Hello @SenhorDolas
Check the links below that they have a problem similar to yours and I believe it will be useful to help you solve the problem:
-------------
--If the reply is helpful, please Upvote and Accept as answer--
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi Everyone,
I need to renew my root certificate and I don't have a clue how to do this correctly. My DC's are 2012 R2 and 2019 and my AD DFL and FFL are: Windows Server 2012 R2, clients are all W10 and servers mostly 2008 and above and a tiny amount of 2003.
1. Is there a step-by-step guide on how to do this?
2. What gotchas show I look out for?
3. Do I need to change the cert signature algorithm from SHA1 to SHA256 or can I keep the same?
4. How can I check where the root cert is used (so I can update these 3rd party systems)
5. How can I test the renewed cert?
6. Is there a rollback option?
Would anyone be able to share their knowledge on this pls?
Many Many Thanks, M

Hello @SenhorDolas
Check the links below that they have a problem similar to yours and I believe it will be useful to help you solve the problem:
-------------
--If the reply is helpful, please Upvote and Accept as answer--
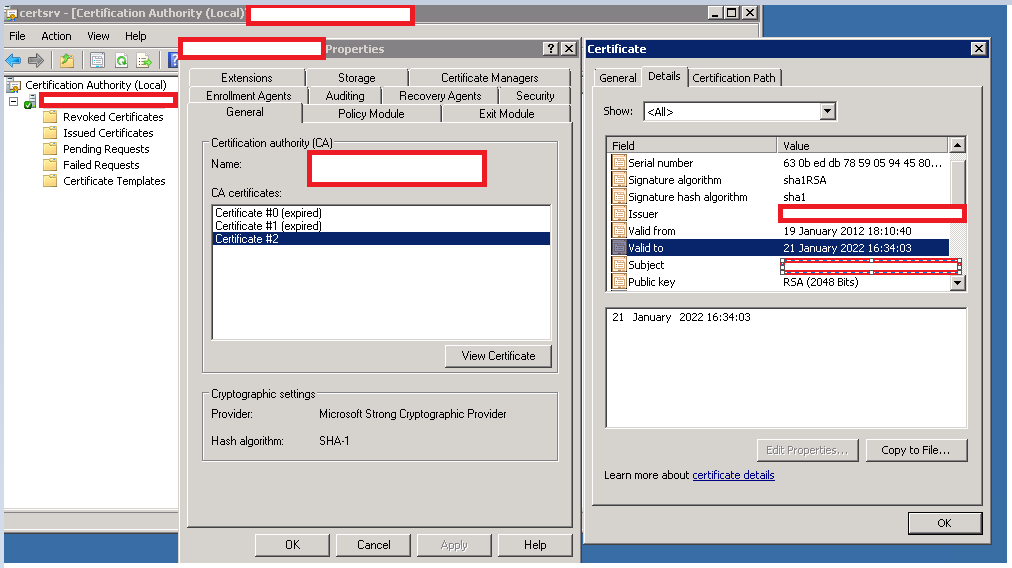
Renew CA certificate
For this task, open the context menu of the Certification Authority in certsrv.msc, and select the Renew CA Certificate option under All Tasks.
Renew CA certificate via the MMC snap in Certification Authority
This action launches a wizard, which first announces that certificate services need to be temporarily stopped. The next dialog box allows the user to choose whether to retain the signing keys or generate new ones.
Microsoft names compromised existing keys, specific software requirements, or an overly long certificate revocation list (CRL) as possible reasons for generating new keys.
With new keys, the certification authority also creates a new CSR that only contains the serial numbers of certificates revoked since the issuance of the new CA certificate. Microsoft's documentation explains how this affects the naming of the CRL.
Retaining the keys simplifies the process because it keeps all previously issued certificates chained up to the new CA certificate. For an in-depth discussion of the pros and cons of new signing keys, refer to this blog post by Vadims Podāns.
As an alternative to the certsrv.msc GUI, you can use the certutil.exe utility to renew the CA certificate while retaining the existing public and private keys:
certutil -renewCert ReuseKeys
Renew the CA certificate with certutil.exe while reusing the previous keys
If you omit the ReuseKeys switch, the utility also creates new keys. With the following entry in the abovementioned CaPolicy.inf, you can set the key length, in this example to 2048 bits:
RenewalKeyLength=2048
Distribute the root certificate to the clients
After renewing the root CA certificate, you must deploy it to the clients to make them trust all certificates issued by the certification authority. Windows PCs store this certificate under cert:\LocalMachine\Root or under a user's trusted root certificates.
If you are running an enterprise CA, the root certificate is automatically distributed within the domain. Clients receive it during the refresh of Group Policies. If you want to speed up this process, you can force a refresh using gpupdate /force.
In the case of a standalone CA, you have to export the certificate and publish it in Active Directory using the following command:
certutil -f -dspublish <RootCACertificate-File> RootCA
This method ensures that the root certificate is propagated to all machines in the domain. Alternatively, you can distribute the root certificate via Group Policy, especially if you want to provide it only to specific OUs.
To determine the type of CA you are dealing with, you can use the following method:
certutil -getreg ca\catype