I did some more work on this and found I was selecting the wrong setting in NPS.
When going to <Network Policy Name> > Settings tab > chose Standard under RADIUS Attributes.
Click Add
Select Service-Type
Under Attribute Value: select Other
In that drop down select Administrative
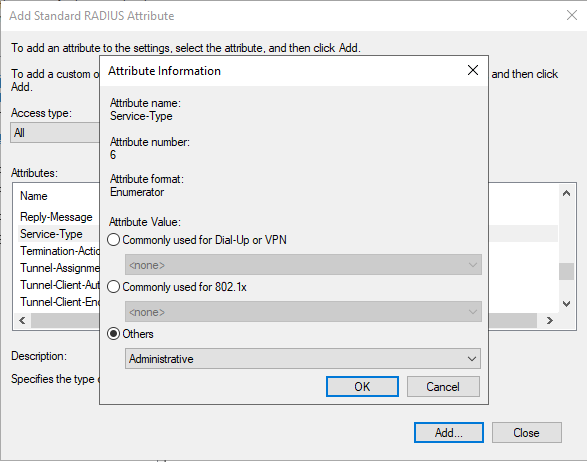
As seen in that screen shot, Service-Type is an Enumerated Value, which is what Cisco ASAs need for the RADIUS response.
The debug on the ASA also confirms the correct value. For those having this same issue, this can be found by doing a "debug radius all" and searching for "Service Type". If your Service-Type response is not exactly like this, then auto-enable will not work.
Radius: Type = 6 (0x06) Service-Type
Radius: Length = 6 (0x06)
Radius: Value (Hex) = 0x6
Additionally, on the Cisco ASA, you will need the following command if it is not already configured.
aaa authorization exec authentication-server auto-enable

