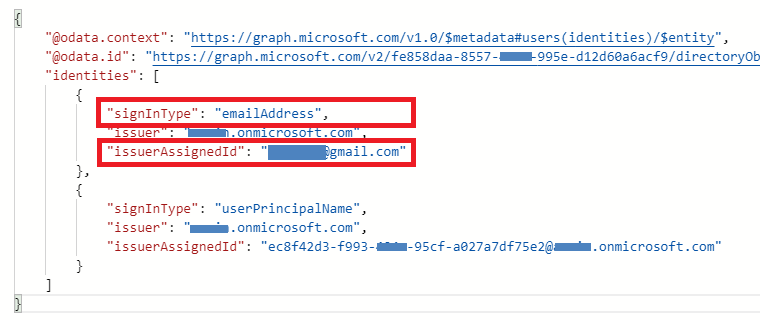
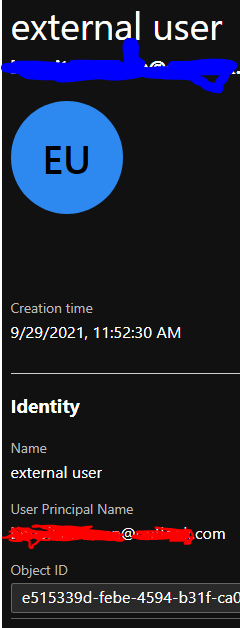
Hi @Benoit Hoffman • Unfortunately, the Username is not stored in the B2C directory by default for the users who signup using federated IDP. Refer to the screenshot below for the user I signup via federated IDP, notice the empty user principal name:
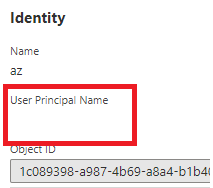
In this case, if you want to store the UPN of the users, you may consider creating a custom attribute like "extension_upn" and configure your signup policy to auto populate the value of this attribute by using preferred_username claim in the token during claims exchange with federated IDP at signup by adding below output claim in the technical profile of the federated IDP.
<OutputClaim ClaimTypeReferenceId="extension_upn" PartnerClaimType="preferred_username" />
Note: preferred_username is the claim name used by Azure AD for UPN. Other IDPs may use different name.
Refer to Add user attributes and customize user input in Azure Active Directory B2C for more details and don't forget to read the important note.
See this in action:
Go to https://b2c.cloud365.in, click on Azure AD button and sign-in with your Azure AD user account. Notice your UPN will be pre-populated in the extension_upn field.
For users who have already signed-up, this needs to be updated by using profile editing flow.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.