Hello @SampathDilhan-7447
To get both Access and Refresh tokens, you would need to federate MSA IDP via OAuth with B2C. As of now, for OIDC IDPs only Access Token is passed through.
Please refer to below Technical Profile to add MSA IDP using OAuth:
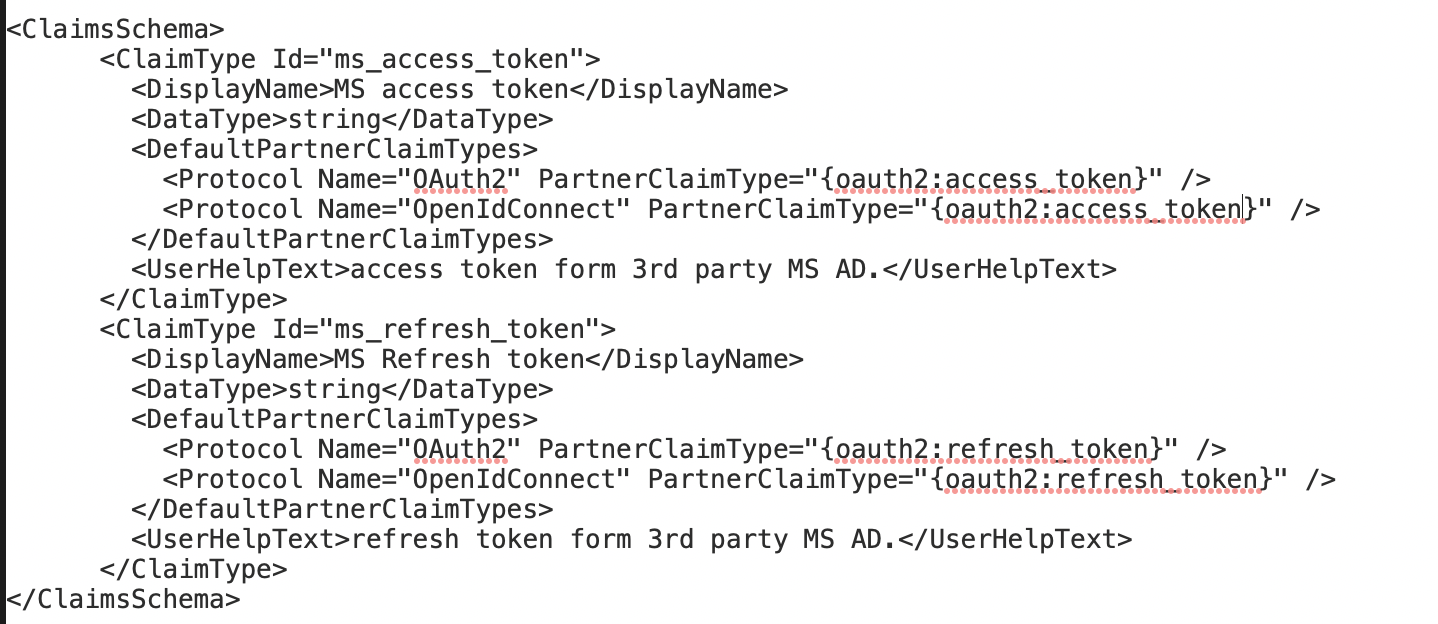
- Define Claim: <ClaimType Id="ms_access_token">
<DisplayName>MS access token</DisplayName>
<DataType>string</DataType>
<UserHelpText>access token form 3rd party MS AD. </UserHelpText>
</ClaimType>
<ClaimType Id="ms_refresh_token">
<DisplayName>MS Refresh token</DisplayName>
<DataType>string</DataType>
<UserHelpText>refresh token form 3rd party MS AD. </UserHelpText>
</ClaimType> - Define Technical Profile: <ClaimsProvider>
<Domain>live.com</Domain>
<DisplayName>Microsoft Account</DisplayName>
<TechnicalProfiles>
<TechnicalProfile Id="MSA-OAuth">
<DisplayName>Microsoft Account</DisplayName>
<Protocol Name="OAuth2"/>
<OutputTokenFormat>JWT</OutputTokenFormat>
<Metadata>
<Item Key="AccessTokenEndpoint">https://login.live.com/oauth20_token.srf</Item>
<Item Key="authorization_endpoint">https://login.live.com/oauth20_authorize.srf</Item>
<Item Key="ClaimsEndpoint">https://graph.microsoft.com/v1.0/me</Item>
<Item Key="ClaimsEndpointAccessTokenName">access_token</Item>
<Item Key="BearerTokenTransmissionMethod">AuthorizationHeader</Item>
<Item Key="client_id">XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX</Item>
<Item Key="HttpBinding">POST</Item>
<Item Key="scope">user.read offline_access</Item>
<Item Key="UsePolicyInRedirectUri">0</Item>
</Metadata>
<CryptographicKeys>
<Key Id="client_secret" StorageReferenceId="B2C_1A_MSASecret"/>
</CryptographicKeys>
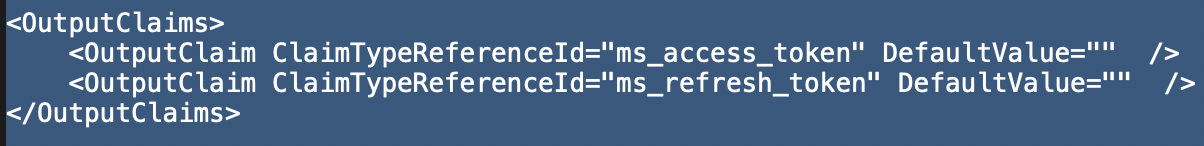
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="identityProvider" DefaultValue="live.com" />
<OutputClaim ClaimTypeReferenceId="authenticationSource" DefaultValue="socialIdpAuthentication" />
<OutputClaim ClaimTypeReferenceId="socialIdpUserId" PartnerClaimType="id"/>
<OutputClaim ClaimTypeReferenceId="displayName" PartnerClaimType="name" />
<OutputClaim ClaimTypeReferenceId="email" />
<OutputClaim ClaimTypeReferenceId="ms_access_token" PartnerClaimType="{oauth2:access_token}"/>
<OutputClaim ClaimTypeReferenceId="ms_refresh_token" PartnerClaimType="{oauth2:refresh_token}"/>
</OutputClaims>
<OutputClaimsTransformations>
<OutputClaimsTransformation ReferenceId="CreateRandomUPNUserName"/>
<OutputClaimsTransformation ReferenceId="CreateUserPrincipalName"/>
<OutputClaimsTransformation ReferenceId="CreateAlternativeSecurityId"/>
<OutputClaimsTransformation ReferenceId="CreateSubjectClaimFromAlternativeSecurityId"/>
</OutputClaimsTransformations>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-SocialLogin" />
</TechnicalProfile>
</TechnicalProfiles>
</ClaimsProvider>
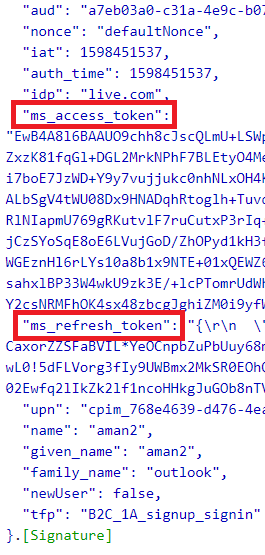
This will return both Access and Refresh tokens, as highlighted below:
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.