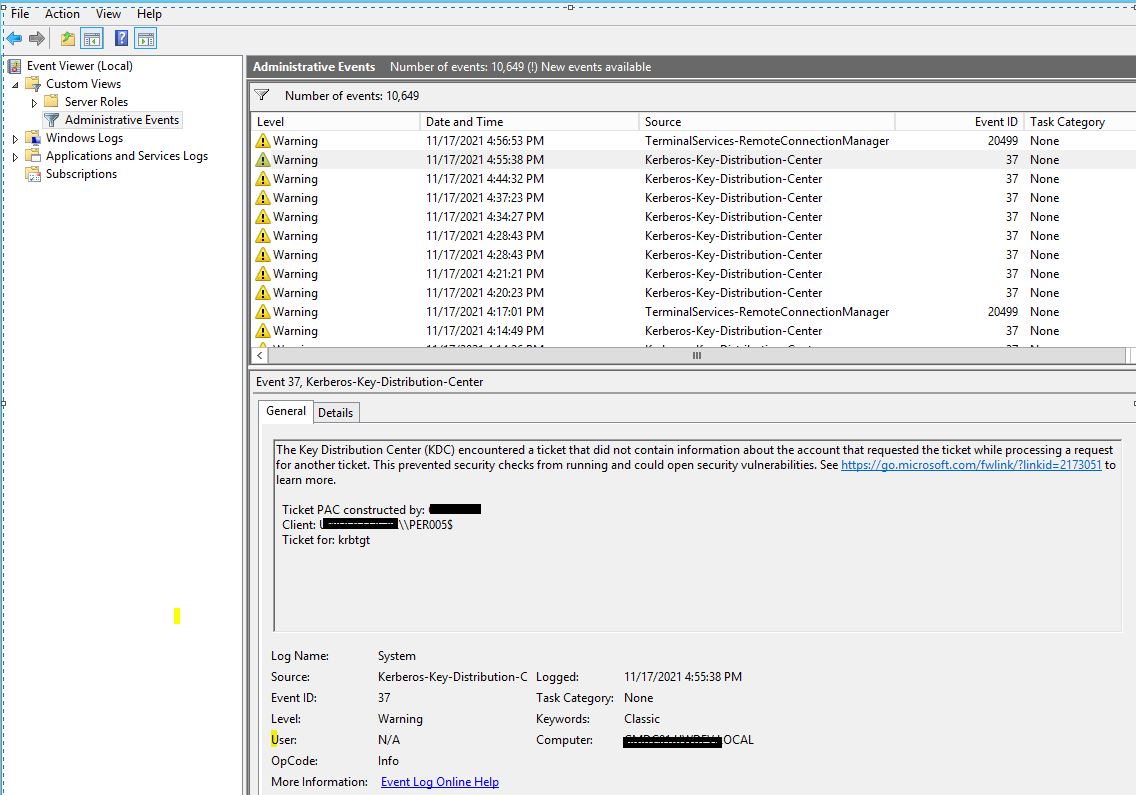
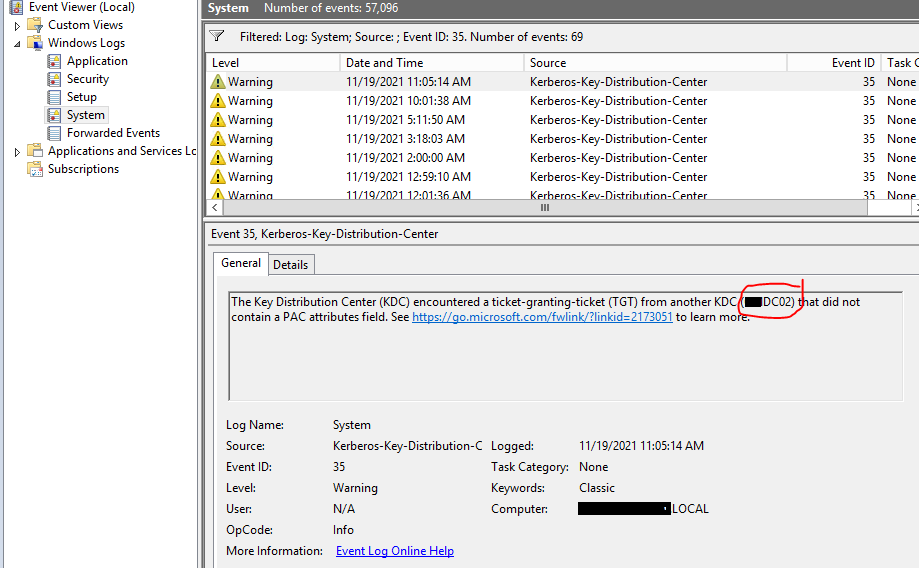
Hi @EcoAxis ,
There is a mentioning of authentication failures with certain Kerberos delegation scenarios over here:
https://learn.microsoft.com/en-us/windows/release-health/status-windows-10-1809-and-windows-server-2019#2748msgdesc
I suggest installing the latest November updates and check if it fixes the issue.
Here's an article about this:
https://www.bleepingcomputer.com/news/microsoft/new-microsoft-emergency-updates-fix-windows-server-auth-issues/
Here's also another forum thread about this:
https://community.spiceworks.com/topic/2338789-event-id-35-and-37-kerberos-on-server-2019
----------
If the reply was helpful please don't forget to upvote and/or accept as answer, thank you!
Best regards,
Leon