Hello @bdiddy
After successful authentication, IDP issues id_token to the user. Along with the issuance of token, session cookies are also issued to facilitate SSO for web browser based sessions. If there are no session cookies present in the browser session or if cookies are expired, user is considered unauthenticated and he is required to authenticate, in order to get access to the protected resources. If session cookies present in the browser session, those cookies are passed in the request header to prove that the user is authenticated and has a valid session. Tokens are not stored on the browser.
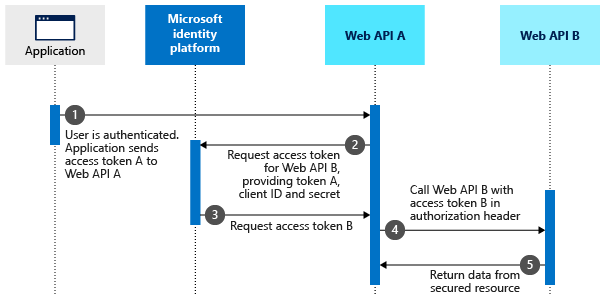
When we call an API, we need to pass the Access Token in the Authorization header. Id_token can be considered as a subset of Access Token and doesn't include the permissions/scopes which are usually required to perform the API call. Id_tokens are used to prove that the user is authenticated but to make API calls we need to prove that we have required permission to perform the Get/Post/Patch operation which is included in the Access Token.
For scenarios where one web api calls another web api, we pass Access Tokens in the Authorization header. Session cookies are not used in that case.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.

