Hello @Bertrand PERRET ,
Thank you for posting here.
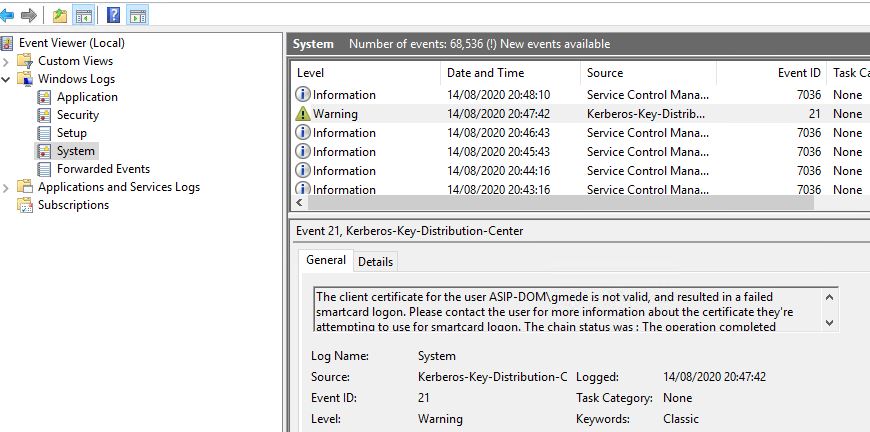
But now I have another error:
You cannot log on because the logon method you are using is not allowed on this computer. Please see your network administrator for more information.
A: For your error message, we can check as below:
If you log on this machine locally, we can check if we deny this account to logon this client locally through local group policy setting.
1.**On this machien, open **gpedit.msc (local group policy) and navigate to
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allowed log on locally (there should be Administrators group and the user account now we are using on this machine)
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny log on locally (it should be blank or there should be no Administrators group or no the user account now we are using on this machine)
**2.**If you log on this machine locally, we can check if we deny this account to logon this client locally through domain group policy setting.
Check the same setting on the domain GPO object:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allowed log on locally (there should be Administrators group and the user account now we are using on this machine)
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny logon locally (it should be blank or there should be no Administrators group or no the user account now we are using on this machine)
**3.**If we receive the error message above when we logon through remote desktop services, we can check if we deny this account to logon this client remotely through local group policy setting.
On this machine, open gpedit.msc (local group policy) and navigate to:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allow logon through Remote Desktop Services (there should be Administrators group and the user account now we are using on this machine)
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny logon through Remote Desktop Services (it should be blank or there should be no Administrators group or no the user account now we are using on this machine)
**4.**If we receive the error message above when we logon through remote desktop services, we can check if we deny this account to logon this client remotely through domain group policy setting.
Check the same settings on the domain GPO object:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Allow logon through Remote Desktop Services (there should be Administrators group and the user account now we are using on this machine)
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\Deny logon through Remote Desktop Services (it should be blank or there should be no Administrators group or no the user account now we are using on this machine)
For how to check 2&4 , we can check as below:
1.We can logon this machine with domain administrator.
2.Open CMD and run as Administrator.
3.Type gpresult /h C:\logon.html and click Enter.
4.Open the file above to check the group policy settings under "Computer Details".
Hope the information is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou