The right events are 4624 (LOGON) and 4634(LOGOFF).
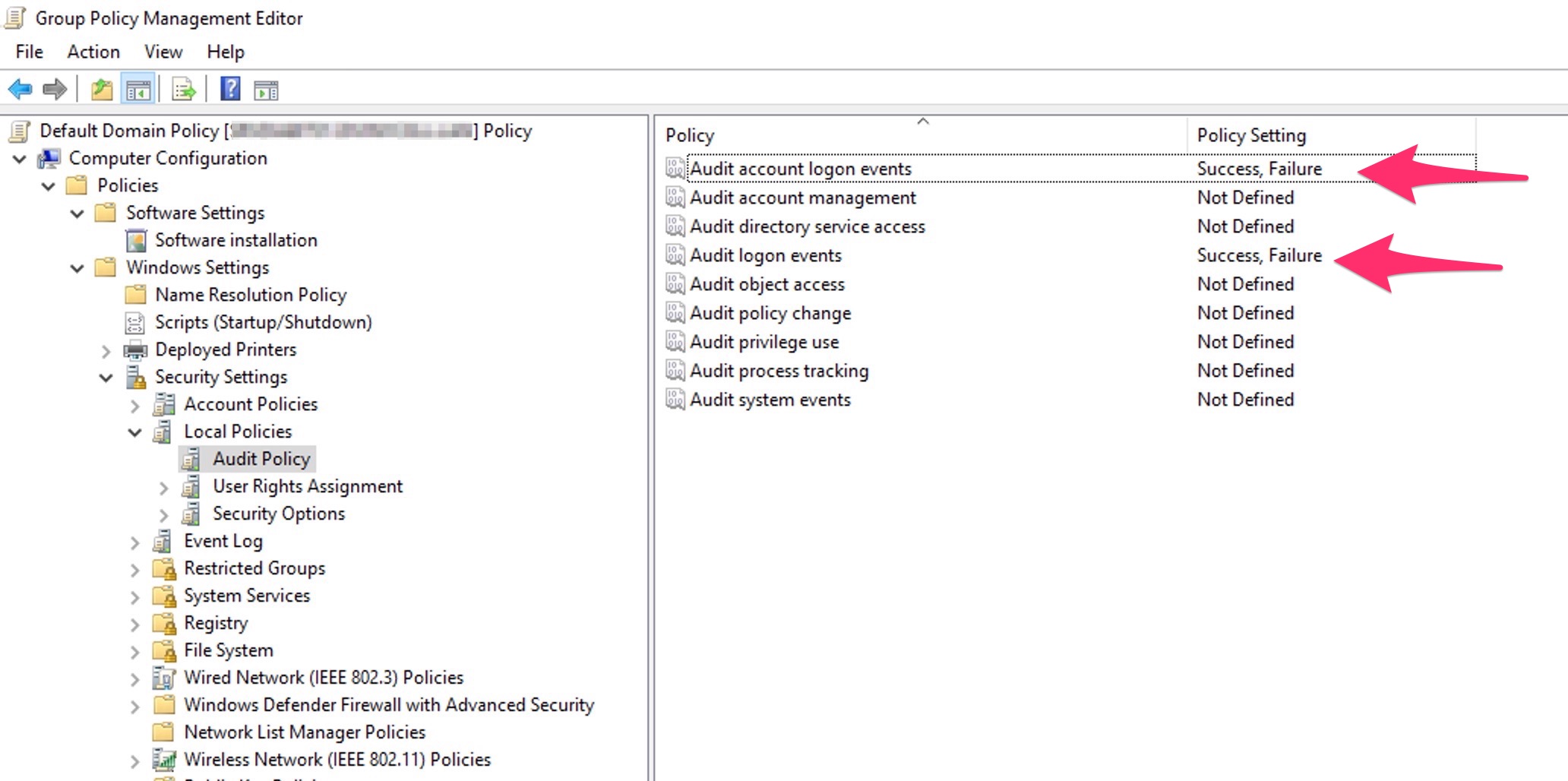
If you need to see the type 10, you must enable enable the ‘Audit Logon Events’ and ‘Audit Account Logon Events’ trought a GPO.
Enable them for example on the "Default Domain Policy", do a refresh from your DC (open a CMD with admin rights and do REPADMIN /Syncall /AdeP ) .
You will see the 4624
A good guide about them : event-4624

