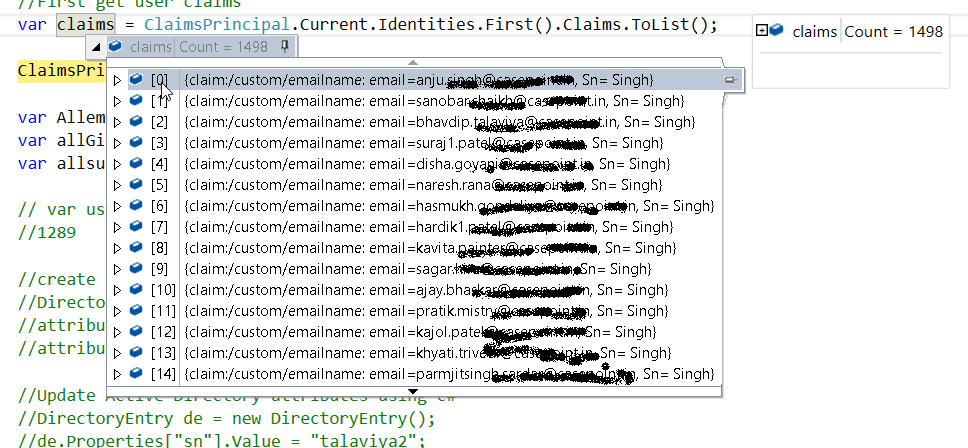
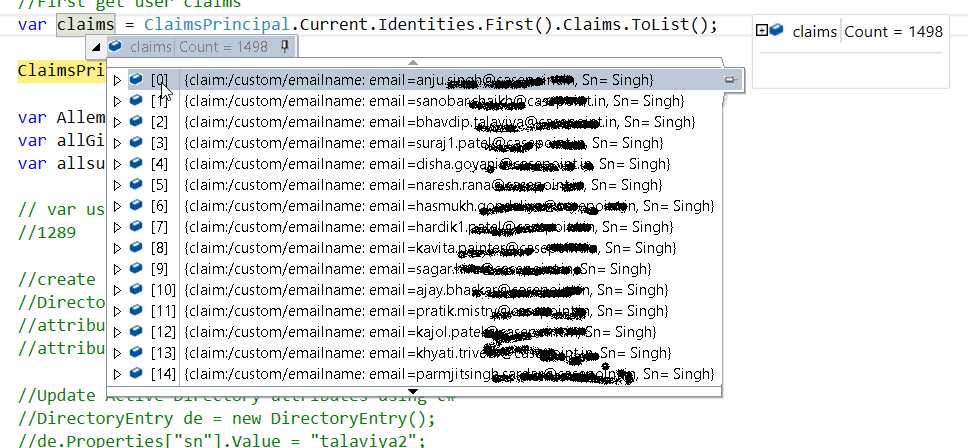
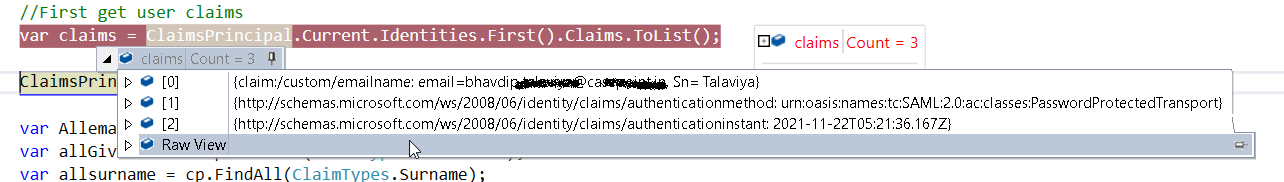
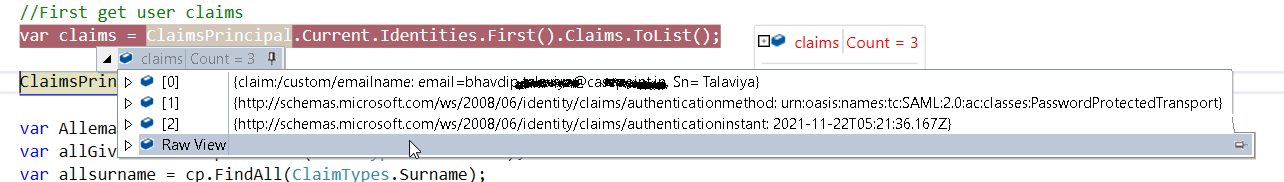
hi @Pierre Audonnet - MSFT I am not asking for the access token,
But it is about access token. The only point of the issuance rules is to "issue" claims that go into the access token.
The query you are doing are returning things for all users. Why would an access token have the list of all users and and all email addresses?
@Pierre Audonnet - MSFT when I am using the below query in custom claim it will return all uses so basically I need all users so I use the below query: (&(objectClass=user)(objectCategory=person))
You should not query info about other accounts than the one you are authenticating unless that information is then used for authorization by the relying party trust. But why would an application want all users info to authorize 1 user? There is very likely a misconception somewhere.
In the first rule I suggested:
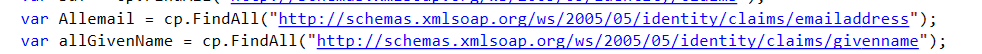
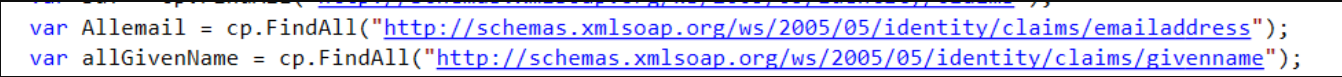
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> add(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname"), query = ";mail,givenName;{0}", param = c.Value);
There is no LDAP filter. So we just get the attributes mail and givenName from the user. A bit like if you were doing a "base" LDAP search on the current user. For we can concatenate them like I suggested without worrying about multi-values.
For the sake of the exerice of thought, if you retrieve a multi-value attribute from the AD attribute store, you won't be able to map it 1:1 with another attribute. You are essentially creating two distinct arrays. If "array1" = value1, value2 and "array2" = valueA, valueB doing the concatenation of "array1" and "array2" into a new claim called "stringConcat" will effectivly create a multi-values claim with all possibilities.
"stringConcat" = value1valueA, value2valueA, value1valueB, value2valueB
In certain cases we can use "dynamic" claim types and make it work. But the AD attribute doesn't support those. With this one, you can only add/issue claims by specifying their claim type with a string (no dynamic values).
So, let's step back and restate... What do you need? and why (what does the application need to do with the data)?