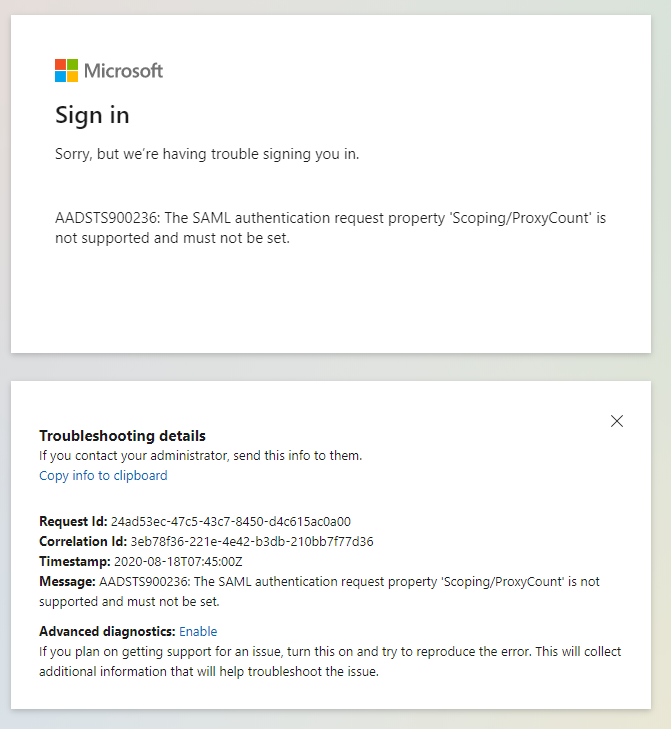
@JaparJarkynbyek , Thank you for reaching out. This error is coming up due to a non-supported value being set for the scoping element in the AuthnRequest. The following values for the scoping element are not supported by AAD.
- ProxyCount attribute
- IDPListOption
- RequesterID element
You can refer to this extract of the nonsupported saml authnRequest for your reference:
<saml:Issuer>https://terena.org/sp</saml:Issuer>
<samlp:NameIDPolicy
Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient"
AllowCreate="true"/>
<samlp:Scoping>
<samlp:RequesterID>https://eventr.geant.org/mellon/metadata</samlp:RequesterID> ----> <samlp:RequesterID> Not supported
</samlp:Scoping>
</samlp:AuthnRequest>
Moreover, the Scoping element, which includes a list of identity providers, is optional in AuthnRequest elements, You can try removing this from your AuthnRequest and then give it a try.
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.