@Yann Greder
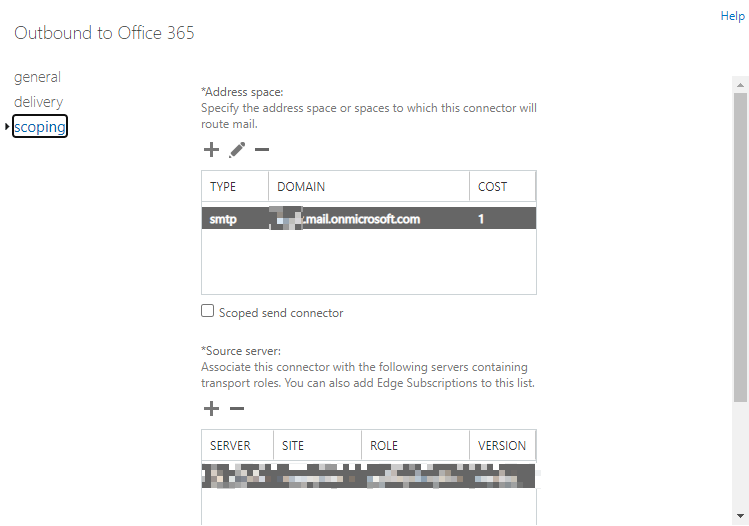
The connector created by HCW is only used when sending email to the email address for your Office 365 (yourdomain.mail.onmicrosoft.com):
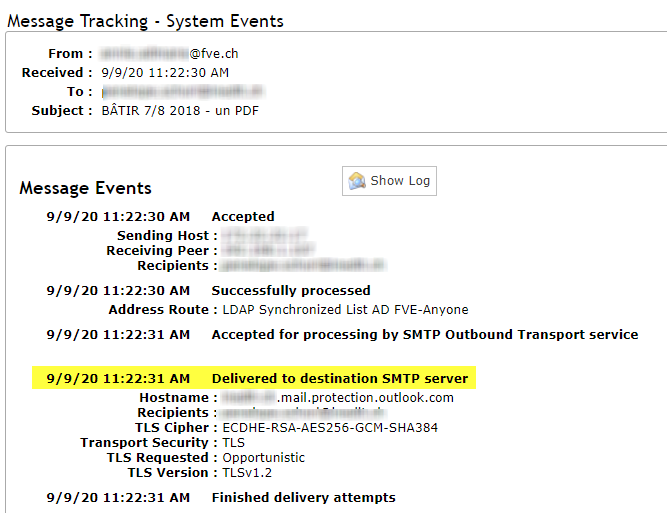
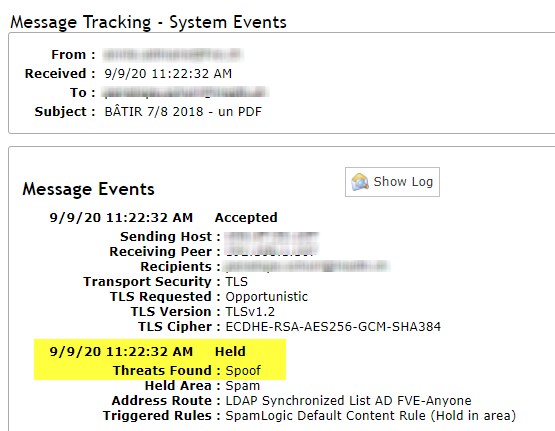
According to your description, you can successfully send email after disabling this connector, so I think you try to send email to Exchange online mailbox hosted on your Office 365 tenant. Could you send email to other tenant's Exchange online mailbox?
If you could send email to other tenant's Exchange online mailbox successfully, I think this issue is caused by the mail filter tool that you used. From this article we can know that don't place any filter tool between Exchange on-premises and Exchange online:
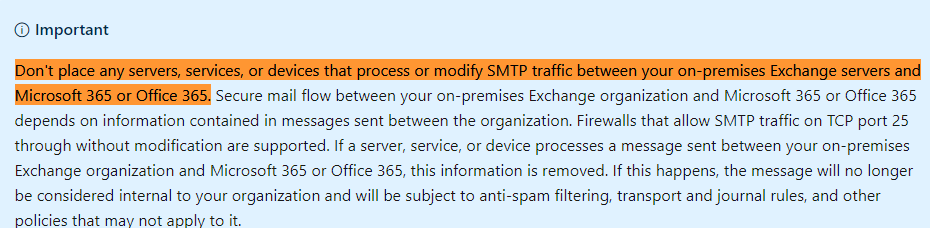
Check your filter tool and the connector created by HCW to ensure that email is delivered directly from Exchange on-premise to Exchange online.
If the response is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.