Hello @Geetha ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
I understand that you have set up point to site VPN in Azure and are able to connect to the VM in the Vnet using private IP address but unable to connect to resources like storage account, azure app service and azure function which have private endpoints in the Vnet.
It's important to correctly configure your DNS settings to resolve the private endpoint IP address to the fully qualified domain name (FQDN) of the connection string.
You can use the following options to configure your DNS settings for private endpoints:
- Use the host file (only recommended for testing)
- Use a private DNS zone.
- Use your DNS forwarder (optional).
Refer : https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns
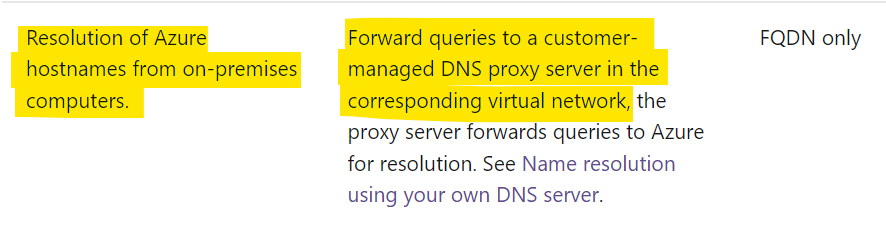
For on-premises workloads to resolve the FQDN of a private endpoint, you must use a DNS forwarder in Azure, which in turn is responsible for resolving all the DNS queries via a server-level forwarder to the Azure-provided DNS 168.63.129.16. A DNS forwarder is a Virtual Machine running on the Virtual Network linked to the Private DNS Zone that can proxy DNS queries coming from other Virtual Networks or from on-premises. A few options for DNS proxies are: Windows running DNS services, Linux running DNS services, Azure Firewall.
Reference : https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns#on-premises-workloads-using-a-dns-forwarder
If you check the table in Name resolution for resources in Azure virtual networks article, you can find the below:
https://learn.microsoft.com/en-us/azure/virtual-network/virtual-networks-name-resolution-for-vms-and-role-instances
Currently, there is no other way to accomplish this requirement as conditional forwarding isn't natively supported for Azure Private DNS but Azure Private DNS Zone resolution from On-premise is planned and is on the roadmap. You can vote for this feature in the below forum:
https://feedback.azure.com/d365community/idea/f50bd7e3-8526-ec11-b6e6-000d3a4f0789
So, for testing purpose, you can have host entry on your point to site client machine for the private endpoint with IP address.
eg: 10.1.0.4 storagename.privatelink.database.windows.net
But the recommended approach for production setups is to configure your on-premises DNS solution to forward DNS traffic to Azure DNS via a conditional forwarder that references the DNS forwarder deployed in Azure.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
