@Somnath Shukla ,
Yes, you can add the onPremisesSamAccount name to the claims and send it within an access token.
You can follow the steps mentioned below:
- Create an AzureADPolicy. New-AzureADPolicy -Definition @('{
"ClaimsMappingPolicy": {
"Version": 1,
"IncludeBasicClaimSet": "true",
"ClaimsSchema": [{
"Source": "user",
"ID": "employeeid",
"SamlClaimType": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/employeeid",
"JwtClaimType": "employeeid"
},
{
"Source": "user",
"ID": "mail",
"SamlClaimType": "http://schemas.microsoft.com/identity/claims/emailaddress",
"JwtClaimType": "mail"
},
{
"Source": "user",
"ID": "onpremisessamaccountname",
"SamlClaimType": "samaccountname",
"JwtClaimType": "samAccountName"
},
{
"Source": "user",
"ID": "department",
"SamlClaimType": "http://schemas.microsoft.com/identity/claims/department",
"JwtClaimType": "department"
}
]
}
}') -DisplayName "CustomClaimsPolicy1" -Type "ClaimsMappingPolicy"- Attach the newly created AzureADPolicy to a specific AzureAD App's Serviceprincipal for which the token would be requested for.
- To check if the policy is successfully added to the ServicePrincipal or not:
- Next you can use the Authorization Code flow of OAuth2.0 and request for a code from AAD.
- Once you have the code, use the code to request for an access token from AAD for the above app on whose ServicePrincipal the AzureADPolicy was added. [I used POSTMAN tool to test the same]
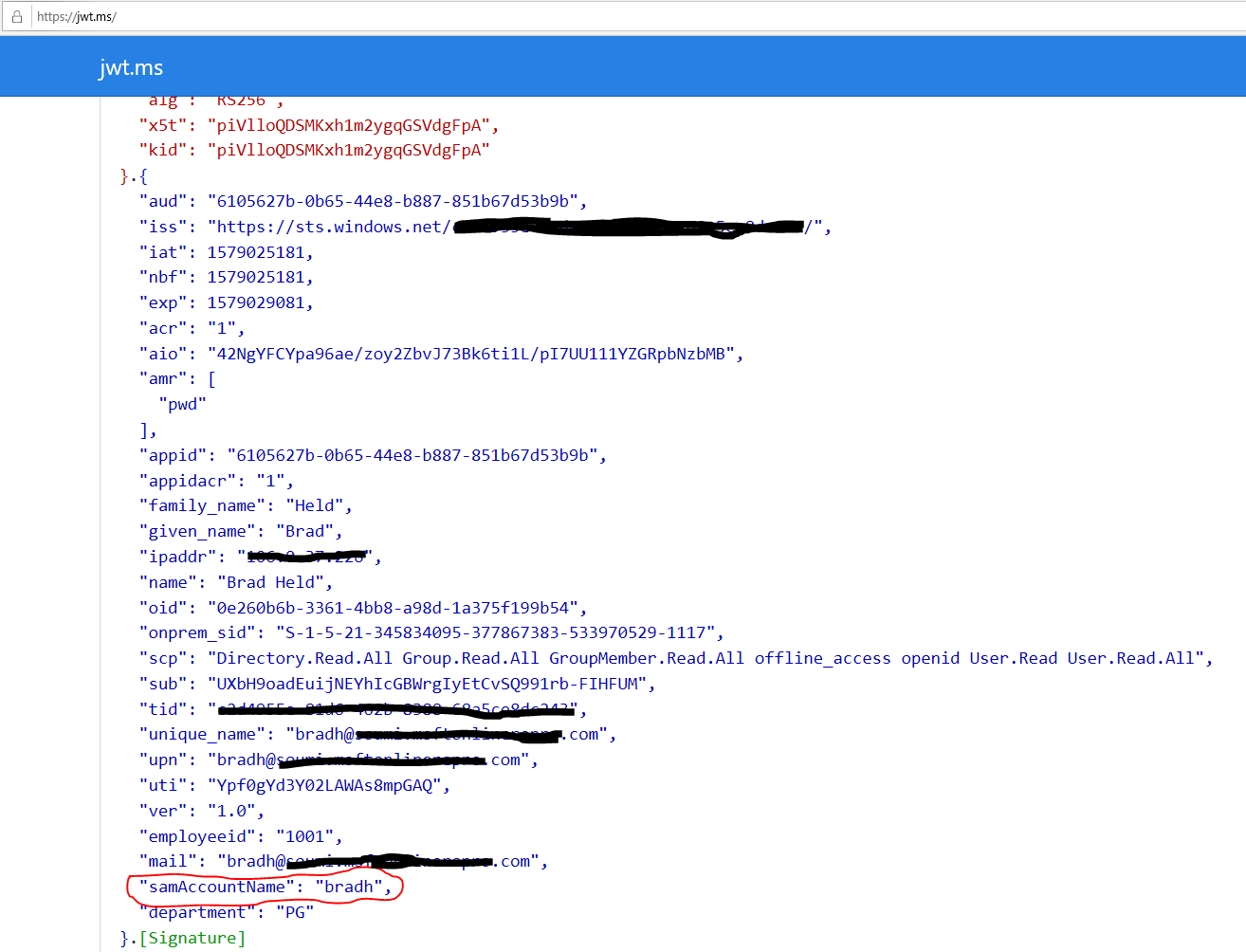
- Once you get the Access Token use https://jwt.ms to see the decoded JWT and you should see the SamAccountName listed in it as claims.
Hope this helps.
Please take a moment to "Mark as Answer" and/or "Vote as Helpful" wherever applicable. Thanks!
