Hi @Taranjeet Malik • Thank you for reaching out.
This can be done by creating a Named Location with the public IP Addresses and/or Subnets that represent your office network over the internet and marking the Named Location as Trusted. For this purpose, you need to navigate to:
Azure Active Directory > Security > Named Locations > +IP Ranges locations > Create & Mark the location as trusted, as highlighted below:
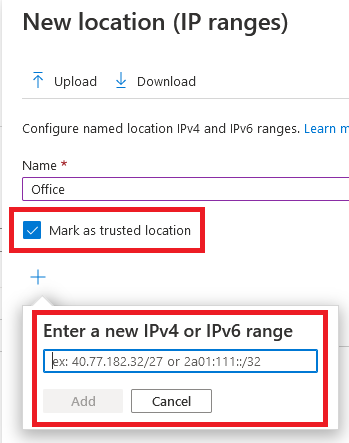
Once you have the Named location in place, you can create a conditional access policy to require MFA. In the policy, include all locations but exclude the Named location created in previous step or choose to exclude All trusted locations, as shown below:
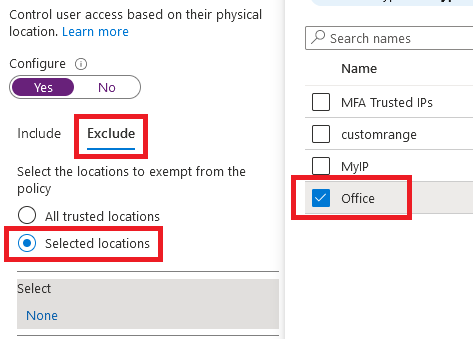
With this configuration, users will be prompted to do MFA if they access the protected cloud applications from any location except when they are inside the office.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
