Hello @Samuel Santos ,
Thanks for reaching out.
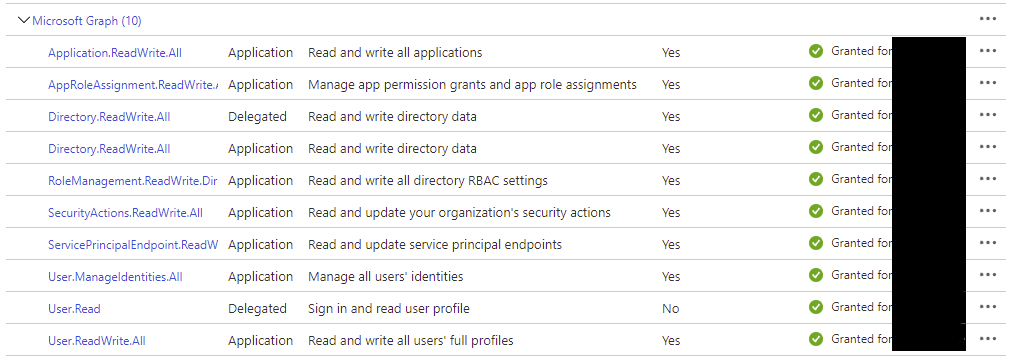
It seem to be acquired token was issued with following audience "Azure Active Directory Graph" https://graph.windows.net but you had configured above API permissions which are part of "Microsoft Graph" https://graph.microsoft.com/ not "Azure Active Directory Graph" hence HTTP 403 Authorization_RequestDenied is expected.
You can decode and verify AAD access_token from https://jwt.ms , you should see something like below for working scenario when you decode token:
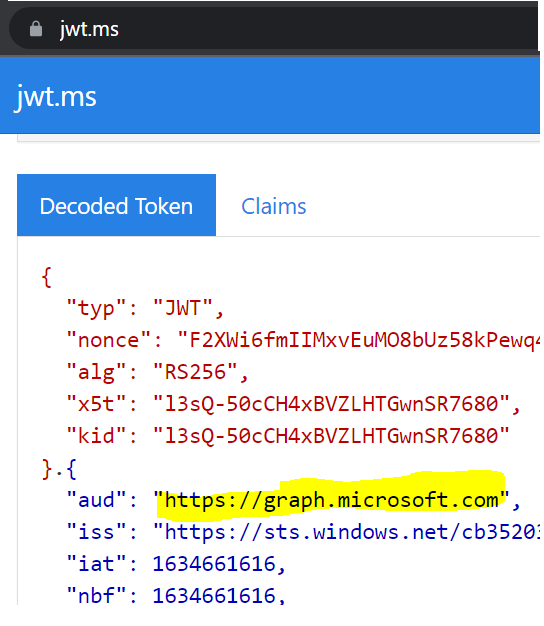
To fix the issue, either assign "Azure Active Directory Graph" API permission for App OR use tokenAudience as https://graph.microsoft.com/ in your code as explained here.
Note: Azure Active Directory Graph will be deprecated in June 2022. We recommend using Microsoft Graph APIs for your application
Therefore, when you use Azure SDK which build on MSAL library instead ADAL library for client to get token to call Microsoft Graph then above API permission should work.
ADAL example for Azure SDK module: https://learn.microsoft.com/en-us/javascript/api/overview/azure/activedirectory?view=azure-node-latest#client-package
ServicePrincipal interface : https://learn.microsoft.com/en-us/javascript/api/@azure/graph/serviceprincipal?view=azure-node-latest
Hope this helps.
------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.