name="Add HttpOnly" preCondition="Missing httpOnly cookie">
<match serverVariable="RESPONSE_Set_Cookie" pattern="." negate="false" />
<action type="Rewrite" value="{R:0}; HttpOnly" />
</rule>
<rule name="Ensure samesite Cookies" preCondition="Missing samesite cookie">
<match serverVariable="RESPONSE_Set_Cookie" pattern=".*" negate="false" />
<action type="Rewrite" value="{R:0}; SameSite=lax" />
</rule>
<preConditions>
<preCondition name="Unsecured cookie">
<add input="{RESPONSE_SET_COOKIE}" pattern="." />
<add input="{RESPONSE_SET_COOKIE}" pattern="; secure" negate="true" />
</preCondition>
<preCondition name="Missing httpOnly cookie">
<!-- Don't remove the first line! -->
<add input="{RESPONSE_Set_Cookie}" pattern="." />
<add input="{RESPONSE_Set_Cookie}" pattern="; HttpOnly" negate="true" />
</preCondition>
<preCondition name="Missing samesite cookie">
<!-- Don't remove the first line here, it does do stuff! -->
<add input="{RESPONSE_Set_Cookie}" pattern="." />
<add input="{RESPONSE_Set_Cookie}" pattern="; SameSite=lax" negate="true" />
</preCondition>
</preConditions>
</outboundRules>
</rewrite>
<httpProtocol>
<customHeaders>
<!-- SECURITY HEADERS - https://securityheaders.io/? -->
<!-- Protects against Clickjacking attacks. ref.: http://stackoverflow.com/a/22105445/1233379 -->
<add name="X-Frame-Options" value="SAMEORIGIN" />
<!-- Protects against Clickjacking attacks. ref.: https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet -->
<add name="Strict-Transport-Security" value="max-age=31536000; includeSubDomains"/>
<!-- Protects against XSS injections. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-XSS-Protection" value="1; mode=block" />
<!-- Protects against MIME-type confusion attack. ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/ -->
<add name="X-Content-Type-Options" value="nosniff" />
<!-- CSP modern XSS directive-based defence, used since 2014. ref.: http://content-security-policy.com/ -->
<!--<add name="Content-Security-Policy" value="default-src 'unsafe-inline'; font-src *;img-src * data:; script-src *; style-src *;" />-->
<add name="Content-Security-Policy" value="default-src 'unsafe-inline' 'self' https://ibankapi.lotusbank.com https://ibank.lotusbank.com; script-src 'unsafe-inline' 'self' https://ibank.lotusbank.com" />
<!-- Prevents from leaking referrer data over insecure connections. ref.: https://scotthelme.co.uk/a-new-security-header-referrer-policy/ -->
<add name="Referrer-Policy" value="strict-origin" />
</customHeaders>
</httpProtocol>
</system.webServer>
<system.web>
<!--<httpCookies httpOnlyCookies="true" sameSite="Strict" requireSSL="true" />-->
</system.web>
</configuration>