Hello,
Thank you so much for posting here.
Agree with Andy David, we could kindly have a check whether this user account is protected user, which is a member of the protected group.
For the users and groups that are members of the protected groups:
• Security inheritance is disabled
• The ACL on the user/group is replaced with the ACL from the AdminSDHolder object in the System container in AD (a smaller, much more restrictive ACL)
• The adminCount attribute on the user/group is set to 1.
For example:
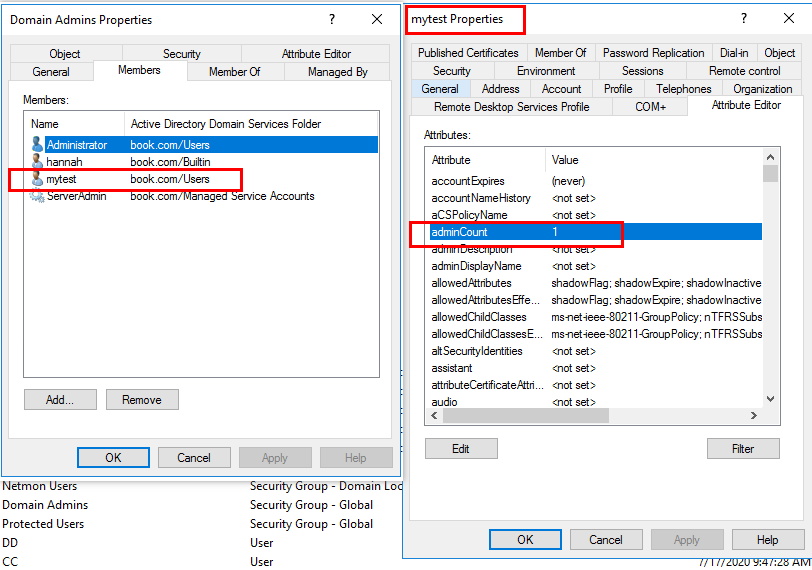
AdminSDHolder permissions apply to security principals that belong to protected groups. The Security Descriptor Propagation (SDPROP) process runs every hour on the domain controller holding the PDC emulator FSMO role. It is this process that sets the adminCount attribute to 1. The main function of SDPROP is to protect highly-privileged Active Directory accounts, ensuring that they can’t be deleted or have rights modified, accidentally or intentionally, by users or processes with less privilege.
If we reenable inheritance on the affected users and clear the adminCount attribute and the group membership that triggered those items being changed in the first place is still there, then SDPROP will revert our changes within the hour. So before cleaning up the permissions on these accounts, we need to ensure they are not affected by AdminSDHolder.
Here we would like to share more information with you:
https://learn.microsoft.com/en-us/previous-versions/technet-magazine/ee361593(v=msdn.10)?redirectedfrom=MSDN
For any question, please feel free to contact us.
Best regards,
Hannah Xiong

