Hello @Guru V ,
Thanks for the question and using MS Q&A platform.
As I understand the ask here is that you want to know how to assign permissions to users from different tenant to a specific folder on your storage account to access the files.
If the users and you are in different tenant, then you need to invite as a Guest and add ACL's permissions to the respective storage account folders.
Here is another Q&A thread where a similar topic has been discussed - Is cross tenant blob access possible in azure?
ACLs give you the ability to apply "finer grain" level of access to directories and files. An ACL is a permission construct that contains a series of ACL entries. Each ACL entry associates security principal with an access level. To learn more, see: Access control lists (ACLs) in Azure Data Lake Storage Gen2.
In your case you don't have to give any RBAC's. A RBAC permission set can give a security principal a "coarse-grain" level of access such as read or write access to all of the data in a storage account or all of the data in a container.
Azure role assignments (RBACs) are evaluated first and take priority over any ACL assignments. If the operation is fully authorized based on Azure role assignment, then ACLs are not evaluated at all. That's because the system evaluates Azure role assignments first, and if the assignment grants sufficient access permission, ACLs are ignored. If the operation is not fully authorized, then ACLs are evaluated.
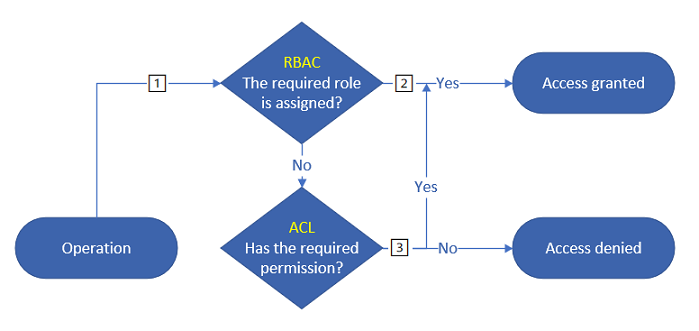
The following diagram shows the permission flow for three common operations: listing directory contents, reading a file, and writing a file.
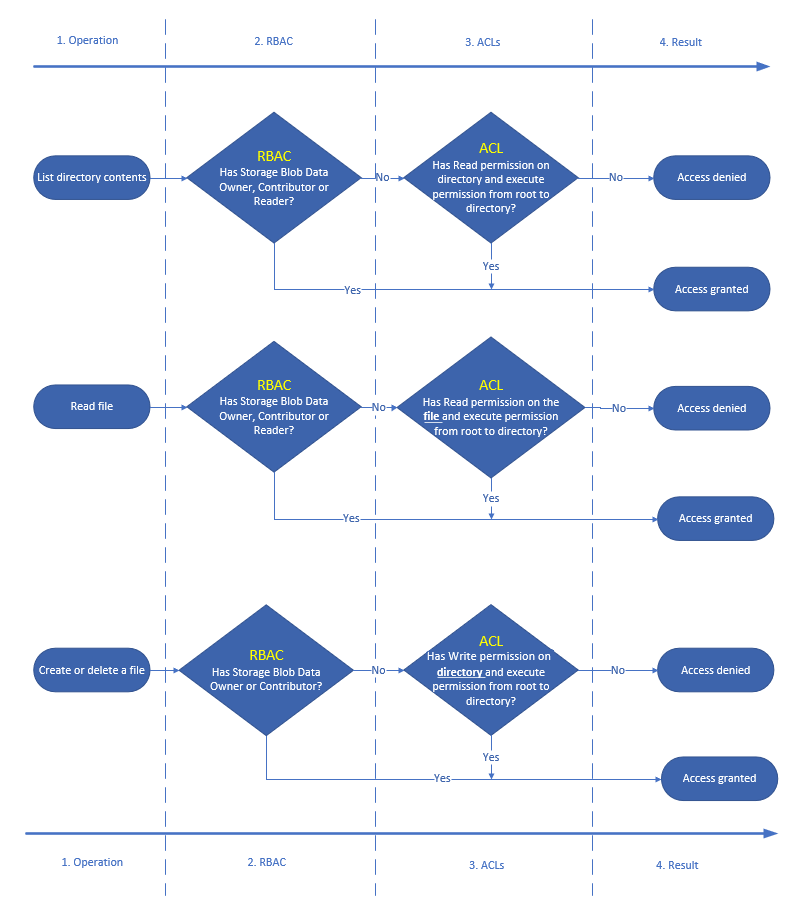
Here is a detailed explanation of how ACLs and RBACS are evaluated: Permissions table: Combining Azure RBAC and ACL
Hope this will help. Please let us know if any further queries.
------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators