Hi guys,
We've successfully updated to Exchange Server 2016 CU22 a few weeks ago. We're stuck at configuring the correct firewall rules. Normally it's just that easy: Accordind to the documentation (HelpConnectivityEEMS) permit all Exchange Servers access to officeclient.microsoft.com/* and you're done. In our case we're not. We noticed that the firewall blocks outbound connections on port 80. To me it looks quite ovious that the service tries to check the certificate for revocation. Normally the connection just times out, when a server is trying to access CRL on internet, but I guess in this case it's not the case because the service is security sensitive. Therefore I understand that the check for revocation must be successful. Ok, first we enabled unrestricted outbound access for the servers on port 80. Which worked, but we don't want to have the Exchange Servers unrestricted internet access on port 80. We've already tried to permit a bunch of well-known CRL URLs in addition to ip adresses blocked by the firewall, but we always get an error when using the get-mitigations.ps1 script:
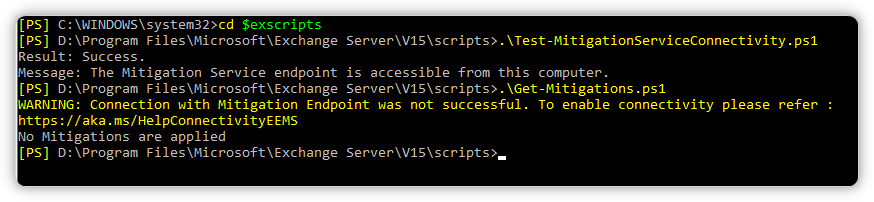
As you can see the Test-Script works (access to xml endpoint), but the get-mitigations.ps1 does not. In the Eventlog there's an error every hour:
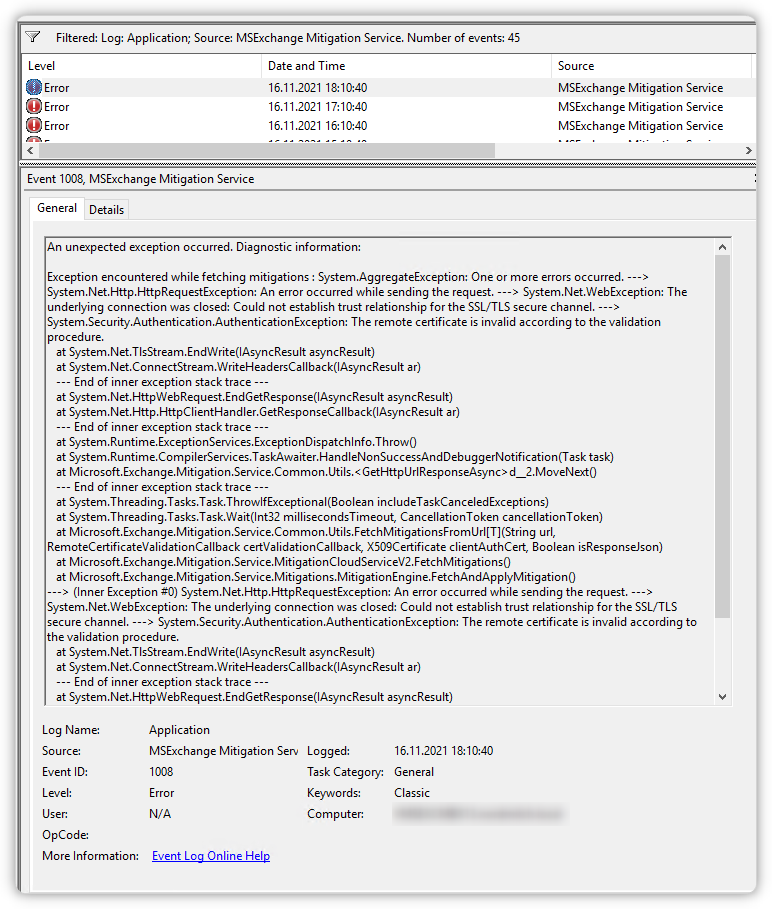
I could find any documentation which URLs are neccessary besides officeclient.microsoft.com. We also tested access through Zscaler proxy. That worked, too, but we don't want unauthorized access through Zscaler because it is paid ber load and not per user. Maybe that are URLs to which all clients should have access to, anyway!? Therefore I have following questions:
- Does anyone know which CRL URLs have to be permitted exactly to get the mitigation services working or does anywhere exist a general list?
- Do you just permit Exchange Servers port 80 outbound without restriction to any host?
Thanks for upcoming replies,
Daniel

